
Release Notes for WS_FTP Server 7.5.1.2, WS_FTP Server 7.5.1.2 with SSH, and WS_FTP Server 7.5.1.2 Corporate
In this File
About this document
This document contains information on how to install and configure WS_FTP Server, WS_FTP Server with SSH, and WS_FTP Server Corporate. Depending on which WS_FTP Server product you have purchased, portions of this document may not apply.
The document also describes how to install and configure add-on modules for the WS_FTP Server and WS_FTP Server with SSH.
What is WS_FTP Server?
Ipswitch WS_FTP® Server is a highly secure, fully featured and easy-to-administer file transfer server for Microsoft Windows® systems. WS_FTP Server lets you create a host that makes files and folders on your server available to other people. Users can connect (via the Internet or a local area network) to your host, list folders and files, and (depending on permissions) download and upload data. Administrators can control access to data and files with granular permissions by folder, user, and group. Administrators can also create multiple hosts that function as completely distinct sites.
WS_FTP Server is proven and reliable. It is used by administrators globally to support millions of end users and enable the transfer of billions of files.
WS_FTP Server complies with the current Internet standards for FTP and SSL protocols. Users can connect to the server and transfer files by using an FTP client that complies with these protocols, such as Ipswitch WS_FTP Home or Ipswitch WS_FTP Professional.
WS_FTP Server with SSH also includes support for SFTP transfers over a secure SSH2 connection.
Our product offerings are described in WS_FTP Server product family.
Administration
- Fully web-based administration for remote management
- Enhanced logging and reporting
- Connection port configurable by host
- Event-driven communication and automation
Performance
- Proven and reliable: Used by administrators globally to support millions of end users and enable the transfer of billions of files
- Failover architecture
Security and Compliance
- File integrity checking support
- Full support for file transfer using SFTP over SSH
- Implicit and explicit SSL support with up to 256 AES encryption
- Auto-expiring passwords and enhanced password controls
- Ability to hide login banner from client
WS_FTP Server Product Family
The WS_FTP Server product family provides a broad range of file transfer functionality, from fast file transfer via the FTP protocol, to secure transfer over SSH, to a complete file transfer (server/client) solutions.
- WS_FTP Server: Our base product offers fast transfer via the FTP protocol with the ability to encrypt transfers via SSL, and includes FIPS 140-2 validated encryption of files to support standards required by the United States and Canadian governments.
WS_FTP Server can operate standalone or is easily integrated with existing user databases (Active Directory, Windows NT, Ipswitch IMail, ODBC). Web-based administration provides remote management of the server and can use our integrated web server or Microsoft IIS.
When used with our WS_FTP Professional client, WS_FTP Server can retry a failed transfer, perform file integrity checks, verify a user's identity, and speed transfers by using compression and multi-part transfers.
WS_FTP Server is designed with a tiered architecture that allows components and data to be maintained on one computer or distributed among several.
WS_FTP Server can be deployed in an active-passive failover configuration that uses shared resources for the user database, configuration data, and the file system for user directories and log data.
- WS_FTP Server with SSH: This product offers all of the features of WS_FTP Server plus the ability to send and receive files over SSH, which automatically delivers encrypted communications during and throughout file transport.
- WS_FTP Server Corporate: This product extends the secure transfer capabilities of WS_FTP Server with SSH to provide:
- Support for SCP2 to provide a secure version of the remote copy capability used in UNIX applications
- LDAP support for authentication to leverage existing corporate databases.
- A complete file transfer solution (server and client) by integrating the WS_FTP Server Web Transfer Module.
- WS_FTP Server Web Transfer Module
The WS_FTP Server Web Transfer Module, an add-on to WS_FTP Server products, enables users to transfer files between their computers and company servers over HTTP/S using a Web browser. As a result, employees and external business partners can connect to company networks simply and securely to share files, data, and other critical business information.
- WS_FTP Server Ad Hoc Transfer Module
The WS_FTP Server Ad Hoc Transfer Module, an add-on to WS_FTP Server products, lets users send files from their computers to one or more individuals by sending an Ad Hoc Transfer message via email. Recipients of an Ad Hoc Transfer "package" can connect to a download page, hosted on the WS_FTP Server, and download the files that have been "sent" to them. This module lets your users send a secure transfer to colleagues and clients, without the need to set up temporary accounts.
Users can send a package by using the Ad Hoc Transfer web interface or Microsoft Outlook.
New in 7.5.1
Version 7.5.1 introduces failover support to the WS_FTP Server family of products. You can now deploy WS_FTP Server on a two-node failover cluster in a Windows Server environment using Microsoft Cluster Services (MSCS) or Microsoft Network Load Balancing (NLB). The failover solution consists of one "active" and one "passive" node, each running identical configurations of WS_FTP Server. If the primary node is unavailable, or if a server (FTP or SSH) is unavailable on the primary node (MSCS only), processing switches over to the secondary node. This two-node configuration uses shared resources for the user database, configuration data (SQL Server), and the file system for user directories and log data.
Version 7.5.1 also includes multiple SSH improvements:
- Users are now able to use multiple SSH user keys to authenticate to SSH servers.
- Administrators can require multiple authentication factors (password and SSH user key) for users authenticating to an SSH server.
New in 7.5
Version 7.5 introduces the Ad Hoc Transfer capability to the WS_FTP Server family of products. Ad Hoc Transfer lets your users send file transfers to an individual, rather than to a folder or file transfer site. Files can be sent to any valid email address, meaning you do not have to maintain accounts for all recipients, or set up temporary accounts.
Files sent via Ad Hoc Transfer are stored in a folder on the WS_FTP Server computer. Recipients receive a notification in their email inbox, and click on a web link to access the posted files.
As the administrator, you can set options that require Ad Hoc Transfers to be password protected, and to manage the size and availability of an Ad Hoc Transfer "package," which is the user-generated email message plus associated files.
The Ad Hoc Transfer Module provides two ways for a WS_FTP Server user to send a transfer:
- The Ad Hoc Transfer Module web interface: Users can open this interface in their web browser to send a file transfer "package" and view recently sent packages. You can set the options, such as password protection and notification on delivery, that are available to users. You provide to users the web address that they will use to access Ad Hoc Transfer Module. No installation is required on the user's computer.
