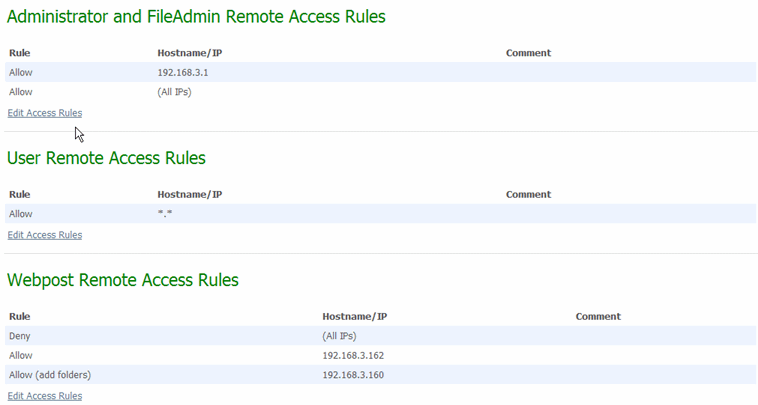
The remote access policy defines the list of IP addresses and/or hostnames from which users and administrators may access this organization.
Registered access settings may be applied to "users" or "administrators." The "administrators" designation includes FileAdmins and Admins. The "users" designation includes Users and TempUsers. "WebPost" rules apply to anonymous users who submit webposts into the MOVEit DMZ system but never actually sign on.
Registered access for SysAdmins is configured in the "Remote Access" section of the "System Settings." (See the System Remote Access Policy page for more information).
These settings may also be overridden by "custom" IP/hostname rules for particular users. (Some organizations will want to leave these "default" settings blank and ONLY allow specific IP access for each user.)
By default, administrators and users may only sign on from the local console. This is why there is a reminder on the home page of administrators to increase this access when the default value are set, and it is also why SysAdmins are given the chance to expand the range of allowed addresses during the creation of a new organization. Also by default, anonymous WebPost users may submit information to MOVEit DMZ, but may not create new WebPost folders.

The Remote Access rule list is made up of three sections:
Note: See also the Unregistered Senders Remote Access Rules, located on the Unregistered Senders page.
Each section contains all current rules. At runtime, the rules will be processed in the top-to-bottom order displayed here.
There are several columns for each rule as follows:
In addition, an Edit Action Rules link for each section (below the last rule of the section) opens a separate page for each section, that is, one page each for Administrator and FileAdmin Remote Access Rules, User Remote Access Rules, and Webpost Remote Access Rules.
Clicking the Edit Action Rules link for any section of rules opens a separate page for that section. There are separate pages for Administrator and FileAdmin Remote Access Rules (shown below), User Remote Access Rules, and Webpost Remote Access Rules.
On each of these pages, a fourth column, Actions, allows administrators to change details about the rules.
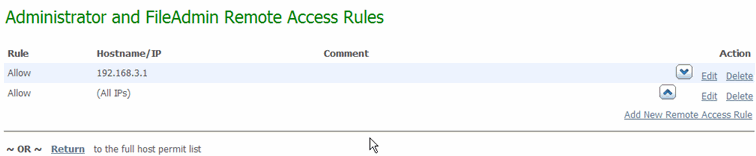
The Action column contains buttons and links for the various actions which may be performed on each rule.
In addition, the Add New Remote Access Rule link (below the last rule) opens the Add Remote Access Rule page, where new rules can be added.
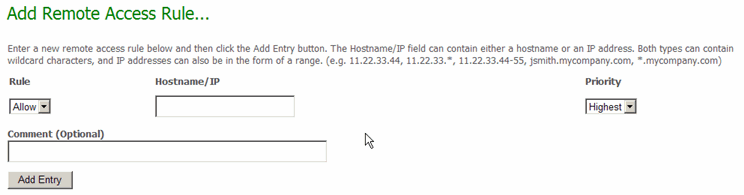
Note: The Add Remote Access Rule page (opened by the "Add New Remote Access Rule" link) and the Edit Remote Access Rule page (opened by the "Edit" link) are the same except that the Edit page is filled with existing values for the selected rule.
