This guide assumes you have already installed a copy of OpenSSH for Windows.
If you have not already installed OpenSSH for Windows, be sure to UNCHECK the Server box on the Choose Components section during the installation of this client.
sftp -oUserKnownHostsFile=SSHDIR\known_hosts user@host
This will come back with a warning that the host is not known. Enter yes to the question. This will add the host's key to the known_hosts file. Then, simply press CONTROL+C to leave the application.
Example:
C:\Program Files\OpenSSH\bin>sftp -oUserKnownHostsFile=C:\Progra~1\OpenSSH\bin\ssh\known_hosts sshkeyboy@dotnet.corp.stdnet.com
Connecting to dotnet.corp.stdnet.com... The authenticity of host 'dotnet.corp.stdnet.com (192.168.3.15)' can't be established. RSA key fingerprint is ce:08:6f:28:87:b6:50:f4:84:e5:37:c2:68:89:33:2a. Are you sure you want to continue connecting (yes/no)? yes arning: Permanently added 'dotnet.corp.stdnet.com,192.168.3.15' (DSA) to the list of known hosts. sshkeyboy@dotnet.corp.stdnet.com's password:
(CONTROL+C)
C:\Program Files\OpenSSH\bin>
ssh-keygen -t rsa
When asked to enter a file to save the key in, use this value:
SSHDIR\id_rsa
When asked for a password, simply hit enter (and again when asked to confirm). This will create an RSA key which will be used to authenticate to the server. The ssh-keygen program should give the key files their correct permissions automatically.
Example:
C:\Program Files\OpenSSH\bin>ssh-keygen -t rsa Generating public/private rsa key pair. Enter file in which to save the key (P7 $"/.ssh/id_rsa): c:\progra~1\OpenSSH\bin\ssh\id_rsa Enter passphrase (empty for no passphrase): Enter same passphrase again: Your identification has been saved in c:\progra~1\OpenSSH\bin\ssh\id_rsa. Your public key has been saved in c:\progra~1\OpenSSH\bin\ssh\id_rsa.pub. The key fingerprint is: 44:a8:8c:88:3f:3f:91:8a:16:07:e4:c6:4a:6e:b8:df xxxx@jglshuttle
C:\Program Files\OpenSSH\bin>
sftp -oUserKnownHostsFile=SSHDIR\known_hosts -oIdentityFile=SSHDIR\id_rsa user@host
This will come back asking for the user's password. Simply Control-C out of the program at this point.
Example:
C:\Program Files\OpenSSH\bin>sftp -oUserKnownHostsFile=c:\progra~1\OpenSSH\bin\ssh\known_hosts -oIdentityFile=c:\progra~1\OpenSSH\bin\ssh\id_rsa sshkeyboy@dotnet.corp.stdnet.com Connecting to dotnet.corp.stdnet.com... sshkeyboy@dotnet.corp.stdnet.com's password:
(CONTROL+C)
C:\Program Files\OpenSSH\bin>
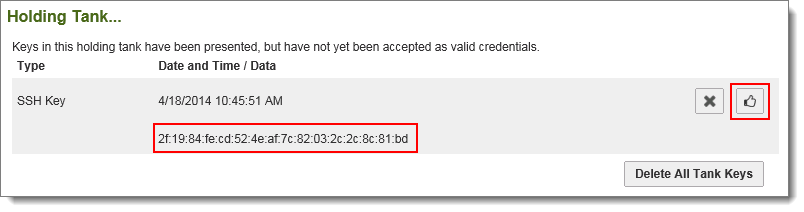
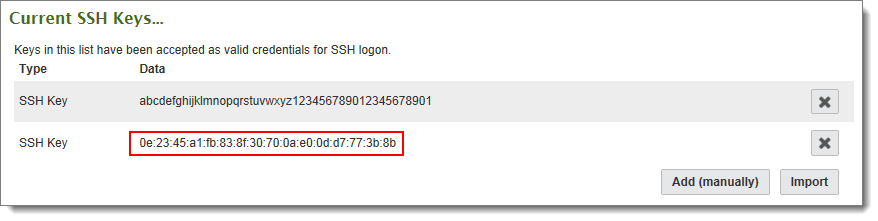
Open the user's profile and under User Authentication > SSH Policy > Current SSH Keys, add this fingerprint. A properly configured user will have a profile similar to the following:
sftp -oUserKnownHostsFile=SSHDIR\known_hosts -oIdentityFile=SSHDIR\id_rsa user@host
Example:
C:\Program Files\OpenSSH\bin>sftp -oUserKnownHostsFile=c:\progra~1\OpenSSH\bin\ssh\known_hosts -oIdentityFile=c:\progra~1\OpenSSH\bin\ssh\id_rsa sshkeyboy@dotnet.corp.stdnet.com Connecting to dotnet.corp.stdnet.com... sftp> pwd Remote working directory: /Home/SSH Key Boy sftp> cd .. sftp> cd .. sftp> dir Distribution Home WebPost sftp>
C:\>type sftp_commands.txt cd /Home/Steve put certreq.txt dir quit
C:\>c:\progra~1\openssh\bin\sftp -oUserKnownHostsFile=c:\progra~1\openssh\bin\ssh\known_hosts -oIdentityFile=c:\progra~1\openssh\bin\ssh\id_rsa -b sftp_commands.txt steve@dotnet.corp.stdnet.com Connecting to dotnet.corp.stdnet.com... sftp> cd /Home/Steve sftp> put certreq.txt Uploading certreq.txt to /Home/Steve/certreq.txt sftp> dir DecSet_6858908.exe MIFreelyInst_9971297.exe brain_1731860.wav certreq_1140952.txt decryptedFile_5848271.dat dmz_backups_2157003.html webpost_bundle_4594384.xml sftp> quit