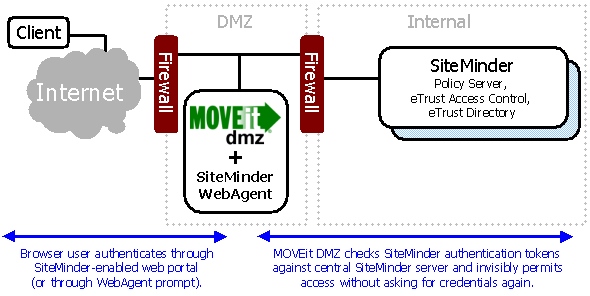
When enabled for external authentication, MOVEit DMZ can interface with CA's eTrust SiteMinder product to enable single-signon to a DMZ server operating in a SiteMinder environment. This allows users to log on to DMZ without having to enter their credentials, as long as they are already authenticated to the SiteMinder environment. This page details how to configure both MOVEit DMZ and SiteMinder to allow DMZ to function properly in a SiteMinder-integrated environment. For more details about configuring the SiteMinder Policy Server and Web Agents, see the documentation for these products.
NOTE: The SiteMinder integration feature, and these instructions, were developed for SiteMinder version 6.0 SP5.

Installing a SiteMinder Web Agent on a server with MOVEit DMZ installed typically involves some extra steps beyond those mentioned in the Web Agent installation guide. This is because the Web Agent typically installs into the default website under IIS, and MOVEit DMZ typically installs itself in its own separate website.
Once the Web Agent has been installed on the MOVEit DMZ server as per the Web Agent installation guide, anything that was added to the IIS default website needs to be copied to the MOVEit DMZ website. For Windows 2003 Server, this includes the "siteminderagent" virtual directory and the wildcard application mapping for the ISAPI6WebAgent dll.
Follow these steps to copy the "siteminderagent" virtual directory to the MOVEit DMZ website:
Follow these steps to copy the wildcard application mapping entry for the ISAPI6WebAgent dll to the MOVEit DMZ website:
Configuring MOVEit DMZ to integrate with SiteMinder simply involves enabling the SiteMinder Integration option through the web interface. This option may be found by signing on to MOVEit DMZ as a SysAdmin, and then finding the SiteMinder settings page under Settings | System | User Authentication. For details about the setting, see the System - User Authentication documentation page.
After enabling this setting, be sure to note the SiteMinder Shared Secret value. SiteMinder will need to be configured to return this value to MOVEit DMZ as part of a Response object before DMZ will begin trusting the SiteMinder HTTP headers injected into an authenticated and authorized request by the Web Agent.
Because MOVEit DMZ requires several allowances to be made in SiteMinder, it is generally wise to create a separate Agent Conf Object and a separate Realm or Sub-Realm in the SiteMinder Policy Server to protect the DMZ server. This allows the following necessary changes to be made without affecting other protected servers.
Several of MOVEit DMZ's file transfer mechanisms involve making requests from the local server back to itself. To allow these to function correctly, the SiteMinder Web Agent needs to be configured to ignore requests to the local computer. Depending on how your server is configured, this is done in one of two ways.
If MOVEit DMZ is the only running website on the server, then this is done by adding the server's computer name to the IgnoreHost parameter on the Agent Conf Object being used by the Web Agent on the server. Note that the computer name should be used here, not "localhost" as one might assume. SiteMinder resolves localhost to the computer name before checking the IgnoreHost value, so adding "localhost" will not exempt local connections.
If there are other websites on the server (more specifically, if the MOVEit DMZ website is not configured to bind to "All Unassigned" IP addresses), then an alias to the MOVEit DMZ website must be added to the IgnoreHost parameter. If an alias for the MOVEit DMZ website already exists, enter that value in the IgnoreHost parameter on the Agent Conf Object. Otherwise, create one by either adding it to a DNS directory that is accessible by the DMZ server, or by adding it to the "hosts" file in C:\WINDOWS\SYSTEM32\drivers\etc.
Once the alias has been set up and SiteMinder has been configured to ignore it, change the Machine URL setting in the MOVEit DMZ Config program's Paths tab to use the alias, so that machine connections will be ignored by SiteMinder.
NOTE: If this latter method is used, be aware that the MOVEit DMZ Checker program will not work unless it is configured to test the alias URL. You can change the test settings for Checker by clicking Options | Configure....
Neither the ActiveX nor the Java-based MOVEit Wizard clients are able to access and submit the SiteMinder identification cookies necessary to operate against a SiteMinder-protected website. Therefore, the MOVEitISAPI module which they both use for file transfer operations needs to be exempted from protection by SiteMinder in order for browser-based file transfers with the MOVEit Wizard clients to work properly. Since such file transfers cannot be done without an established MOVEit DMZ session anyway, this should not pose a security risk to the server.
To exempt the MOVEitISAPI module from SiteMinder protection, a Sub-Realm needs to be created under the Realm that protects the MOVEit DMZ server. This sub-realm should have a resource filter of "moveitisapi/moveitisapi.dll" and should be marked as Unprotected.
In order for MOVEit DMZ to trust the HTTP headers provided by the SiteMinder Web Agent, a special static header needs to be included that contains the shared secret value automatically generated by DMZ when its SiteMinder Integration setting is enabled. This header can be added by creating a new Response object under the policy Domain that protects the MOVEit DMZ server. The new Response object must include a static WebAgent-HTTP-Header-Variable attribute with a variable name of "SM_MOVEITDMZ_SHAREDSECRET" (so that the full HTTP header name ends up being "HTTP_SM_MOVEITDMZ_SHAREDSECRET"), and a variable value equal to the DMZ shared secret string. Once the Response object has been created, it will need to be added as a Response to the Rule which covers the MOVEit DMZ server in the appropriate domain Policy object.
When configured to use an installed and working SiteMinder Web Agent, MOVEit DMZ will no longer prompt users for credentials when they arrive at MOVEit DMZ's web browser interface. The username of the logged-in SiteMinder user will be used as the username for the MOVEit DMZ account as well.
As such, there is no direct way to log on to MOVEit DMZ with a different username than the one being used to authenticate to SiteMinder. If this becomes necessary (such as for logging in as an administrator user with a different username), log on to DMZ as usual (using SiteMinder), then apply the following query string to the URL in the web browser:
?transaction=signoff&arg12=signon
These query string parameters instruct DMZ to log off the current user account, and return the signon screen to the browser. From the signon screen, a different username and password can be entered. DMZ will use the provided username and password to authenticate the user instead of the current SiteMinder information.