The fields here define a Hostname/IP address or range combination and whether it will be allowed or denied. The individual rule can be assigned a priority for applying it in combination with other access rules. For a new rule, fill out the fields to create a new remote access rule and then click the Add Entry button. Similarly, for an existing rule, change fields and then click the Update Entry button.
The fields and buttons on this page are:
Hostname/IP entries can be individual hostnames, individual numeric IP addresses, or masks that allow matching against a range of hostnames or addresses. An asterisk ("*") will match any value in a particular position. For example, "2*" matches "23" or "213", "*cat" matches "tomcat" and "bobcat" and "*" matches all of the above.
A dash ("-") will match numeric values which fall on or between the numbers on either side of the dash. For example, "2-4" matches "2", "3" and "4" but not "1" or "5".
When an incoming IP address or hostname is tested, rules are processed top-to-bottom. The first rule which applies to the incoming IP or hostname is the rule which actually allows or denies access.
By default, all IP addresses and hostnames are denied if they "fall off the end of the list."
Specific IP addresses and hostnames (e.g. 192.168.3.4 or test.stdnet.com) should be at the top. Ranges of IP addresses and hostnames (e.g. 192.168.3.* or *.stdnet.com) should be in the middle. Catch-all entries (e.g. 192.*.*.* or *.edu) should be at the bottom.
Given the following access list...
Allow/Deny IP Address or Hostname ALLOW 192.168.3.24 ALLOW test.stdnet.com ALLOW 192.168.4.* ALLOW *.bed.stdnet.com DENY 192.168.5.1-64 ALLOW 192.168.5.*
...the following addresses will be allowed or denied access:
Incoming Address Allowed Reason 192.168.3.24 YES Matches "ALLOW 192.168.3.24" test.stdnet.com YES Matches "ALLOW test.stdnet.com" 192.168.4.21 YES Matches "ALLOW 192.168.4.*" feather.bed.stdnet.com YES Matches "ALLOW *.bed.stdnet.com" 192.168.5.21 NO Matches "DENY 192.168.5.1-64" 192.168.5.121 YES Matches "ALLOW 192.168.5.*" 192.168.6.34 NO Does Not Match Any Entry
When a user signs onto the MOVEit DMZ server from a web browser running on the same machine as the MOVEit DMZ server itself, that user is said to be "connected to the console" if he or she connects to MOVEit DMZ using a URL which begins with "http://localhost..." or "http://127.0.0.1..." rather than the usual "http://MOVEitDMZ.nowhere.com..." URL.
These "console connections" are NOT subject to the remote access List. This exception prevents SysAdmins from "locking themselves out" with an empty Access List because they can always sign on from the same machine on which MOVEit DMZ runs. To prevent unauthorized access to MOVEit DMZ through the console, extra care should be taken to secure NT users on MOVEit DMZ and the physical security of the server itself.
When an IP address is locked out, it is locked out across all organizations at a particular site. Any Admin may unlock an IP address, and IPs may be unlocked one at a time, or all at once with the "Unlock All IP Addresses" link. Once an IP address is unlocked it is unlocked for all organizations. Also, whenever an IP address is locked out, all SysAdmin users who have their notification property set to On+Admin will receive an email notification that the lockout has occurred. If there is only one non-system organization configured, Admin users in that org who have their notification property set to On+Admin will also receive email notifications.
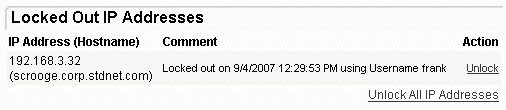
Only SysAdmins may set IP Lockout Policy. (See the IP Lockout Policy section of the System Remote Access Policy page for more information). Starting in version 4.0, IP lockouts are enabled by default and set to lock out IP addresses after 15 bad attempts in any 5 minute period.
To prevent session hijacking, MOVEit DMZ normally does not allow the IP address used by a session to change over the course of that session. However, some firewalls and proxy servers use pools of IP addresses to assign to users who access the internet, and can sometimes assign different IP addresses to a user even within a single session. In order to allow these users full access to the server, the IP Switching feature allows administrators to set an allowable range within which a session IP address can change.

By default, the IP Switching option is set to "None", which corresponds to a subnet mask of 255.255.255.255, or /32. This prevents any sort of IP address switching. Other available values are: