Users of SSH clients know to trust specific machines because their keys will match publicly available SSH fingerprints. As part of the instructions you give your clients, you SHOULD be distributing the fingerprint of your MOVEit DMZ SSH server so your clients can confirm the identity of your server. (Without this protection, anyone could spoof this or any other SSH server!)
The following OpenSSH session shows this mechanism in action. Specifically, OpenSSH asks the end user if they want to trust the remote server after displaying the MD5 hash of the remote server's SSH server key.
d:\>sftp sshftpuser@moveit.myorg.com
Connecting to moveit.myorg.com...
The authenticity of host 'moveit.myorg.com (33.44.55.66)' can't be established.
RSA key fingerprint is b4:51:8a:9c:5d:7e:98:db:f0:88:08:52:31:b4:a0:1e.
Are you sure you want to continue connecting (yes/no)? yes
sshftpuser@moveit.myorg.com's password:
MOVEit DMZ's SSH key is automatically generated the first time the server is started and an associated fingerprint is created at the same time. To view your MOVEit DMZ SSH key fingerprint log into a Windows console on your MOVEit DMZ server. Open Start -> All Programs -> MOVEit DMZ -> MOVEit DMZ Config and navigate to the SSH tab to view your MOVEit DMZ's SSH key MD5 hash.
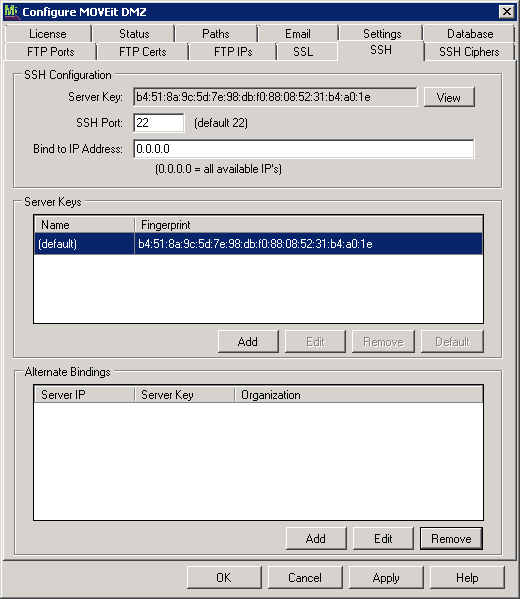
The MOVEit DMZ SSH server key is stored encrypted in the registry under the SSHServer\PrivKey registry entry. Any registry backup, including the registry backup performed by the MOVEit DMZ Backup Utility, will back up this key.
To export MOVEit DMZ's public SSH server key in either OpenSSH or SSH2 format, see the related instructions in SSH - Configuration.
MOVEit DMZ only supports FTP over SSH (or SFTP) and SCP2. SCP (SCP1) and all Terminal sessions will be denied access.
MOVEit DMZ SSH Server uses SSH Protocol 2 only. A client will not be able to connect to the MOVEit DMZ server using only Protocol 1. MOVEit DMZ SSH Server recommends using the following encryption ciphers: AES, 3DES, and Blowfish. (An ever-expanding list of compatible clients and a complete list of encryption options is also included in this documentation.)
If the SSH user is connecting to MOVEit with the correct username but the administrator does not see any SSH public key entries in the audit logs, it is likely that the end user has NOT yet generated a public/private key pair for SSH. End users can often use the ssh-keygen -t rsa command to generate these keys, but they should be advised to NOT enter a passphrase when prompted during the key generation; if a passphrase is entered it will be asked for during each subsequent attempt to connect and will spoil attempts to automate the process.