Single Signon allows your users to connect to MOVEit from their web browser, Ad Hoc Transfer for Outlook plug-in, or MOVEit Sync clients without having to enter a username and password each time.
MOVEit Server can use a third-party user directory (for example, Active Directory) to authenticate users. The Single Signon feature allows MOVEit Server to authenticate a user without requiring sign on, provided that user is already signed on (to the third-party user directory) using their network or corporate account.
MOVEit Server uses SAML (Security Assertion Markup Language) to exchange the authentication information with the user database.
This topic describes:
See Feature Focus - Single Signon for information about the requirements, a description of terms such as Service Provider and Identity Provider, and an overview of the process of configuring Single Signon.
For notes from our own testing with different identity providers, see SAML Single Signon Configuration Notes
For notes on troubleshooting common setup errors, see Troubleshooting Single Signon Issues.
Configure Local Service Provider/Relying Party Settings
These settings are used to identify the MOVEit Server and organization as the Service Provider, secure the SAML communications, and to determine how MOVEit will receive responses from the Identity Provider.
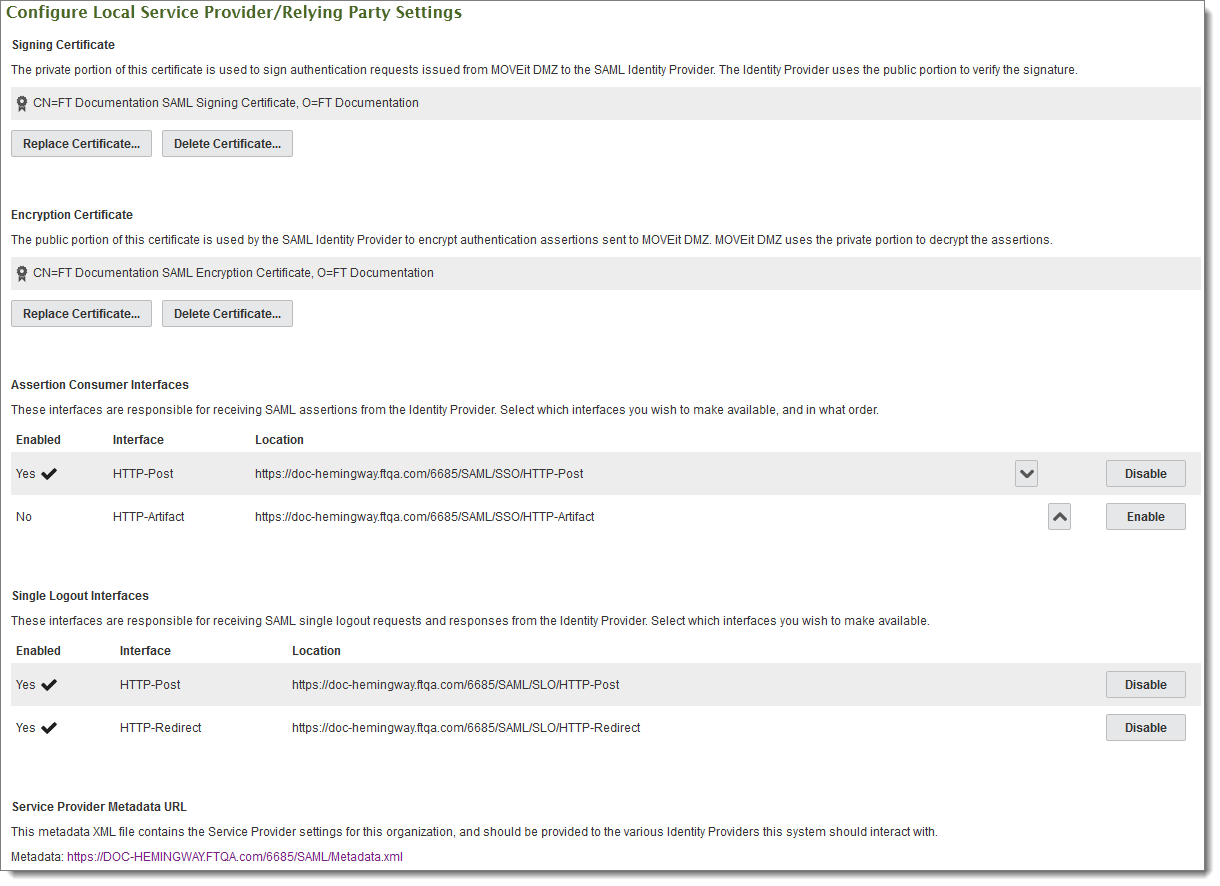
The MOVEit Server (Service Provider) sends a request to the Identity Provider. The private portion of the Signing Certificate assures that the request is from the MOVEit Server. The Identity Provider uses the public portion to verify the signature.
