Some users may be able to provide their SSH key fingerprints in advance. For example, most *nix users may use the ssh-keygen -l command to display their SSH fingerprint.
sshenduser@slackwarelinux:~$ ssh-keygen -l
Enter file in which the key is (/home/sshenduser/.ssh/id_rsa):
2048 63:bd:cc:05:ba:41:63:67:b1:b8:b6:6e:98:1f:10:67 /home/sshenduser/.ssh/id_rsa.pub
In other cases, users may only provide the public key itself. To manually add MD5 fingerprints or public keys provided by an end user, go to the User Profile page and click on the SSH Policy link.
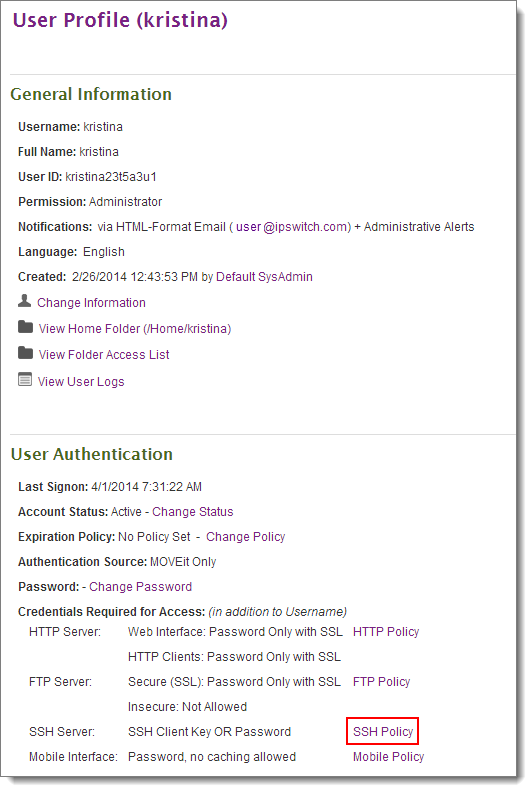
Then, scroll down to the Current SSH Keys section and click on Add (manually).
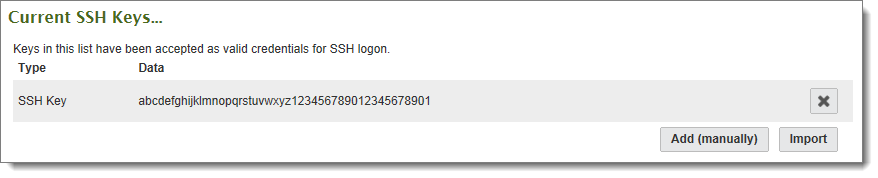
Next type (or hopefully, paste) the fingerprint or the entire SSH client's key into the text box provided.
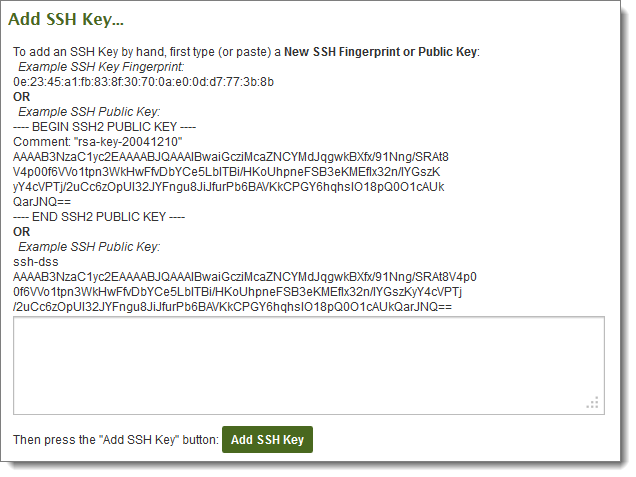
If a valid key was provided, a success message appears, and the key is listed in the Current SSH Keys section. A single user can be associated with multiple SSH keys; this is especially useful if a user is using the same username from multiple machines.
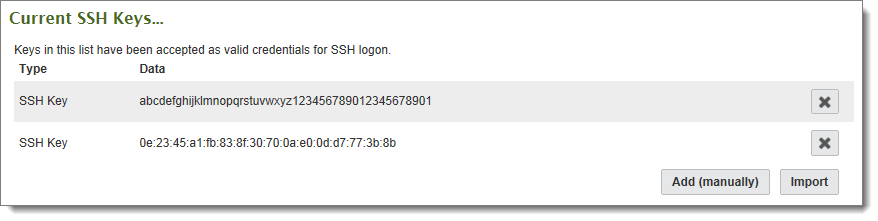
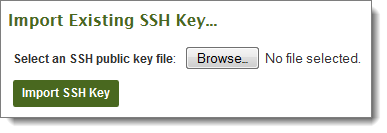
As an alternative, if you have the SSH key in a file on your PC, you can upload it directly by clicking on Import. Enter or browse to the SSH key file and press the Import SSH Key button. A successful import will display in the Current SSH Keys section.
Finally, to make sure the key will be solicited from the SSH client and/or that the key will be a required credential, see the Edit SSH Policy section and check the boxes appropriately.
If you plan on using OpenSSH in batch mode, you should use the following settings (require_key = yes, require_pass_with_key = no). If you want to enforce "two-factor" authentication, enable all of the following settings (require_key = yes, require_pass_with_key = yes).
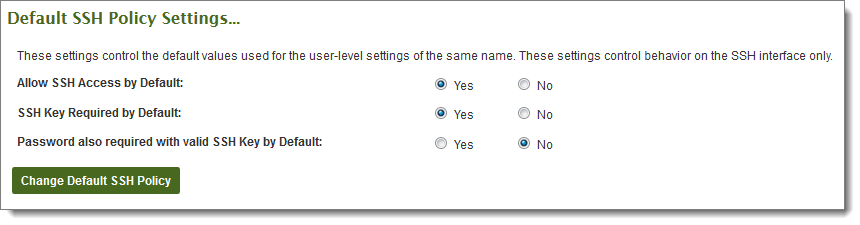
For detailed information about configuring the SSH Keys policy, please also see the Interface Policy documentation page.