MOVEit DMZ relies on Microsoft's IIS server to provide HTTPS connection services. Therefore, MOVEit DMZ must also rely on IIS to also provide client certificate functionality.
MOVEit DMZ users must use client certificates that are ultimately trusted or stored in the Microsoft Certificate Trusted Root store, but MOVEit DMZ's certificate management interface usually takes care of this requirement behind the scenes. This section focuses on the IIS settings that the MOVEit DMZ installation/upgrade toggles to turn on client certificate support (by default) and a second supported option.
MOVEit DMZ's web interface supports client certificate authentication as soon as it is installed or upgraded to version 4.0 or higher. No manual changes to IIS are required; the installation/upgrade program sets the necessary IIS settings behind the scenes.
Authentication requirement flags on individual user accounts control whether client certificates are required and what client certificates can be used for authentication. (See "Web Interface - Users - Profile" for more information about this.)
By default, MOVEit DMZ sets the "Accept client certificates" flag on two files: "humancc.aspx" and "machinecc.aspx." The "cc" in both files stands for "client certificate."
All web browser sessions must authenticate through human.aspx and all other clients must authenticate through machine.aspx. When a user attempts to authenticate through either "human.aspx" or "machine.aspx" and MOVEit DMZ notices that the user's account requires client certificate authentication, MOVEit DMZ will automatically redirect the user's session to "humancc.aspx" or "machinecc.aspx." At this point the user will be prompted for client certificate credentials (if using a web browser) or client certificate credentials will be consumed (if using another client). No "second sign on page" is presented; from the user's perspective the entire sign on operation requires only a single submission.
No other files or folders are marked to "Accept client certificates". Access to MOVEit DMZ resources is only possible after a user authenticates with any required client certificates, so only the authentication gateways need to be marked to "Accept client certificates".
Do not set the site-wide "Accept client certificates" flag on your MOVEit DMZ IIS website. This configuration is not supported and is not necessary to require individual MOVEit DMZ users to use client certificates while authenticating.
Two signs that someone may have flipped the site-wide "Accept client certificates" on your "moveitdmz" IIS site are:
Setting the IIS site flag to "Require client certificates" is usually not necessary and is generally not recommended unless it is absolutely required. The large amount of work required by administrators, end users and operators of remote systems usually makes implementing a pure IIS "Require" environment harder than explaining to an auditor why MOVEit DMZ's application-level client certificates is a better choice.
Furthermore, the "Require client certificates" flag is only supported by MOVEit DMZ software under Windows Server 2003.
MOVEit DMZ's FTP, SSH, ISAPI and related services often communicate with the core MOVEit DMZ application through HTTP/S-based XML transactions. To allow this conversation to continue in a "Require client certificates" environment, you must make a copy of the original "moveitdmz" IIS and set it to listen for localhost connections only.
To set up this extra site and configure MOVEit DMZ to use it in the context of setting the IIS site-wide "Require client certificates" flag, use the following procedure.
Although the default client certificate property on your "moveitdmz" IIS site will be set to "Require...", the following folders must always be marked "Ignore client certificates" to support the use of the Java Upload/Download Wizard.
The MOVEit DMZ installation and upgrade programs will reset "Ignore client certificates" on these folders automatically when they are run. (However, "Repair" installation actions will not reset these parameters.)
To revert from "Require..." to "Accept...", the easiest way to proceed is to set the IIS site-level client certificate requirement from "Require..." to "Ignore..." and then force a MOVEit DMZ upgrade (not just a "repair") to reset the appropriate properties on other elements in the IIS web site. (The latest procedure to force a complete MOVEit DMZ upgrade is available as an article in the Knowledge Base on the MOVEit support site.)
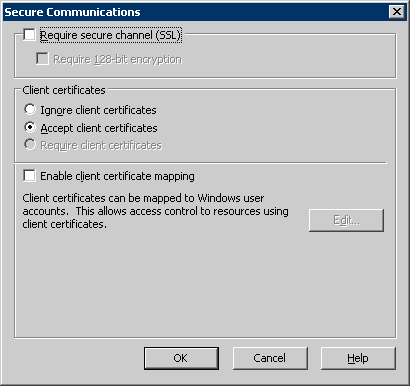
Otherwise, set the IIS site-level client certificate requirement from "Require..." to "Ignore..." (while choosing to override all subfolders) and then set the "Accept client certificates" flag on the "humancc.aspx" and "machinecc.aspx" files as shown here:

After completing either procedure, you may also wish to delete the extra localhost IIS site that setting the site-wide "Require..." flag requires. You may also need to change the "Machine URL" on the "Paths" tab of the DMZ Config Utility if your "moveitdmz" site is bound to a specific IP address.