Click Create Certificate to open the Signing Certificate page. Enter the appropriate values, then click Create Certificate. Only the Common Name (CN) is required.
The new certificate is shown in the list.
You always have the options of replacing or deleting an existing certificate.
Note: While most servers require a Service Provider to have a signing certificate to sign requests, the encryption certificate is optional, though highly recommended for security.
The Identity Provider sends an "authentication assertion" or other response to the MOVEit Server. The public portion of the Encryption Certificate is used to encrypt the assertion. MOVEit uses the private portion to decrypt the assertion.
Click Create Certificate to open the Encryption Certificate page. Enter the appropriate values, then click Create Certificate. Only the Common Name (CN) is required.
The new certificate is shown in the list.
You always have the options of replacing or deleting an existing certificate.
This interface determines how MOVEit will receive the response (the user authentication) from the identity provider. You can enable multiple interfaces, in which case the identity provider will use the first interface listed whose binding it supports.
HTTP-Post is more widely supported, and is good enough for most situations, but is less secure than HTTP-Artifact because the assertion data passes through the client browser, giving that browser an opportunity to access data that may not be appropriate for the client to see. This can be compensated for by using an encryption certificate, but only if the identity provider supports encrypting response messages.
HTTP-Artifact is more secure, since the assertion data never passes through the client browser – only the reference "artifact" does. However, it is less widely supported, and also requires a direct connection between MOVEit and the identity provider, which some firewall rules may not allow from the DMZ network segment.
This interface determines how the identity provider sends a logout response or request to MOVEit. You can enable multiple interfaces, in which case the identity provider will use the first interface listed whose binding it supports.
Note: Shibboleth does not have sufficient support for single logout and Ipswitch does not recommend or support that feature with Shibboleth. It is not enabled by default in the Shibboleth Identity Provider, so MOVEit will not show the logout feature in the administrator interface. If it is enabled in the Identity Provider, we recommend you disable it here by clearing the Enabled option for all Single Logout interfaces.
When configuring the Identity Provider, you can provide this URL directly to the identity provider in the configuration settings. This requires that the identity provider has direct internet access to the MOVEit Server. If that's not the case, you can download the file and then upload it to the identity provider.
Note: This metadata file is updated when you change settings for a certificate, Assertion Consumer Interface, or Single Logout Interface. Make sure your identity provider is updated with the new file.
Add Federated Identity Providers
These settings add the identity providers (for example, an Active Directory Federated Services (ADFS) server) to which MOVEit Server can send an authentication request. The identity provider can be configured to offer two types of service: SAML single signon (available from the web browser), and WS-Trust (available as an external authentication method to other types of clients).
Note: If you are already using an external source for user authentication, we recommend that you use the same user store as your identity provider.
The Single Signon settings page shows the list of identity providers available (if any) to this organization.
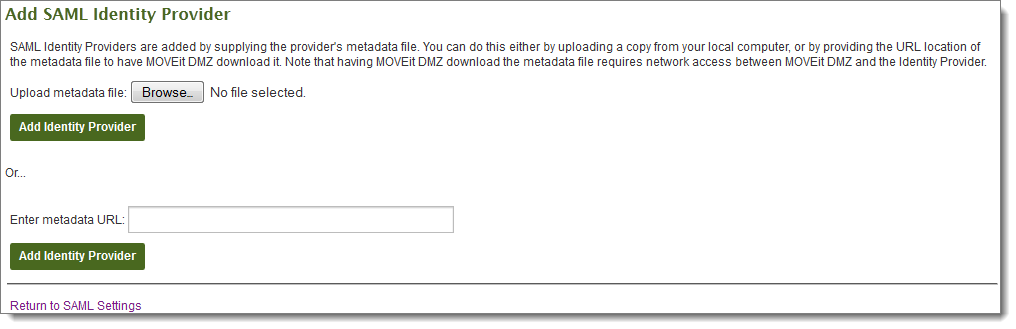
Identity providers that support SAML and WS-Trust authentication will provide a metadata file or URL that is used to configure them as a provider.
