A client cert's SHA-1 Thumbprint provides a cryptographic-quality way to prove that a specific certificate is what it says it is. A client cert's CN, however, could be found on hundreds or thousands of other perfectly valid client certs. The way MOVEit Transfer keeps track of certs that use CN authentication is to follow their CA chain and to only allow certs that have been signed by a short list of Trusted CAs to authenticate.
By definition, a Trusted CA is a CA that an organization trusts with providing properly (CN) named certificates to the correct users. If a CA issues certificates with the same CN to multiple users (e.g., "Thawte Personal Freemail CA"), then that CA should NOT be a Trusted CA. If your organization already maintains its own CA, then that CA should probably be in your list of Trusted CAs. Third-party organization CA's may or may not also be added as trusted CAs depending on their ability to issue unique CN-named certificates to the correct users.
Trusted CA vs. Microsoft Trusted Root Certificate Store
The Microsoft Trusted Root Certificate Store contains installed certs of CAs. All client certs that connect to MOVEit Transfer must "chain up" to a cert installed in the Microsoft Trusted Root Certificate Store. Once an SSL connection is established, however, the Microsoft Trusted Root Certificate Store has no further role in authentication.
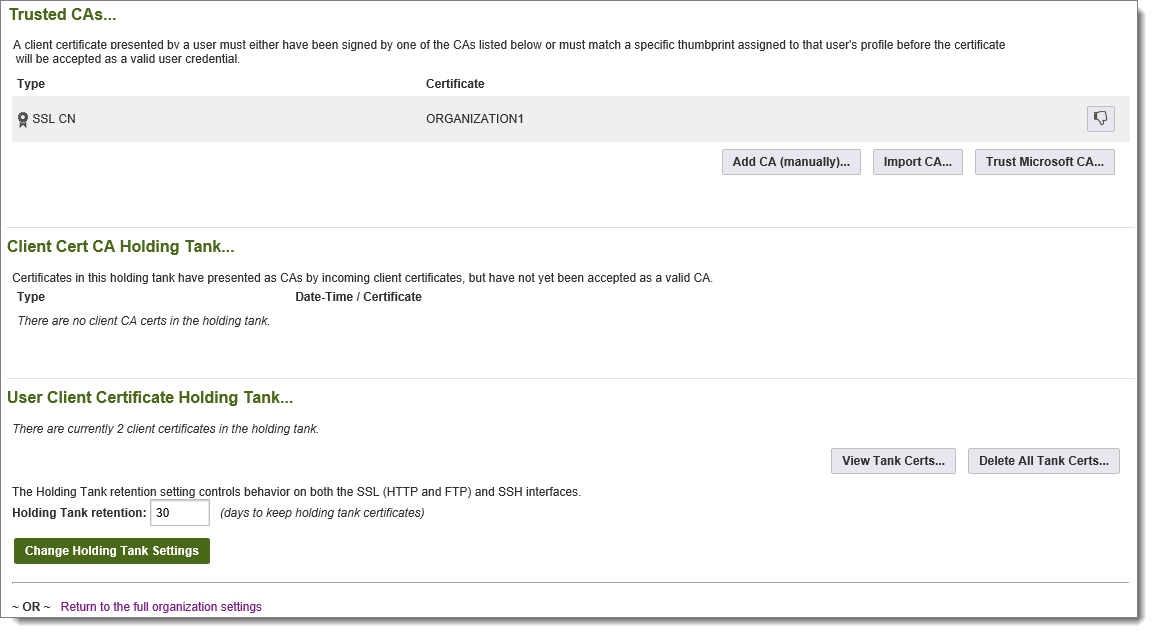
The Trusted CAs is a (CN) list of CAs; no certificates are actually installed here. Client certs that offer a CN for authentication must be signed by one of the CAs listed here, but CAs in this list do not actually need to be in the Microsoft Trusted Root Certificate Store too as long as each Trusted CA "chains up" to an entry in the Microsoft Trusted Root Certificate Store. The Trusted CA list is available on the org-level SSL settings page, which is accessible from the Settings page by following either the Security | Interface Policy | FTP or Security | Interface Policy | HTTP links.
