MOVEit uses Microsoft's built-in TLS/SSL security support provider (Schannel.dll). In all supported versions of Windows, there are several available protocols and cipher suite options enabled by default. Not all of them will meet your security and compliance needs. For example, the much older SSLv2 protocol is enabled by default on the server but is not allowed for PCI-compliant web applications. Be careful to choose the right mix of strong encryption methods and acceptable client support.
Warning: Changing the cipher suites or TLS/SSL versions can affect any applications that use TLS/SSL. Be sure you are aware of the requirements of other applications before making a change. For example, if you select SSL 2.0 only, MOVEit will not be able to connect to the Microsoft SQL database. The intent of this dialog is to allow you to avoid using a weak cipher where not allowed by PCI, FIPS, or other standards.
You can use the SSL tab to select the cipher suites and SSL versions that can be used when establishing an SSL session.
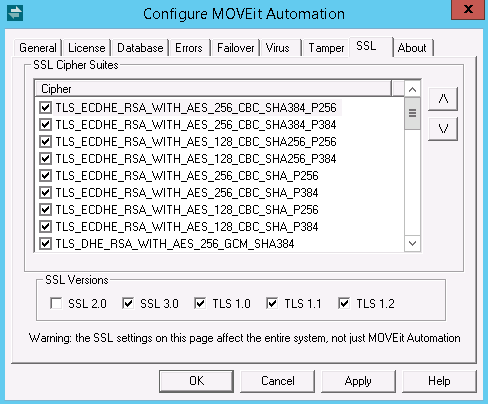
The SSL Cipher Suites section allows you to choose which cipher suites are permissible, and their order of preference. A cipher suite is a named combination of authentication, encryption, and message authentication code (MAC) algorithms used to negotiate the security settings. By default, all ciphers suites enabled in the base Windows OS are enabled.
Note: Both the client's and the server's preferences are taken into consideration when choosing the actual cipher for a given session. Though the server's first choice won't always be chosen, the cipher that ends up being chosen will always be in the set of allowed algorithms on both sides.
Select the Enabled check box to disable a selected entry or to enable an unselected entry.
Entries closer to the top of the list are given preference over entries lower down. Use the arrow buttons to move entries up or down in the list. Even if you must permit weaker cipher suites, you should always put the stronger ones at the top of the list.
SSL Versions are shown at the bottom of the SSL Tab. The default selections include SSL 2.0, SSL 3.0, and TLS 1.0. The versions selected determine the cipher suites that are available.
Select a check box to disable a selected version, or to enable an unselected version.
Note: After any SSL Version change, you need to reboot the system before the change takes effect.
Note: Be aware that the security policy setting System cryptography: Use FIPS compliant algorithms for encryption, hashing, and signing will restrict the available cipher suites and protocols. For example, TLS 1.0 will always be enforced.
Note: Be aware that the setting SSL cipher suite order via Group Policy will override any changes made to cipher suite order on this tab.
To test SSL changes, first obtain a copy of OpenSSL. You can get OpenSSL.exe from the OpenSSL Project. Consult the following examples which show how to use this client and understand the information it provides.
(You need to type the commands in purple. Look for the results in red.)
Using OpenSSL to verify TLS1 is running on a remote server
This test was performed against our moveit.ipswitch.com support server. It shows that a connection using TLS1.
