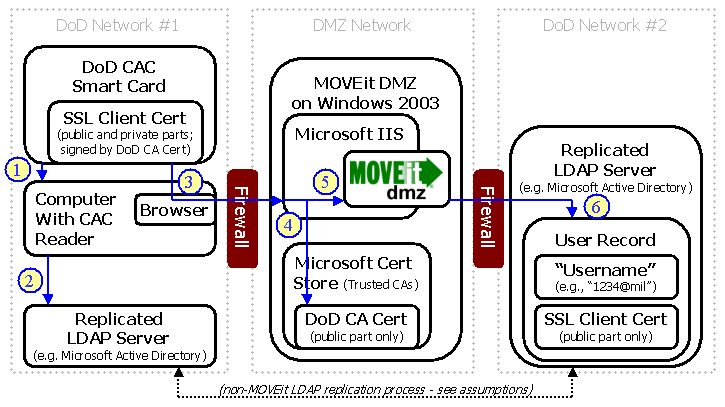
When enabled for external authentication, MOVEit DMZ can integrate into a Common Access Card (CAC) environment to allow users to access MOVEit DMZ without having to provide a username and password. The hardware certificate provided by the user's CAC Smart Card can be used to both identify and authenticate the user. This page details how to configure MOVEit DMZ to function properly in a CAC environment.
CAC environments, particularly those used by the U.S. Department of Defense (DOD), typically use Smart Cards containing hardware-based SSL client certificates as identification and authentication mechanisms. User information is stored in a directory, typically Microsoft Active Directory. When a user inserts their Smart Card into a reader at a workstation and enters the proper PIN code, the hardware certificate is used to identify which user is logging on and authenticate them.
MOVEit DMZ can use the same hardware client certificate to determine the identity of the user who is trying to access the site, and match the certificate against the copy contained in the user's Active Directory account to verify the user's identity.
Integrating MOVEit DMZ with a CAC environment involves several steps. First, the CAC CA certificate must be trusted as a valid signing certificate on both the MOVEit DMZ server and in MOVEit DMZ itself. Next, a DMZ external authentication source must be configured for the directory, to allow user information and authentication to be controlled by that directory. Next, the Allow Username from Client Certificate option must be enabled in the org-level HTTP policy settings page. This allows MOVEit DMZ to identify an incoming user based solely on their provided client certificate. Finally, the external authentication source must be configured to read a value from the provided client certificate and match it against a value in the user directory. This allows DMZ to identify the user's information in the directory.
The CA certificate that user client certificates are signed with must be trusted by the Windows server that MOVEit DMZ is running on by "chaining up" to a certificate in the Microsoft Trusted Root Certificate Store. Users will not be allowed to access the MOVEit DMZ application unless the CA certificate that signed it is trusted.
The CA certificate must also be marked as a trusted CA in the MOVEit DMZ application itself. If the CA certificate is not trusted by MOVEit DMZ, users will not be allowed to sign on with their client certificates. See the System Configuration - SSL and SSH - SSL - Client Certs - Trusted CAs documentation page for more information about trusting a CA certificate in MOVEit DMZ.
Initial configuration of the external authentication source will be similar to setting up any other LDAP source. CAC integration requires an LDAP Lookup+Authentication source as many different user properties are queried from the LDAP server. See the Security Policies - External Authentication - LDAP Lookup doc page for more information about configuring such a source.
In addition to the normal parameters, CAC integration requires the proper configuration of the Client Cert Field value. This is the name of the field in the LDAP directory which contains the client certificate data for the user. For Active Directory servers, this value is called "userCertificate". Without this value, MOVEit DMZ will be unable to match the user's client certificate against their certificate in the directory, and will thus be unable to authenticate the user.
The Allow Username from Client Certificate option can be found on the Settings - Security Policies - Interface - HTTP page in the MOVEit DMZ web interface. This option allows DMZ to identify the user from their client certificate. See the Security Policies - Interface doc page for more information about this setting.
Normally, DMZ will be able to determine the user's identity by looking in its locally cached certificate store. If this is unsuccessful, such as if the user is new to the system, or their client certificate has recently been changed, DMZ will go out to the directory server configured in the external authentication source to look for a matching user record. This is where the following settings take effect.
When MOVEit DMZ needs to determine the user's identity from the directory server, the Client Certificate Value and Matching LDAP Field settings allow it to more easily search for the user's directory entry based on information in the provided client certificate. These options become available in the external authentication source once the org-level Allow Username from Client Certificate option is enabled. See the Security Policies - External Authentication - LDAP Lookup doc page for more information about these settings.
For CAC environments, typically the Principal Name value in the certificate's Subject Alternative Name (SAN) extension is used as the identifier when matching the certificate to a user entry in the directory server. For Active Directory servers, this value is matched to the "userPrincipalName" field.
Once CAC integration is configured, users will be able to access MOVEit DMZ without providing a username or password, as long as their hardware client certificate is available. First-time access to the DMZ site will still result in the signon page being displayed. However, with the Allow Username from Client Certificate option enabled, a link will be provided prompting the user to click if they have a client certificate and would like to automatically sign on. If this process is successful, a long-term cookie will be set on the user's browser which will instruct DMZ to automatically forward the user to the client certificate identification process in the future, so they shouldn't need to see the signon page again from that point on, unless their cookie gets removed or they access the site from a different computer.
NOTE: MOVEit DMZ can be configured to require passwords with client certificates when authenticating users. If this option is enabled at the organization level, or on a user-by-user basis, users may not be able to access the DMZ site without providing a username and password. Users who require passwords with client certificates will be returned to the signon page if they attempt an automatic signon with a message indicating that further credentials are required.
MOVEit DMZ CAC authentication assumes that either:
How browser-based CAC authentication works with MOVEit DMZ:
