The remote access policy defines the list of IP addresses and/or hostnames from which system administrators may access this organization.
By default, SysAdmins may only sign on from the local console.
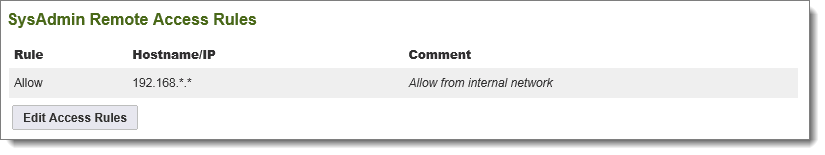
The Remote Access rule list is different for SysAdmins compared to other organizational Administrators. There is no section for end users and none for Webposts because these cannot be created in the System organization. The SysAdmin Remote Access Rules control from which IP addresses or SysAdmins may connect.
The process for setting up Remote Access Rules for SysAdmins is the same as that for organizational Administrators. You can find details and examples in the Remote Access Policy page.
The Trusted Hosts permissions list for the Sysadmin organization can be set by Sysadmins only.
You can add a hostname or IP address here that will allow the sysadmin to login to MOVEit DMZ from a host that matches the hostname or IP address.

For most purposes, when trusted host access is needed, you will want to provide that access for a specific organization. The Trusted Hosts settings available to sysadmins now apply only to the System organization. A Trusted Host for an organization is defined by using the rules available in the Security Policies - Remote Access options.
Under normal operations, clients that access MOVEit DMZ from any of the local interfaces will bypass the normal IP lockout and session IP consistency checks. This allows services like the MOVEit DMZ FTP server and the MOVEit DMZ SSH server to function properly, and present the client's IP address for display and logging purposes. The Trusted Hosts permission list allows sysadmins to designate certain hosts as Trusted, allowing them the same privileges as local interfaces. This feature is most often used when using MOVEit DMZ API within a separate web application to provide single-signon access to MOVEit DMZ. It allows the API session to be transferred to the client browser, and back again, and also allows API to present the client's IP address for display and logging purposes.
Note: Hosts added to the Trusted Hosts permission list will avoid many of the standard security safeguards built into MOVEit DMZ to prevent unauthorized access (though clients connecting through such hosts will not). NEVER ADD A HOST TO THIS LIST UNLESS YOU KNOW WHAT YOU ARE DOING! If you are uncertain as to whether a host should be added to this list, feel free to contact Ipswitch MOVEit support for assistance. Also, for security reasons, the All IPs mask of *.*.*.* will not be allowed as a Trusted Host entry.
The IP Lockout settings allow SysAdmins to decide how many attempts in how short a time period are required to lock an IP address out. A lockout expiration option is also available which will automatically unlock locked out IP addresses after a configured time period.
Note: Under normal operations, clients that access MOVEit DMZ from any of the local interfaces will bypass the normal IP lockout and session IP consistency checks. This allows services like the MOVEit DMZ FTP server and the MOVEit DMZ SSH server to function properly, and present the client's IP address for display and logging purposes. The Security Policies - Remote Access options allow Org admins to allow access to certain hosts (trusted hosts), allowing them the same privileges as local interfaces.
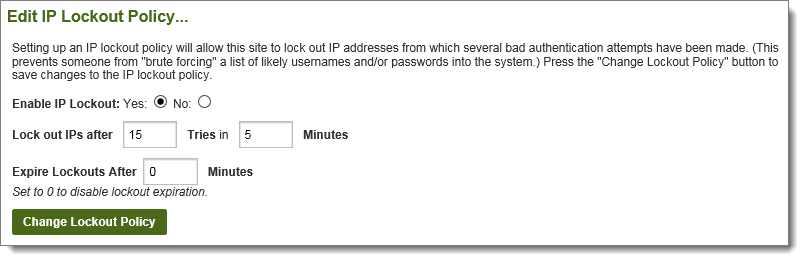
Starting in version 4.0, IP lockouts are enabled by default and set to lock out IP addresses after 15 bad attempts in any 5 minute period.