openssl s_client -connect WIN-TRL4JLD99D8:3471 -tls1
Loading 'screen' into random state - done
CONNECTED(000000FC)
depth=0 CN = WIN-TRL4JLD99D8, OU = Testing
verify error:num=18:self signed certificate
verify return:1
depth=0 CN = WIN-TRL4JLD99D8, OU = Testing
verify return:1
---
Certificate chain
0 s:/CN=WIN-TRL4JLD99D8/OU=Testing
i:/CN=WIN-TRL4JLD99D8/OU=Testing
---
Server certificate
-----BEGIN CERTIFICATE-----
MIIC0TCCAbmgAwIBAgIBADANBgkqhkiG9w0BAQUFADAsMRgwFgYDVQQDEw9XSU4t
VFJMNEpMRDk5RDgxEDAOBgNVBAsTB1Rlc3RpbmcwHhcNMTQxMjA1MjE0MjUxWhcN
MjMwNDA1MjE0MjUxWjAsMRgwFgYDVQQDEw9XSU4tVFJMNEpMRDk5RDgxEDAOBgNV
BAsTB1Rlc3RpbmcwggEiMA0GCSqGSIb3DQEBAQUAA4IBDwAwggEKAoIBAQC+Alcm
qM+OpzRA1Sk+qr8Ofsvnt52sVg/B+J9b5UsRWabrNAulXMmh6gHLOXGzZMR4ouha
IXRT91aOoJa4NBnoT/oymRnv4tSIDc77jG/fiXTvX5R+XXvpo83npfuuRIu+9S1S
F1C3elO/c6B2imeblee16HN+x6GNgRaLCX5fFKsdZaM9LEAxCTGcq2bBjOEQiAXH
uZ+S5yu7BUZcIJCoJh5WRDYS1GSlIonMBGgOHCgXOLHjh7mqQvMvugkF8ldz5piZ
mEnHdKnbxXqGhhh/kU7E6OuELc9E+Iscm2ZY2zJt9gylyoLmmm+l102G5bvzHEDT
3Trceu6GHj2mnd+dAgMBAAEwDQYJKoZIhvcNAQEFBQADggEBAC+wCLSVwfR8tkWH
tVh0Nd9pyMdMuyDNmR9M1041FBf94F+6SXXSL/R6pcfOVgYqGdzhZqEg/xATD4RW
wnAEg+pSTW0WrJBiSLRIzbV3ykESjHdk5s53wJfCRaOYAgqeWjxy2AHpFTEd7K4Y
OQ98z5sdWQ2ZERttlcTZi1PwTyEgOqpGJqGJ1Bi4sMUPqX8+Ob95zESW5A2dzaB0
F6SUZosCkC8+00QTOhnnGW/MJk02ox5AwOUeVs1HJk/U9IydDy3Knka2gDed9W04
b4f5EAeoGzihBWI3GEKW44Tbmtm17nQTILmtyaBOPJPaRzl5LdG86tDc1SOAcOPz
lHnv2mg=
-----END CERTIFICATE-----
subject=/CN=WIN-TRL4JLD99D8/OU=Testing
issuer=/CN=WIN-TRL4JLD99D8/OU=Testing
---
No client certificate CA names sent
---
SSL handshake has read 1215 bytes and written 349 bytes
---
New, TLSv1/SSLv3, Cipher is ECDHE-RSA-AES256-SHA
Server public key is 2048 bit
Secure Renegotiation IS supported
Compression: NONE
Expansion: NONE
SSL-Session:
Protocol : TLSv1
Cipher : ECDHE-RSA-AES256-SHA
Session-ID: 3F2700008883D23306B46F8A63A138348A412268F08E35B9E016401FD4C98854
Session-ID-ctx:
Master-Key: D54E13EE42BFF28224222EB489758CAA37A1F24D1073F98414EF0A379EE9249F
D4647C1BEC129F306714A5CD17780980
Key-Arg : None
PSK identity: None
PSK identity hint: None
SRP username: None
Start Time: 1418072824
Timeout : 7200 (sec)
Verify return code: 18 (self signed certificate)
Using OpenSSL to verify SSL 3 is NOT running on a remote server
(This test was performed against an internal IIS server after SSL3 was manually disabled.)
openssl s_client -connect WIN-TRL4JLD99D8:3471 -ssl3
Loading 'screen' into random state - done
CONNECTED(0000012C)
2980:error:1408F10B:SSL routines:SSL3_GET_RECORD:wrong version number:.\ssl\s3_pkt.c:338:
---
no peer certificate available
---
No client certificate CA names sent
---
SSL handshake has read 5 bytes and written 7 bytes
---
New, (NONE), Cipher is (NONE)
Secure Renegotiation IS NOT supported
Compression: NONE
Expansion: NONE
SSL-Session:
Protocol : SSLv3
Cipher : 0000
Session-ID:
Session-ID-ctx:
Master-Key:
Key-Arg : None
PSK identity: None
PSK identity hint: None
SRP username: None
Start Time: 1418074464
Timeout : 7200 (sec)
Verify return code: 0 (ok)
---