- Microsoft Outlook: Users can send a file transfer "package" by creating a new message in Outlook, attaching the files, and selecting Send Secure (rather than Send). You can set the options, such as password protection and notification on delivery, that are available to users. Users will need to install the Ad Hoc Transfer Plug-in for Outlook.
New in 7.1
Version 7.1 includes the following new features:
- Support for Windows 2008. You can now install WS_FTP Server and each of its features on a Windows 2008 Server. The install will activate several Windows 2008 roles and features (see the WS_FTP Server Getting Started Guide for details). WS_FTP Server is compatible with 32 and 64-bit versions.
- VMWare ESX (32-bit) Support. You can now install WS_FTP Server on virtual machines you have hosted on ESX servers.
- New Email Notification Variables. There are now new variables that you can use to trigger notification emails. Notification variables now include transfer type ("ASCII" or "Binary"), IP addresses of clients performing an action, the server host of a user attempting an action, and the size of a file uploaded or downloaded.
- SMTP Authentication. WS_FTP Server now supports authentication for SMTP servers. If you activate SMTP Authentication in WS_FTP Server Manager, when connecting, the server will submit the username and password you entered.
New in 7.0
Version 7 introduces a third product offering, WS_FTP Server Corporate, to the WS_FTP Server family of products. WS_FTP Server Corporate offers a convenient way to purchase the full range of secure, managed file transfer functionality that we provide. For a description of each of the WS_FTP Server product offerings and the major features included, see WS_FTP Server Product Family.
Version 7 is a major release that includes the following new features:
- Blocking of IP addresses that attempt multiple concurrent connections.
The IP Lockouts feature is designed to thwart dictionary attacks, which can shut down a server by flooding it with connection requests. WS_FTP Server can monitor connection attempts, identify possible abuse, and deny access to the FTP and SSH servers for the offending IP address.
The IP Lockouts feature lets the administrator set the criteria for blocking an address (or subnet range), manually add an approved address to the whitelist, or manually add a problem address to the blacklist.
From the Server Manager, select Server > IP Lockouts.
- Support for LDAP databases for user authentication (with failover) to leverage existing corporate databases.
WS_FTP Server supports standard implementations of LDAP, including Microsoft's Active Directory, OpenLDAP, and Novell's eDirectory. Administrators can configure a WS_FTP Server host to use an LDAP database for the user database. Failover to a secondary LDAP database is supported, and communications are secured via SSL.
The LDAP user database option is selected from the Create Host page. Selecting Configure opens the LDAP Configuration page.
- Support for Secure Copy (SCP2) transfers, to provide a secure version of the remote copy capability used in UNIX applications. (WS_FTP Server Corporate)
WS_FTP Server supports SCP2 protocol (i.e. SCP over SSH2), which leverages SSH to provide authentication and secure transfer. In addition, the WS_FTP implementation of SCP2 has the benefit of leveraging any users, rules, and notifications created for the WS_FTP server host. For an SCP client, users can use either OpenSSH or PuTTY SCP.
The Enable Secure Copy (SCP2) is on the Edit Listener page when you select an SSH listener.
- FIPS 140-2 validated encryption of files, to support standards required by the United States and Canadian governments. (WS_FTP Server Corporate)
FIPS 140-2 sets a standard for encoding data (cryptography) that is required of many military and government organizations. WS_FTP Server provides FIPS 140-2 validated ciphers to encrypt file transmissions. The administrator can enable FIPS mode for the FTPS and SSH services.
FIPS mode does not apply to FTP and HTTP services. FIPS mode ensure that all secure listeners use FIPS 140-2 validated cryptographic algorithms. If you use the default WS_FTP Server certificate, you will have to create a new certificate.
The Operate in FIPS 140-2 Mode option is on the System Details page.
- Updated home folder options: A new user option to Show home folder as root can hide the directory path to the user's home folder. This option is used with the Lock user to home folder option to improve security of user folders. Both options are on the Edit User page when you select an individual user. To set either option to apply to all users, use the iftpaddu program, found in:
- 32-bit:
C:\Program Files\Ipswitch\WS_FTP Server - 64-bit:
C:\Program Files (x86)\Ipswitch\WS_FTP Server
- 32-bit:
- SSH User Level Key Management: SSH user keys can be imported and exported to and from Windows, Unix and Linux systems. You can now import OpenSSH keys in the same way as you would other types of SSH keys.
- Enhanced SSL Certificate Support: The WS_FTP Server Trusted Authorities database now supports SSL certificate chains containing either the full chain or just the peer level certificate. Also, SSL Certificates now support more than 2 characters for the State/Province.
- SSH Listener Options: Support for suppressing the server identification and version (WS_FTP_SSH_7.0) from being displayed on the login banner, preventing users from attempting malicious actions on the SSH server based on the server identification and version.
- Notification variables: Added %emailaddress variable, which returns the email address of the user that attempted the action.
- License Activation Support: During installation, if an install executable does not have an active license, a license dialog will prompt the user for a serial number, MyIpswitch username, and password. A license activation shortcut will also be available in the Windows Start Menu (Programs > Ipswitch WS_FTP Server > Activate or Refresh WS_FTP Server License), so that the user can activate a license after installation.
System requirements for WS_FTP Server
Tip: If a listed requirement is hyperlinked, you can click the link to get more information on obtaining and installing that prerequisite.
WS_FTP Server
Supported Operating Systems
For a standalone WS_FTP Server installation:
Operating System |
Edition |
Service Packs |
Supported Versions |
Windows Server 2008 |
|
SP2 or later |
|
Windows Server 2008 R2 |
|
|
|
Windows Server 2003 |
|
SP2 or later |
|
Windows Server 2003 R2 |
|
|
|
Windows XP |
|
SP3 or later |
|
For a WS_FTP Server failover cluster using Microsoft Clustering Services:
Operating System |
Edition |
Service Packs |
Supported Versions |
Windows Server 2008 |
Enterprise |
SP2 or later |
32-bit: English |
Windows Server 2008 R2 |
Enterprise |
|
64-bit: English |
For a WS_FTP Server failover cluster using Microsoft Network Load Balancing:
Operating System |
Edition |
Service Packs |
Supported Versions |
Windows Server 2008 |
|
SP2 or later |
|
Windows Server 2008 R2 |
|
|
|
Windows Server 2003 |
|
SP2 or later |
|
Windows Server 2003 R2 |
|
|
|
System Requirements
- Microsoft .NET Framework 2.0
If you plan to install the WS_FTP Server Web Transfer Module, you will need to also install Microsoft .NET Framework 3.0.