Please also see the Connect/Authenticate examples on the Client Certs - Overview documentation page for an illustration of how the Trusted CA vs. Microsoft Trusted Root Certificate Store work together.
Trusted CA Holding Tank
The Trusted CA list has its own holding tank similar to the client cert holding tank. To get a CA certificate entry in the Trusted CA holding tank, a user must connect with a client cert that "chains up" to a CA in the Microsoft Trusted Root Certificate Store and whose thumbprint does not match the related user profile.
Trusted CA List Maintenance
There are two other ways to add Trusted CAs. One is to manually type the CN of a Trusted CA. The other is to scroll down and select any of the CA certs already installed in the Microsoft Trusted Root Certificate Store (or Microsoft Intermediate CAs Store).
When you delete a Trusted CA entry, you are only deleting a pointer, even if the Trusted CA is also installed in the Microsoft Trusted Root Certificate Store. (You must delete certificates directly from the Microsoft Trusted Root Certificate Store using the usual MMC console if that is the desired action.)
Organization Cert-Signing CA
Every organization on MOVEit Transfer can create and use a single CA certificate to sign any client certificates created through the MOVEit Transfer web interface. These CA certificates are "self-signed" but are automatically included in and installed through the "*.pfx" client certificate files created during the new client certification creation process.
Background: In version 4.0, MOVEit Transfer generated self-signed client certificates (i.e., certificates not signed by any CA) through a similar interface. However, in practice only about 100-200 self-signed client certificates can be supported under the default IIS configuration so client certificates created by MOVEit Transfer are now CA-signed to avoid this limit.
How and When to Create an Organization Cert-Signing CA
If you have been directed to create an organization CA to sign client certificates (after clicking a Create New link) or you see a Client Signing CA Cert section like the following section:
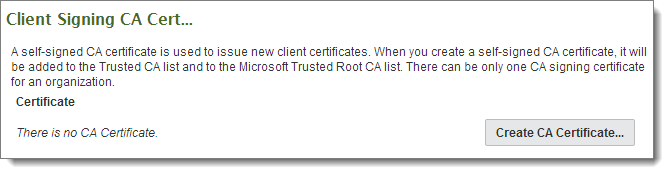
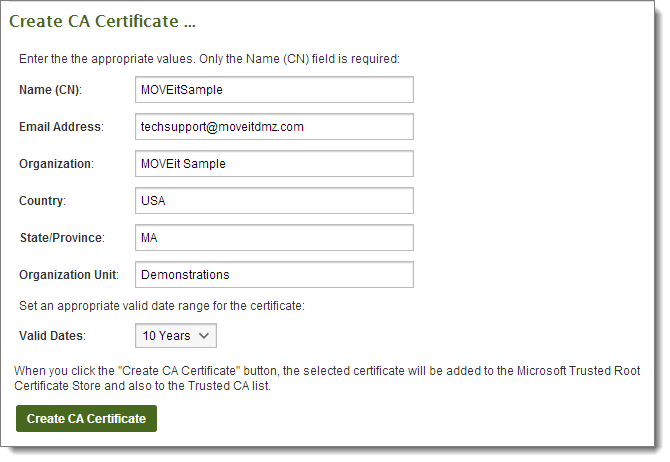
...you should create an organization client cert-signing CA certificate. To do so, click the Create CA link in this section and fill out the following form. This signing certificate will be visible on any client certificate you or any other administrator creates through the MOVEit Transfer web interface, so it is usually worth the time to provide meaningful answers to each question on the form. Also, the duration of this certificate should be LONGER than the duration of any particular client certificate you plan to issue now or in the future.
Once an organization's CA cert has been created, it is generally an invisible part of the client cert creation process; there is no CA cert drop-down or similar control to worry about.