Establishing an SSL-secured connection between a client and a server begins with a server certificate, which is used to both verify the identity of the server and securely negotiate a shared encryption key to use during the rest of the encrypted session. Consequently, all SSL servers require a server certificate. Because MOVEit Transfer uses SSL to secure its web-based interface (HTTPS) and its FTP interface (FTP/SSL), both of these interfaces require server certificates. Typically, the same certificate is used by both interfaces.
HTTPS and FTP/SSL clients know to trust specific machines because the certificates presented by remote servers are valid within a specific time period, match the hostname of the server to which the user connected, and are signed by a chain of trusted Certificate Authorities (CAs), such as Thawte or Verisign. (Without these protections, anyone could spoof an SSL-secured server with a self-generated server certificate!) So, for production environments, the use of a certificate signed by a well-known CA is highly recommended in order to give end users the most secure experience. For evaluation, development, and/or testing environments, however, self-signed test certificates are often used to eliminate the cost of purchasing a fully trusted certificate. In these cases, clients often present alert messages informing the user that something is not right with the certificate.
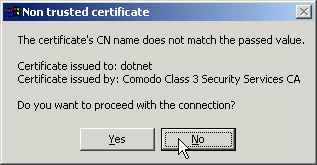
The following MOVEit Freely session shows this mechanism in action. During the SSL negotiation, MOVEit Freely notices that the remote certificate (for "dotnet") does not match the hostname that the client was told to connect to (192.168.3.15). The end user is prompted with a warning message.
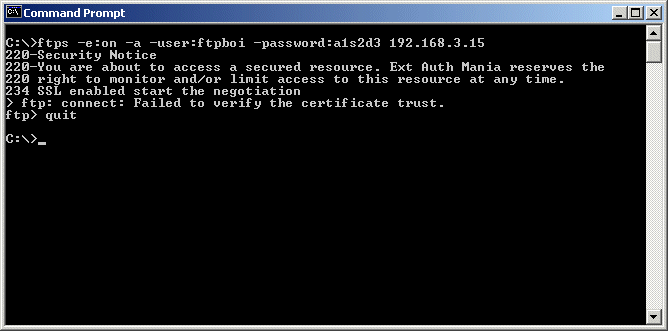
Assuming the end user decided not to complete the SSL connection to this server, MOVEit Freely displays a short description about why the SSL connection was refused.
On Windows platforms, server certificate requests and installations are typically performed through the IIS Internet Services Manager and its Web Server Certificate Server. For instructions on requesting a signed server certificate, see the Certificate Signing Requests documentation page.
After a certificate is available, it must be installed in both IIS and the MOVEit Transfer FTP server in order to be used by MOVEit Transfer. For instructions on installing a server certificate in IIS and the MOVEit Transfer FTP server, see the Assign Components documentation page.
After a certificate is installed and operational, back up the certificate so that it will be available if catastrophic system error occurs. The MOVEit Transfer Backup and Restore utilities can back up both client and server certificate information from a MOVEit Transfer server. For additional instructions on manually backing up certificates, see the Backing Up Server Certificates.