- ASP.NET (via IIS) and .NET 3.0 or 3.5 for Web Transfer Module, Ad Hoc Transfer module, and WS_FTP Server Corporate
- Broadband connection to the Internet (recommended)
- During installation, you can select Microsoft Internet Information Services (IIS) as your web server (instead of WS_FTP's Web Server). If you choose this option, you need to have Microsoft Internet Information Services (IIS) 5.0 or later installed on your computer.
- The default database for configuration data is PostgreSQL 8.3.12 (local only).
- During installation, you can select Microsoft SQL Server as your database for configuration data. If you choose this option, you must use one of the following versions:
- Microsoft SQL Server 2005 Express or Standard versions (local or remote)
- Microsoft SQL Server 2008 Express, Standard, or Enterprise versions (local or remote)
Required Hardware
- An Intel Pentium® 4, 1 GHz or higher (or an equivalent processor)
- 512 MB RAM minimum
- 250 MB of drive space
- NTFS formatted drive
- TCP/IP enabled network interface card (NIC)
- Other minimum OS requirements
Virtualization Requirements
- VMware ESX 3.5 and 4.0 (32-bit and 64-bit guest operating systems)
- Microsoft Hyper-V 1.0 on Windows 2008 64-bit (32-bit and 64-bit guest operating systems)
Ipswitch Notification Server
All requirements for WS_FTP Server (above), plus:
- Broadband or dial-up connection to the Internet (required for email notifications sent from outside of the local area network)
- Modem and phone line required for pager and SMS notifications (optional)
Ipswitch Notification Server is a part of WS_FTP Server and is typically installed on the same machine as the original software by the original package.
WS_FTP Server Manager
Server Requirements:
- WS_FTP's Web Server (included in installation package) or Microsoft Internet Information Services (IIS) 5.0 or later.
Client Requirements:
- Microsoft Internet Explorer 6 or later, Mozilla Firefox 3.6 or later, Google Chrome 4 or later, Apple Safari 3.2.3 or later
- Enabled Javascript support in the Web browser
- Enabled Cookie support in the Web browser
WS_FTP Server Server Manager is a part of WS_FTP Server and is installed on the same machine as the original software by the original package.
Installing WS_FTP Server on Windows 2008 Server
The WS_FTP Server installer automatically activates certain components in your Windows 2008 installation. This is necessary because after installation, Windows 2008 does not turn on non-core operating system components. However, before installing WS_FTP Server, you should be sure that these changes conform to your organization’s security policies.
When you install WS_FTP Server, the install activates the following 2008 Server roles:
- ISAPI Extensions
- Windows Authentication
- ASP
- Note: If you are installing the WS_FTP Server Web Transfer Module on Windows 2008, there are additional components activated. See "System requirements for WS_FTP Server Web Transfer Module" below.
Upgrade notes
Upgrading a license to add a feature(s)
If you are upgrading an existing WS_FTP Server 7 license, use the following procedure. Upgrading an existing license includes the following:
- Upgrading from an evaluation license to a full license
- Adding a feature(s) to an existing license, for example, adding the Ad Hoc Transfer Module, or upgrading to WS_FTP Server Corporate
- Purchase the feature.
- Click Program Files > Ipswitch WS_FTP Server > Activate or Refresh WS_FTP Server License. The Ipswitch Product Activation program opens.
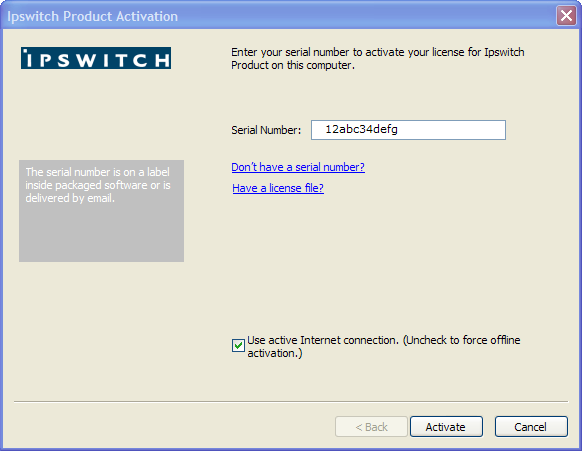
Note that your serial number should appear in the Serial Number box. If it does not appear, please enter it.
- Click Activate to upgrade your license.
Your license will be upgraded to include the new purchased feature. This upgrade process does not create a second activation of the product, it just updates the existing license.
Upgrading from WS_FTP Server 6
- Make a backup of your existing server before starting the installation program. The WS_FTP Server 7.x installation program makes changes to your database that will not work with previous versions of WS_FTP Server. We recommend that you back up your database so you retain the option of reverting to the previous version. To back up a PostgreSQL database, see the Knowledge Base article on how to back up WS_FTP Server 6+. To back up a SQL Server database, see your SQL Server documentation.
- If the WS_FTP Server installation uses PostgreSQL, you must install Microsoft .NET Framework 3.5 when upgrading to WS_FTP Server 7.5.1 from previous versions of WS_FTP Server, otherwise the installer will not let you complete the upgrade.
- If you are upgrading from WS_FTP Server 6.x (with FTP only, no SSH) to WS_FTP Server with SSH 7, the SSH Listener is not created by the installation program. When the installation program completes, you need to log on to the WS_FTP Server Manager, select Listeners, and create the SSH listener.
Installing WS_FTP Server
Important:If upgrading from a previous version of WS_FTP Server, before running the installation program, see the section on upgrades.
During the installation, a host using the internal WS_FTP Server user database is created. You can create hosts using Microsoft Active Directory, Microsoft Windows, or other external user database types after the install is completed.
Important: Installing WS_FTP Server on a domain controller is not recommended.
