The Content Scanning feature allows scanning of incoming files using a remote anti-virus server. MOVEit DMZ will submit incoming files to the anti-virus server using the ICAP protocol. Files that are clean are then passed into the MOVEit DMZ filesystem.
MOVEit DMZ currently supports the following anti-virus programs:
For information on installing and configuring the Sophos ICAP AV scanner, refer to your Sophos documentation.
For information on installing and configuring the Sophos ICAP AV scanner, refer to your Symantec documentation.
These versions of the two anti-virus scan engines support the ICAP protocol (RFC3507 for more information), which is required to interface with MOVEit DMZ. Other “desktop” versions from these same vendors will not work with MOVEit DMZ.
Before you can configure content scanning for incoming files, you must have one of these anti-virus scanners configured on a machine that is accessible to the MOVEit DMZ system.
Note: If you are using the AS2 Module to transfer files, be aware that content scanning does not apply to AS2 transfers. Use MOVEit Central to scan AS2 transfers for viruses.
After you have configured the anti-virus server, you need to set up content scanning for your MOVEit DMZ hosts. To access the Content Scanning settings, you must be logged on as sysadmin. These settings apply to all MOVEit DMZ hosts on the system. Under System Settings, Content Scanning, select Anti-Virus. For a description of each of the settings, see the Web Interface - Settings - System - Content Scanning topic.
Enabling the content scanning option causes MOVEit DMZ to scan uploaded files as follows:
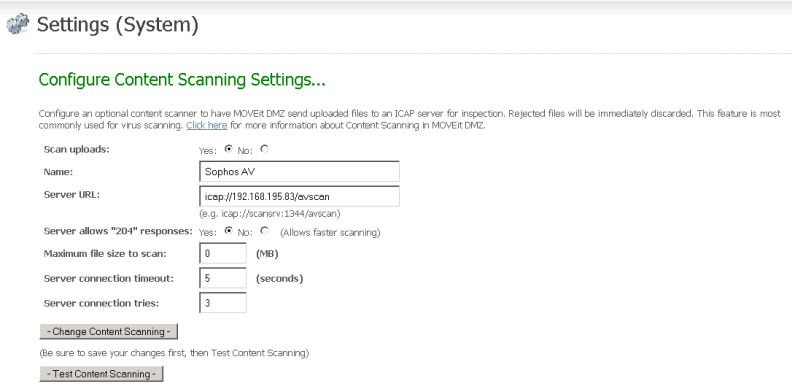
The following screen shows an example of the configuration for a Sophos ICAP AV scanner.

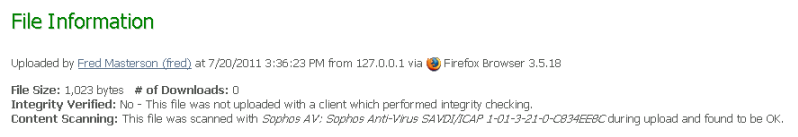
If a file was scanned, file detail pages will display the ICAP server information, for example:
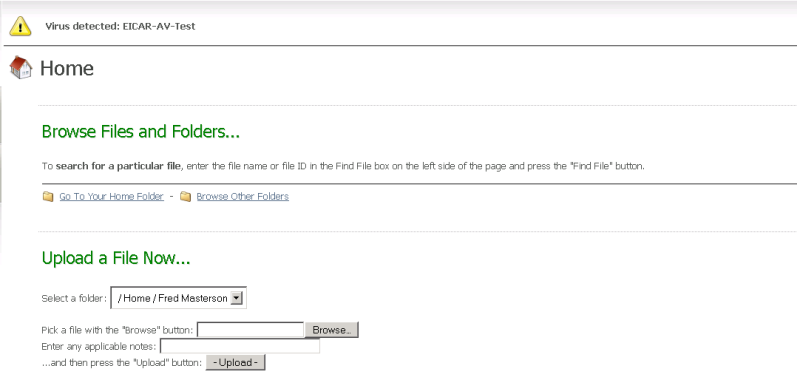
If a file fails the scan, the user who uploaded the file will see an error message at the top of the browser page, for example:
Log file entries will report the user-configured name of the ICAP server used during the file upload. File records will also report the self-identification, version, and virus definition tag from the server, for example:
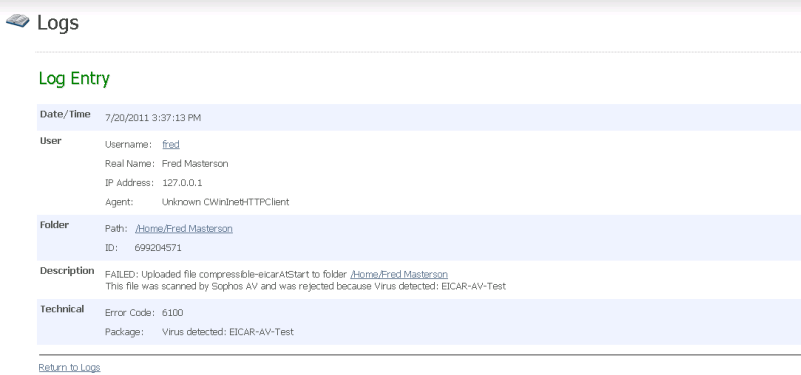
New error code numbers (6100 - 6103) are used to report content scanning errors. This will help when filtering logs. If an upload fails due to content scanning, the corresponding log table records will contain the ICAP server name and, if possible, the name of the virus.
If Content Scanning (Anti-virus) is enabled, MOVEit DMZ checks every few minutes to make sure the anti-virus scanner is available. This is part of the SysCheck routine (see the Advanced Topics - System Internals - Scheduled Tasks topic) and can generate a built-in notification. If the anti-virus scanner is not available, SysCheck sends an email message to the "Send Errors To" email address and warns that the MOVEit DMZ server will not be able to transfer files until this situation is addressed. When the scanner becomes available again, SysCheck sends an email that states that scanning for viruses is now working.
Notification macros for content scanning, if enabled, can report the scan results in the following notifications: New File Upload Notification, File Upload Confirmation, File Non-Delivery Receipt, File Upload List Notification, File Upload List Confirmation, File Not Downloaded List, File Delivery Receipt. The standard templates for these notifications do not include the content scanning results. You can add the macros that report the scan results by creating custom notification templates. Custom notifications are set in an organization via Settings | Appearance | Notification | Custom.
You can add a Content Scanning report which shows any content scanning violations. An example of a violation is a file that failed an anti-virus check. In this case, the report will show the name of the scanner, the file name, and the name of the virus (if known). If you are logged in as Admin, the report shows violations for your organization. If you are logged in as sysadmin, the report can show multiple organizations.