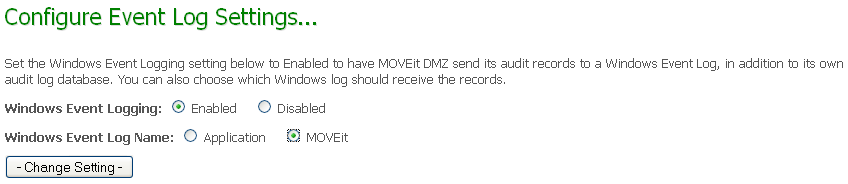
These options force MOVEit DMZ to write each audit log entry into a local Windows Event Log as well as the usual MOVEit DMZ audit database. Entries will either be created with a source of "MOVEit DMZ Audit" in the Windows Application Event Log or with a source of "MOVEit_DMZ_Audit" in the "MOVEit" Application Event Log. Audit log entries reporting successful actions will be entered as Information level events, while those reporting unsuccessful actions will be entered as Error level events.

An example of an entry written to the Windows Application Event Log is pictured below.
Although MOVEitDMZ has the ability to send audit entries directly to a remote Syslog server, there are also many utilities available which can send logs from local Event Logs to SysLog or SNMP management consoles. For more information about how to do this, see the "SysLog and SNMP" documentation.
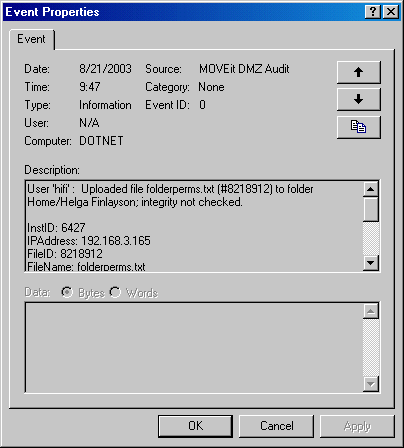
These options force MOVEit DMZ to write each audit log entry to a remote Syslog server, as well as to the usual MOVEit DMZ audit database. SysLog is based on UDP (usually port 514) and is therefore an "best efforts" protocol in the sense that neither the client nor the server will know (or care) if SysLog messages are dropped by the network. Audit log entries reporting successful actions will be entered as Information level events, while those reporting unsuccessful actions will be entered as Error level events. A SysAdmin must configure a Syslog host in addition to enabling this setting. They can also optionally configure a Port to use for the connection (default = 514) and the Facility that audit messages will show up as on the Syslog management console (default = FTP).
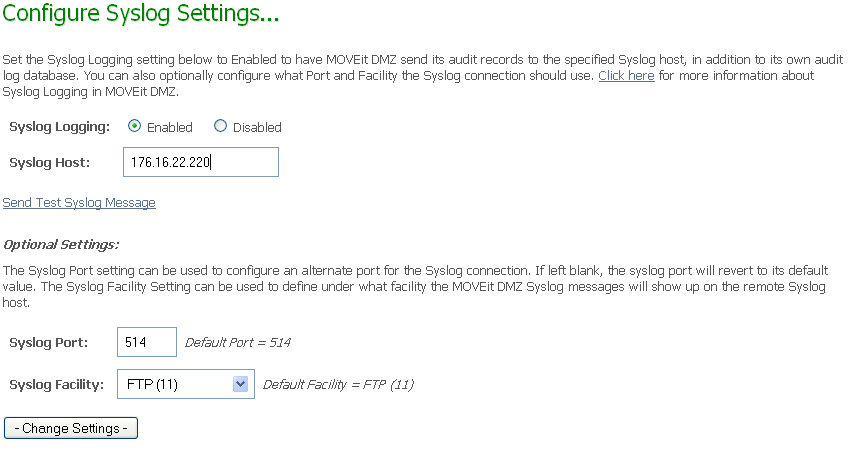
The "Send Test Syslog Message" link can be used to test the current Syslog settings by sending a test message to specified host. Since the BSD Syslog implementation is based on UDP, the administrator will have to manually verify that the test message arrived at the remote Syslog management console.
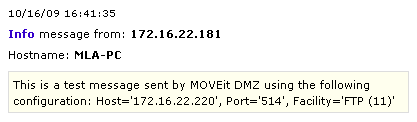
If the test is successful, a message similar to below should show up in the Syslog management console on the remote Syslog server:
When this option is enabled, end users will be shown a nicely formatted and branded error page in the rare event a system exception is generated by MOVEit DMZ. The page will contain details about the error and what was happening when the error occurred, as well as instructions to contact their tech support contact and inform them about the error. When this option is disabled, the user will simply be notified that an error occurred, and instructed to notify their tech support contact. (See the Exception Handing page in the Advanced Topics section for more information)
Normally, MOVEit DMZ records every failed signon attempt that happens on the system to the audit log. On some busy systems however, large numbers of these records can make it difficult to search for other issues, and can slow down access to all audit log records. The options on this page help relieve this problem by allowing administrators to prevent certain types of signon failures from being recorded in the log.
Currently, the only available option is the Log Insecure FTP Failed Signons option. When set to No, this prevents audit log records from being written whenever someone attempts to access the DMZ FTP server in an insecure manner, if the DMZ FTP server is configured to not allow any insecure access. This option will NOT prevent audit log records from being written if the DMZ FTP server is configured to allow insecure access, but either the user's IP address or user account is prevented from using the insecure FTP interface.