Important: Installing WS_FTP Server via Terminal Services is not recommended. You can use Terminal Services to install subsequent WS_FTP Server updates and installations.
Note:If you are installing on Windows 2008 Server, a command window may display and pause at various points during install. These pauses may last a minute or longer and are an expected part of the product installation.
To install WS_FTP Server:
- If you are using Microsoft IIS as your web server, before you begin the WS_FTP Server installation, confirm that Microsoft IIS is running and that you can access the Web site on which you will install the WS_FTP Server Manager web application.
- If you received an installation CD, insert it into a drive. If the Welcome screen does not appear, select Start > Run, and enter the drive path followed by launch.exe.
Example: D
:\launch.exe- OR -
If you downloaded the software from our Web site, double-click the executable (.exe) file to begin the installation.
- On the installation Welcome screen, click Read to read the release notes or View to download and view an electronic copy of the Getting Started Guide. Click Next to continue. The License Agreement dialog appears.
- Read the license agreement carefully. If you agree to its terms, select I accept the terms of the license agreement and click Next. The Setup Type dialog appears.
- The Setup Type dialog lets you select from two installation methods, Express and Custom.
- Express installs the WS_FTP web server and installs the following components to default locations: WS_FTP Server or WS_FTP Server with SSH, Ipswitch Notification Server, Ipswitch Logging Server, and PostgreSQL. The option to install WS_FTP Server with a Microsoft IIS web server, or with a SQL Server database, will not be available with express install.
- Custom installation allows you to select the specific components you want to install and also specify locations for each component install. Custom install also allows you the option of using a Microsoft IIS web server and/or MS SQL Server database.
- Select the installation method you want to use, then click Next.
To use the express install option:
Important:The express installation option does not include the option of installing WS_FTP Server with Microsoft IIS as the web server for WS_FTP Server Server Manager, or Microsoft SQL Server as your database. If you wish to run WS_FTP Server with IIS or SQL Server, click the back button and choose the Custom install option.
- If you are installing on Windows 2008, you will first see the Enable Ports dialogue. Selecting Yes will configure the Windows firewall to allow incoming connections from the FTP and SSH services. (If you select No, you will still be able to configure the firewall manually later.)
- Enter the port that your WS_FTP Web Server will use for WS_FTP Server Server Manager. (The install will verify that the port is not in use.) Click Next.
- Verify or enter the fully qualified host name for this server. The installation program provides the host name of the server, but you may need to add domain information. This host name is used to create the first host.
- When you click Next, one of the following screens opens:
- Specify a PostgreSQL Server and Administrator Account. This screen opens if PostgreSQL database server was previously installed on your computer. Go to step 4.
- Create User Accounts. Continue to step 5.
- In the Administrator Password box, enter a System Administrator Password for access to the system administrator (sa) account for the PostgreSQL database that hosts WS_FTP Server data. Click Next. The Enter Host Name screen opens.
- The Create User Accounts screen opens. Set the appropriate options.
- Create the WS_FTP Server system administrator account on this host. Select the host on which you want to create a system administrator account. If you are installing for the first time, only one host is available.
- Username. Enter a username. This username is used to create:
- a WS_FTP Server user to serve as the system administrator. This user belongs to the specified host, but is granted full system administrator permissions for all hosts on the server.
- a non-privileged Windows user account named
IPS_plus the name you provide. For example, if you enteradmin, the Windows user is namedIPS_admin. This account is used by the configuration data store (PostgreSQL) and serves as the run-as user for theWSFTPSVRvirtual folder.
- Password and Confirm Password. Enter and confirm a password. This password is assigned to both the WS_FTP Server system administrator user and the Windows user account.
Important: Your domain password policy may require that you use complex password rules. If so, make sure that you use a password that conforms to the domain requirements. The account will not be created without conforming to the domain password requirements.
- Click Next. The Ready to Install the Program screen opens.
- The install program is now ready to install the components you selected. Click Install. The install program installs and configures the components you selected. This may take a few minutes.
- If you do not have an active product license, the License Activation dialog will appear. See "Activating WS_FTP Server for New or Upgraded Licenses" below for details.
- Click Finish to complete the installation.
To use the custom install option:
- If you are installing on Windows 2008, you will first see the Enable Ports dialogue. Selecting Yes will configure the Windows firewall to allow incoming connections from the FTP and SSH services. (If you select No, you will still be able to configure the firewall manually later.)
- The Select Features screen opens. Select the checkboxes next to the components you want to install. Click Next.
- Choose the database you wish to use for WS_FTP Server: PostgreSQL or Microsoft SQL Server (you will be asked for configuration values later in the install).
- For each component that you selected, confirm the Destination Folder where the install program will install the component. To choose a new folder, select Browse and choose another folder. After you have made your selection, click Next. Repeat this step for each component (including the database components). When the destination folder for each component has been selected, the Select Web Host screen appears.
- Select the web server that you will use with WS_FTP Server. (If you select Microsoft IIS, be sure that IIS is running on the PC that you are installing to.) Click Next.
- If you chose the PostgreSQL database, enter the port that your WS_FTP Web Server will use. (The install will verify that the port is not in use.) Click Next.
- Next, enter the fully qualified host name for this server. The installation program provides the host name of the server, but you may need to add domain information. This host name is used to create the first host.
- When you click Next, one of the following screens appears:
- Specify a PostgreSQL Server and Administrator Account. This screen opens if PostgreSQL database server was previously installed on your computer. Go to step 8.
- Create User Accounts. Continue to step 9.
- In the Administrator Password box, enter a System Administrator Password for access to the system administrator account for the PostgreSQL database that hosts WS_FTP Server data. Click Next. The Enter Host Name screen opens.
- The Create User Accounts screen opens. Set the appropriate options.
- Create the WS_FTP Server system administrator account on this host. Select the host on which you want to create a system administrator account (if you are using WS_FTP Server). If you are installing for the first time, only one host is available.
- Username. Enter a username. This username is used to create:
- a WS_FTP Server user (if applicable) to serve as the system administrator. This user belongs to the specified host, but is granted full system administrator permissions for all hosts on the server.
- a non-privileged Windows user account named
IPS_plus the name you provide. For example, if you enteradmin, the Windows user is namedIPS_admin. This account is used by the configuration data store (PostgreSQL) and serves as the run-as user for theWSFTPSVRMicrosoft IIS virtual folder (if you use Microsoft IIS).
- Password and Confirm Password. Enter and confirm a password. This password is assigned to both the WS_FTP Server system administrator user (if applicable) and the Windows user account. Click Next.
Important: Your domain password policy may require that you use complex password rules. If so, make sure that you use a password that conforms to the domain requirements. The account will not be created without conforming to the domain password requirements.
Important: The Windows user account must comply with the security policies on your Windows server. Once the install completes, verify that the account is not set to expire at the next logon and that you are aware of any expiration policies that apply to the account.
- If you chose Microsoft SQL Server for your database (in step 2), next you will be asked to enter the Server's name or IP address with the instance name (formatted as Server/Instance), a Port number (the install autofills SQL Server's default value of 1433), the Master Database Username, and Password. Click Next.
- If you chose Microsoft IIS as your web server, the Web Configuration screen opens. In the Use this Web site dropdown, select the preferred Internet Information Services (IIS) Web site. Click Next.
- The Ready to Install the Program screen opens, which will install the components you selected. Click Install. This may take a few minutes.
- If you do not have an active product license, the License Activation dialog will appear. See "Activating WS_FTP Server for New or Upgraded Licenses" below for details.
- Click Finish to complete the installation.
Activating WS_FTP Server for new or upgraded licenses
There are four ways you can make a WS_FTP Server installation active:
- If you installed WS_FTP Server using an installation application downloaded from a link in a purchase confirmation email, then the program will be fully functional immediately after installation. No further action will need to be taken.
- If you downloaded the installation application from another source, when you run the installation, it will automatically ask you for your license serial number and attempt to activate.
- If the WS_FTP Server license is not activated during installation, or if you are upgrading from a previous WS_FTP Server version, you can manually activate WS_FTP Server (see below).
- If for some reason you cannot activate your license via Internet connection, you can opt for an offline activation. To force offline activation, on the Activation screen, clear the check mark for Use active Internet connection. You will then need to go to www.myipswitch.com, click on Offline Activation, and follow the instructions displayed.
To manually activate the license on an existing installation:
Note: Before you start the manual activation process, make sure that you have your product serial number, MyIpswitch account name, and password available for use during activation.
- Click Start > Programs > Ipswitch WS_FTP Server > Activate or Refresh WS_FTP Server License.
- or -
- If you run the WS_FTP Server installation, near the end, it will display a License dialog. Enter your serial number and click Activate to start the license activation process.
Follow the on-screen instructions, entering your product serial number, MyIpswitch account name, and password.
Note: When the activation is complete, a confirmation page indicates the license has been activated. If the activation does not complete successfully, you may be behind a proxy or firewall that is blocking the activation request. In this case, click the Offline button, then follow the onscreen instructions.
For more help and information about licensing, go to the MyIpswitch (www.myipswitch.com) licensing portal.
Fixed in 7.5.1.2
The following issue was addressed in V7.5.1.2:
- Fixed an issue in V7.5.1 where SSH and FTP server services stop accepting connections after receiving a network error. The SSH or FTP server stopped receiving new connections when it received this network error:
10054 Network ErrorFailed to accept client connection: An existing connection was forcibly closed by the remote host.Users would restart the server service before it started to accept new connections.
Fixed in 7.5.1
The following issues were addressed in V7.5.1:
- Fixed a security vulnerability where an attacker could exploit a cookie vulnerability to expose passwords for the Server Manager, Web Transfer Module, and Ad Hoc Transfer module web interfaces.
- Fixed issue where administrators were unable to save changes to a user's home folder path when it was entered manually in the Server Manager.
- Idle sessions were not closing in WS_FTP Server. The server now closes sessions that have been idle for the specified timeout period. Administrators can also terminate idle sessions from the Session Manager page in the Server Manager.
- Silent uninstall of WS_FTP Server has been changed to silently deactivate the server license, even if there is no network connectivity. This will prevent an offline deactivation pop-up window.
- Internet Explorer 8 displayed error messages when viewing help files for Ad Hoc Transfer module and Web Transfer Module. Fixed Javascript errors in the English and German help systems for both the modules.
- Users now see explanatory messages and detailed messages are now written to the system log when uploads fail while sending Ad Hoc Transfer packages due to impersonation account errors.
If the impersonation account is incorrectly configured, the user sees the message "Send files failed - data access error, contact system administrator." If the impersonation account does not have permissions to read and write to the folder where Ad Hoc Transfer packages are stored, the user sees the message "Send files failed - system account error, contact system administrator."
- Documentation updated to support backup utilities on 64-bit systems. See Maintaining the Server for more information.
- In WS_FTP Server Manager Help, "Removing users from groups" no longer appears as "Adding Users to a User Group."
- Upgraded PostgreSQL to 8.3.12 to eliminate security vulnerabilities from previous versions.
- Upgraded zlib to 1.2.5 to fix some bugs and implement some security enhancements. See http://www.zlib.net for more information.
- Fixed bug where some SFTP clients cannot retrieve a directory listing if the folder contains paths or files with filenames that contain special UTF-8 characters such as French characters (like é, à or ô) or German characters (like ä, ë, or ö).
- The certificate import utility
certimport.exehas been reintroduced in V7.5.1. It can be found in:- 32-bit:
C:\Program Files\Ipswitch\WS_FTP Server\Utilities - 64-bit:
C:\Program Files (x86)\Ipswitch\WS_FTP Server\Utilities
- 32-bit:
- Fixed bug in the Ad Hoc Transfer module that caused AHT to become inaccessible after reinstalling AHT with the Repair option.
Fixed in 7.5
- Fixed a defect that caused notification variables (%Dir,%File, %ToFile and %FmFiles) to not display the correct file path when executed from a folder action rule on a virtual folder.
- Fixed a defect in v7.1 that caused %File and %Dir notification variables to not work.
- Fixed a defect in v7.1 that caused downloads via the Web Transfer Module to fail when the files were on a network (UNC) drive.
