A minimum MOVEit DMZ Resilient architecture consists of at least two MOVEit DMZ nodes, a load balancing device and a NAS device. However, even in a two-node configuration there are different ways to arrange things depending on your performance goals. This document describes the various architectures supported by MOVEit DMZ and discusses the advantages and disadvantages of each approach.
The three types of networks used in the diagrams below are explained below:
The typical role of each component in these architectures is briefly covered below:
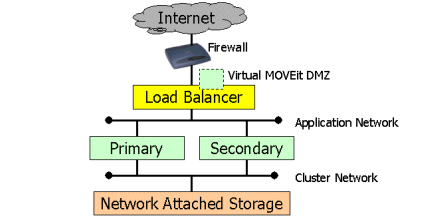
When two MOVEit DMZ nodes are deployed in a resilient cluster, the focus is usually failover rather than load balancing. Nonetheless, it is usually easiest to configure the load balancer to send traffic to each machine equally, as long as connections from each unique remote IP address are always directed to the same physical machine.

Even though the usual focus is failover when implementing this architecture, an additional performance benefit often results from running the database and the application on two separate servers during normal production. If this configuration is desired and a higher level of up-front configuration is not an issue, then then load balancer should be configured so that all incoming APPLICATION connections go to the SECONDARY node unless the secondary node is down. In this configuration, the PRIMARY node primary handles database queries and updates until the SECONDARY node goes down; at this point the PRIMARY node will also handle application traffic.
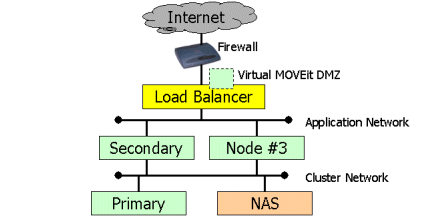
With the introduction of a third, application-only MOVEit DMZ node, the focus of the system begins to shift to offloading and true load balancing. A Load Balancer in this architecture should hand off sessions on a round-robin basis to the SECONDARY node and NODE #3.
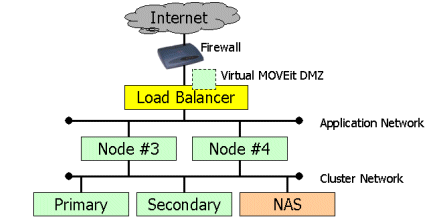
With the introduction of a fourth MOVEit DMZ node, it is possible to drop one or two MOVEit DMZ nodes back to serve as dedicated database (and configuration) nodes. A Load Balancer in this architecture should hand off sessions on a round-robin basis to NODE #3 and NODE #4. Note that web, FTP or SSH services are not disabled on the PRIMARY or SECONDARY nodes in this configuration because these services do not consume significant resources unless they are working with active sessions.
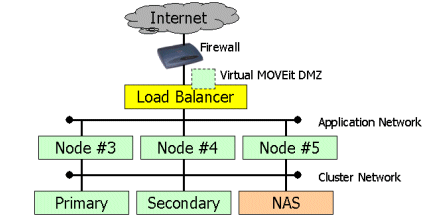
This architecture is similar to the four-node architecture, but with one extra application node (and an additional MOVEit DMZ license).
This architecture is similar to the four-node architecture, but with two extra application nodes (and two additional MOVEit DMZ licenses).
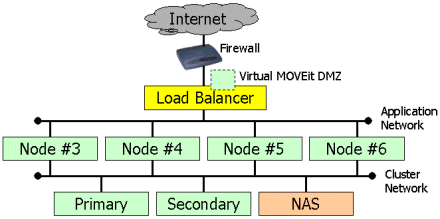
One of the issues with the two, three and four node architectures depicted above is a possible loss of application performance if one of the two available application nodes goes down. To mitigate this loss, you may be able to configure your load balancer to also include the PRIMARY and/or SECONDARY nodes in the "application hunt" if one or more of the application nodes is already down.