- Fixed a defect that caused the SSH server service to stop accepting connections due to the incoming packet size setting in the SSH client.
Fixed in 7.1
The following issues were addressed in 7.1:
- Users upgrading from versions 5 to 7 or 6 to 7 were getting error messages (“Error 1053”). This was due to a problem in the Ipswitch licensing system, which was resolved for 7.1.
- Some clients on non-Windows OSs had problems connecting to WS_FTP Server. This was due to a problem with a newly-introduced security feature and was resolved.
- Tumbleweed and other clients using the JScape SSH Factory for .NET were getting errors when connecting to WS_FTP Server. The new version of Server has been modified to fix this problem.
- In WS_FTP Server Manager, when creating a SITE command, the system failed to save when double quotes were used in the path. This problem was corrected for 7.1.
- In WS_FTP Server Manager, some users were seeing multiple passwords reset at the same time when individual users took the action of resetting their password. A fix included in 7.1 addressed this problem.
- When you use the "Show home folder as root" option, the PUT / STOR commands to move files to subfolders were not working. All commands now work as expected.
- After a period following installation, users were not able to log into the WS_FTP Web Client. This was due to a problem setting permissions on folders. This problem was addressed for 7.1.
- In some cases, notifications were not triggered for files upload via the Web Client. This had do to with OS level permissions in specific folders, and has been resolved.
- FTP sessions, in certain cases, were failing with "unsupported SFTP feature" errors when
STAT /commands were issued. This has been addressed. - When shutting down WS_FTP Server on the Windows 2003 OS, some users were receiving runtime errors. This was corrected.
- In some cases, on WS_FTP Server 7.0, when you configured two hosts with two separate domains using LDAP, the separate configurations were not successfully saving, and appeared as identical. This has been fixed.
- WS_FTP Server's Web Admin application had several cross-site scripting (XSS) vulnerabilities of low to moderate severity in versions 6.x and 7.0. These could allow remote attackers to inject arbitrary web script or HTML into pages of the web-based administration interface. These have all been addressed. (Thank you to Paul Hand, CEH for bringing these to our attention.)
Fixed in 7.0
The following issues were addressed in this release:
- WS_FTP Server: SSL Certificates now support more than 2 characters for the State/Province.
- WS_FTP Server: Linux/Unix public keys can now be imported successfully.
- WS_FTP Server: Fixed a defect that caused an SSH connection attempt to fail for some clients and displayed the message “Bad remote protocol version identification: 'SSH-2.0' "
- Web Transfer Module: Fixed a defect that caused the installation to fail (and display a 1720 error) when installing the WS_FTP Server Web Transfer Module on a 64-bit Windows operating system.
- Web Transfer Module: Fixed a defect that caused a failed download if the selected file's name had been truncated in the display.
- Web Transfer Module: Fixed a defect that caused a download of a file with a Chinese file name to fail. The IE and Firefox browsers can now support a multi-byte character set filename, though the Safari browser cannot.
Fixed in 6.1.1
The following issues were addressed in this release:
- The "TLS Only" option allowed connections using SSL v2, but would reject the connection during the login attempt. "TLS Only" now rejects connections during SSL negotiation.
- Clients with SSL session reuse and mutual authorization activated (requiring a client certificate) failed during second attempts to connect to the server. This problem has been fixed.
- File transfers were keeping files locked when network connections were suddenly dropped. This problem has been addressed by including a Data Channel Timeout for listeners.
Ipswitch would like to thank Secunia (secunia.com) for reporting the following issues, which have been fixed in this release:
- [SA28753] SSH Server Denial of Service vulnerability: A boundary error in the SSH Server Service could be exploited by passing an overly long argument to a command.
- [SA28822] The WS_FTP Server Manager log viewer vulnerability: HTTP requests for the FTPLogServer/LogViewer.asp script could be exploited allowing unauthorized log access.
- [SA28761] WS_FTP Server Denial of Service vulnerability: Overly large datagrams sent within a short time period could cause the log service to stop responding to log requests.
Fixed in 6.1
The following issues were addressed in this release:
- You can now generate an SSL certificate that uses the full State name (Georgia, Florida, etc), which is required when validating a CSR with Verisign. The previous release used a 2-letter abbreviation for State names.
- Fixed a defect that caused the WS_FTP Server Manager to display page errors (for the Host pages) when NTFS compression was used with folders on an FTP site. This also fixes the error seen when a client attempted to retrieve a directory listing of compressed folders.
- Using the MLSD command to display a directory listing in an FTP client caused the Modified date and time to be displayed incorrectly. It now displays correctly.
- When upgrading from 5.04, and using Internet Explorer to browse folders, some customers saw an invalid time stamp displayed for the file modified date. Time stamps now display correctly.
- When issuing a Port command using a script, if a leading zero was used (for example, 010), the Port command would fail. Leading zeros are now accepted in the Port command.
Ipswitch would like to thank Secunia (secunia.com) for reporting the following issues, which have been fixed in this release:
- [SA26529] WS_FTP Server Script insertion vulnerability: Parameters passed to valid FTP commands could insert arbitrary HTML and script code.
- [SA26040] WS_FTP Log Server Denial of Service vulnerability: An error within the WS_FTP Log Server (ftplogsrv.exe) could be exploited to crash a server.
Release notes
OpenSSL conflicts when installing WS_FTP Server V7.5.1
The WS_FTP Server 7.5.1 installation program installs a new version of the OpenSSL library. The new version, OpenSSL 0.9.8p, is required and gets installed to the installation folder (the default is: C:\Program Files\Ipswitch\WS_FTP Server).
If the installation program finds a version of the library in the Windows system folders, it will stop the installation and ask you to move or rename the library files. If these library files are used by other programs, you want to make sure that you retain a copy of them. We suggest you create a backup in another folder, or rename these files, then remove the files from these locations:
32-bit OS |
64-bit OS |
C:\Windows\libeay32.dll |
C:\Windows\libeay32.dll |
C:\Windows\ssleay32.dll |
C:\Windows\ssleay32.dll |
C:\Windows\system32\libeay32.dll |
C:\Windows\SysWOW64\libeay32.dll |
C:\Windows\system32\ssleay32.dll |
C:\Windows\SysWOW64\ssleay32.dll |
C:\Users\[username]\Windows\libeay32.dll or |
C:\Users\[username]\Windows\libeay32.dll or |
C:\Users\[username]\Windows\ssleay32.dll or |
C:\Users\[username]\Windows\ssleay32.dll or |
Upgrading WS_FTP Server V7.5 to V7.5.1 (PostgreSQL)
When upgrading a WS_FTP Server installation that uses a PostgreSQL database from V7.5 to V7.5.1, you must install Microsoft .NET framework 3.5 or 3.5 SP1 before running the installer to upgrade, otherwise the installer will halt the installation.
IP Lockouts do not carry over failed logon attempts after cluster failover
When a cluster fails over from node 1 to node 2, the number of failed logon attempts does not carry over to node 2. Therefore, the server does not lock out the user even if the failed logon count is cumulatively greater than the limit set by the IP Lockouts rule since the failed logon count per node is less than the IP Lockout rule allows. Once a user fails a number of logons on a single node equal to the IP Lockouts limit, then the user is locked out.
For example, assume a user account’s IP Lockouts rule is set to blacklist the user after 5 failed attempts. If a user fails to log on 3 times while node 1 is the active node and then the cluster fails over, the user will have to fail 5 more log on attempts on node 2 in order for WS_FTP Server to blacklist the user because the failed attempts do not transfer between nodes.
Currently, there is no work around for this issue.
See IP Lockouts do not carry over failed logon attempts after cluster failover in the Ipswitch Knowledge Base for more information.
Unhandled exception when using AHT and switching nodes after a failed send
When a cluster fails over from node 1 to node 2 while an Ad Hoc Transfer user attempts to send a package from the AHT site, the file transfer fails, the user is logged out, and the browser displays the Microsoft error "Internet Explorer cannot display the webpage." After node 2 becomes the active node, users attempting to log on to the AHT site again receive an error message about an unhandled exception.
To resolve this issue, the user must restart the browser session before logging back onto the site. Then the user can send packages normally.
See An unhandled exception when using AHT and switching nodes after a failed send in the Ipswitch Knowledge Base for more details and the content of the exception.
Unable to resume transfer or delete file after failover
When a cluster fails over from node 1 to node 2 during an upload, the transfer fails and the file transfer client‘s connection to the cluster drops (the message is "Connection is dead"). The upload does not resume when the user logs back into the server. Although the partially uploaded file is present, it cannot be deleted. This is caused by the share host (Windows UNC or Linux NAS) holding an open handle for node 1 on the partially uploaded file, presumably waiting for the client to (possibly) reconnect. Node 2 cannot modify the file at this time.
Since resuming the transfer is impossible, the user must delete the file and then restart the transfer.
To delete the file, the user must wait a few minutes until the share host releases its hold on the file handle, and then the user can delete the file. ("A few minutes" ranges from about 2 minutes on Windows, up to about 10 minutes on a Linux NAS.)
To delete the file sooner, an administrator can force a failover so that node 1 is active, allowing the user to modify the file again.
See Unable to resume transfer or delete file after failover in the Ipswitch Knowledge Base for more information.
Unable to delete files in the Web Transfer Client after failover
When a cluster fails over from node 1 to node 2 during an upload using the Web Transfer Client, both the browser session and the file transfer fail. When the user logs back in, the upload does not resume. Although the partially uploaded file is present, it cannot be deleted. This is caused by the share host (Windows UNC or Linux NAS) holding an open handle for node 1 on the partially uploaded file. Node 2 cannot modify the file at this time.
Since resuming the transfer is impossible, the user must delete the file and then restart the transfer, or overwrite the file on another upload attempt.
To delete or overwrite the file, the user must wait a few minutes until the share host releases its hold on the file handle, and then the user can delete the file. ("A few minutes" ranges from about 2 minutes on Windows, up to about 10 minutes on a Linux NAS.)
To delete the file sooner, an administrator can force a failover so that node 1 is active, allowing the user to modify files again.
See Unable to delete files in the Web Transfer Client after failover in the Ipswitch Knowledge Base for more information.
Error connecting in FIPS mode (FIPS mode cannot use the pre-7 default SSL certificate)
If you installed WS_FTP Server 6.x with the default SSL certificate, when you upgrade to WS_FTP Server 7, that default certificate is maintained. If you then enable FIPS mode, which requires the use of FIPS-validated ciphers in the certificate, the default certificate will cause a connection error when a user attempts a secure connection. The server log will show the following error:
Failed to begin accepting connection: SSL failed to load key file. Non-FIPS algorithms might be used in the selected SSL certificate.
To work around this issue, you need to use a certificate that uses a FIPS-validated algorithm, such as SHA1. You can select to use your own certificate, or create a new certificate in the WS_FTP Server Manager (from the Home page, select SSL Certificates).
IIS notes
- Prior to installing, the Microsoft Internet Information Services Web site on which you intend to install WS_FTP Server Manager must be configured to use a port that is not already in use. If another application, such as the Web server included with Ipswitch WhatsUp Gold, is operating on the same port as the Web site, you must take one of the following actions:
- change the port used by the existing application.
- configure the Web site to use a port that is not already in use.
- The setup program makes the following changes to your IIS configuration:
- On the Web site, Web Services Extensions will be set to Allow ASP Pages.
- On the WSFTPSVR Virtual Directory, Enable Parent Paths will be enabled.
- On the WSFTPSVR Virtual Directory, Application Pooling will be set to the Medium/Pool level.
- On 64-bit versions of Windows, if 32-bit applications are not allowed to run under IIS, a "Service Unavailable" error is displayed in the browser. To correct this, you must run the following command from the command line to enable 32-bit applications to access IIS:
cscript %SystemDrive%\inetpub\AdminScripts\adsutil.vbs set w3svc/AppPools/Enable32bitAppOnWin64 1After running the command, you must restart IIS.
- In some cases the install will display the error message Could not enable ASP. This typically occurs when Active Server Pages in the IIS Server Extension section have been enabled. To verify this:
- Right-click My Computer, then click Manage. The Computer Management console opens.
- Click Services and Applications > Internet Information Services > Web Service Extensions. The Web Service Extensions are displayed in the right-hand console window.
- Make sure that the Active Server Pages status is set to Allowed. If it is not, right-click Active Server Pages and select Allow.
- Close the Computer Management console.
- If you specify a user other than the default user to serve as the run as user on the IIS virtual folder (if you are using Microsoft IIS as your web server), you may get a HTTP 401 error when you attempt to open the WS_FTP Server Manager. If this occurs, you must open the
WSFTPSVRvirtual folder in IIS and change the anonymous access user password to match the specified user's password.
Operating system notes
- If installing on a Windows Server 2003 domain controller, some required user accounts may not be present. For more information, please see knowledge base article 827016 on the Microsoft Web site.
Note: Installing on a domain controller is NOT recommended.
- Microsoft Windows XP Systems NOT on a Windows domain may encounter problems creating and validating system administrator account entries against local system accounts during the install. To complete the install, a registry value must be edited. Launch Regedit and navigate to the key
HLKM\SYSTEM\CurrentControlSet\Control\Lsa. Find the valueforceguest. Set the value to0to allow account validation. Following the installation, this value may be set back to the original value; however, future installations may also require this change in order to install. - To install on Windows XP, the Windows "Guest" account must be disabled. To disable the "Guest" account:
- Right-click on My Computer and select Manage. The Computer Management console opens.
- Expand Local Users and Groups and select Users. The list of users appears in the main pane of the Computer Management console.
- Double-click Guest. The Guest Properties dialog appears.
Select Account is disabled and click OK.
Configuring the database for remote connections
By default, the Microsoft SQL Server database will only accept connections coming from the local system. To use a remote notification server, to allow multiple servers to share a data store, or to allow a remote Web Transfer Client connection, you have to enable remote connections.
Microsoft's Knowledge Base (KB) provides the following information on remote connections:
"When you try to connect to an instance of Microsoft SQL Server 2005 from a remote computer, you may receive an error message. This problem may occur when you use any program to connect to SQL Server. For example, you receive the following error message when you use the SQLCMD utility to connect to SQL Server:
Sqlcmd: Error: Microsoft SQL Native Client: An error has occurred while establishing a connection to the server. When connecting to SQL Server 2005, this failure may be caused by the fact that under the default settings SQL Server does not allow remote connections.This problem may occur when SQL Server 2005 is not configured to accept remote connections. By default, SQL Server 2005 Express Edition and SQL Server 2005 Developer Edition do not allow remote connections.
For instructions, see the Microsoft KB article: How to Configure SQL Server 2005 to Allow Remote Connections
Other notes
- If
net.exehas been removed from the computer on which you want to install WS_FTP Server, you must create a user account to serve as the WS_FTP Server account in Windows before installing. The account name must begin withIPS_, and it is recommended that it be configured so that the password never expires.During the install, when you reach the Create User Accounts dialog, specify this username without the
IPS_at the beginning.For example, if you created a Windows user account called
IPS_wsftpadmin, enterwsftpadminfor the username on the Create User Accounts dialog.Note: If you are upgrading a previous version of WS_FTP Server with hosts that use Windows NT user databases exclusively, the username you create must be
IPS_plus the username of an existing Windows NT user that has system administrator privileges in WS_FTP Server. - If you select to install to a Web site that uses a custom host header or port, the desktop shortcut created does not use the host header or port. To correct this, you must create a new shortcut using the correct host header and port.
- When creating a rule for Failed Login, Folder Action, Quota Limits, or Bandwidth Limits, the Group Search function does not work.
- When upgrading a host using an external (ODBC) user database, you must manually set permissions to the external database file after the upgrade completes.
When multiple hosts with firewall settings configured share a single listener, the firewall settings for the first of those hosts that a user logs into are applied to all of the hosts that share the listener and have firewall settings configured. Hosts that do not have firewall settings configured are not effected by this issue. We recommend that all hosts that are assigned to a common listener share the same firewall settings.
- If you create a virtual folder with the same name as a physical folder, in 6.1, the physical folder takes precedence for permissions purposes. (This has changed from 5.0, where the virtual folder took precedence.) A work around is simply to change the name of one of the 2 folders.
Uninstalling WS_FTP Server
- In the Control Panel, select Add/Remove Programs.
- Select Ipswitch WS_FTP Server, then click Change/Remove and follow the onscreen prompts to uninstall.
The User Configuration Data Exists screen presents options for removing the configuration database:
- Remove the WS_FTP Server configuration data from the data store
- Remove the Ipswitch Notification Server configuration from the data store
- Also, remove the PostgreSQL database server. (Note: You may have other databases on that server.)
If you want to maintain the configuration data in the database, for example when you plan to upgrade or migrate to another database, make sure that these options are not selected.
For more assistance
For more assistance with WS_FTP Server, consult the following resources:
- Installation and Configuration Guide. This guide includes information on configuring the modules, failover clusters, custom installations, unattended "silent" installations, and uninstalling the product.
- Application Help. Contains dialog assistance, general configuration information, and how-to's that explain the use of each feature. The application help can be accessed from any page in the WS_FTP Server Manager by clicking Help.
- User Guide. This guide describes how to use the application out-of-the-box. It is also useful if you want to read about the application before installing. To view the User Guide offline, select Start > Programs > Ipswitch WS_FTP Server > WS_FTP Server User Guide.
- WS_FTP Server Forum. Provides a resource for you to interact with other WS_FTP Server users to share helpful information about the application.
- Ipswitch Knowledge Base. Search the Ipswitch Knowledge Base of technical support and customer service information.
Installing and Configuring the WS_FTP Server Web Transfer Module
Whether you purchased the WS_FTP Server Web Transfer Module as an add-on to WS_FTP Server or WS_FTP Server with SSH, or you received it with your WS_FTP Server Corporate purchase, you need to run the WS_FTP Server Web Transfer Module installation program. For system requirements, installation procedure, and release notes, go to Installing and Configuring the WS_FTP Server Web Transfer Module.
Installing and Configuring the Ad Hoc Transfer Module
The Ad Hoc Transfer Module is installed separately from WS_FTP Server. For system requirements, installation procedure, and release notes, go to Installing and Configuring the Ad Hoc Transfer Module.