Or
Enter a URL for the provider's metadata, then click Add Identity Provider.
The entry for the identity provider is created and added to list of identity providers on the Settings (Single Signon) page.
Editing an Identity Provider
You can edit an identity provider entry to make changes to some of the settings, to select whether to use Single Signon or WS-Trust services, and to define whether and how a user account in the identity provider is created as a user in MOVEit.
To edit an identity provider, click the Edit action to the right of the entry.
Edit Federated Identity Provider settings.
These settings identify the identity provider and configure how it will communicate with the service provider (MOVEit). The settings you need to use will depend in large part on your third-part identity provider. See your identity provider's documentation for requirements. For notes from our own testing with different identity providers, see SAML Single Signon Configuration Notes.
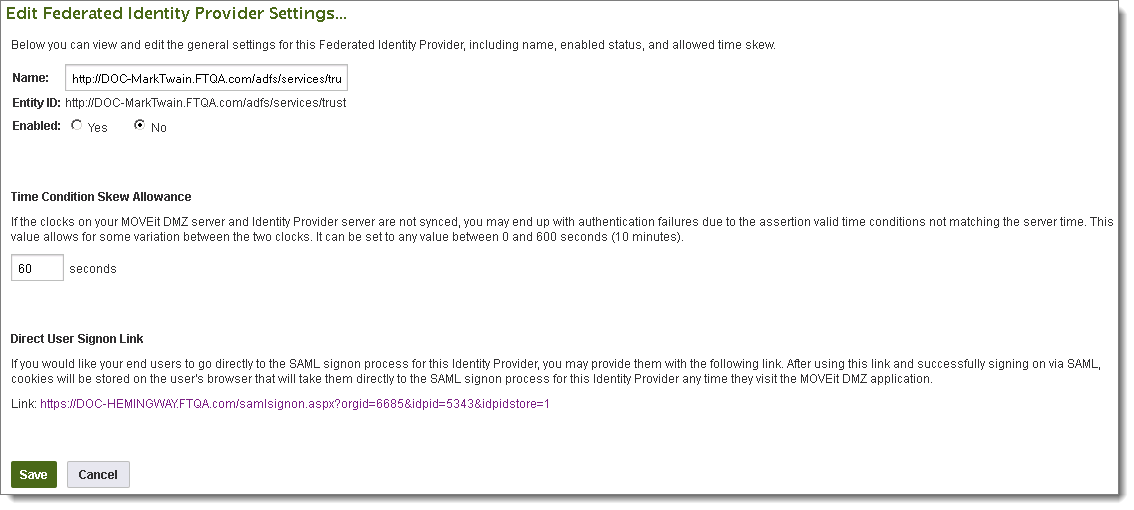
Name: Enter a descriptive name. This name will be shown on the sign on page if you have multiple identity providers for an organization. Users can choose among the providers.
Entity ID: The URL for the identity provider. This comes from the metadata file; it cannot be modified here.
Enabled: A newly added identity provider is disabled by default. If you want to enable it, click Yes.
Time Condition Skew Allowance: This setting can prevent unnecessary authentication failures by allowing for some variation between the MOVEit Server clock setting and the identity provider's clock setting. By default, this is set to 60 seconds.
Direct User Signon Link: The URL link shown here provides direct access to the SAML Signon page. If you provide users with this link, they can skip the step of accessing the standard Sign on page, and having to then select an identity provider. After successful signon using this link, cookies stored on the user's browser will take them directly to the SAML Signon page on subsequent access.
Note: After the initial signon, if a user is already authenticated to the identity provider, they will not need to sign on when accessing MOVEit.
Select Federated Identity Provider Services
These settings let you select which of the available services you want to use with this organization, including SAML Single Signon and WS-Trust Secure Token Authentication.
SAML Single Signon Service
The identity provider provides single signon services using the SAML 2.0 protocol. These services are for single signon from a browser.
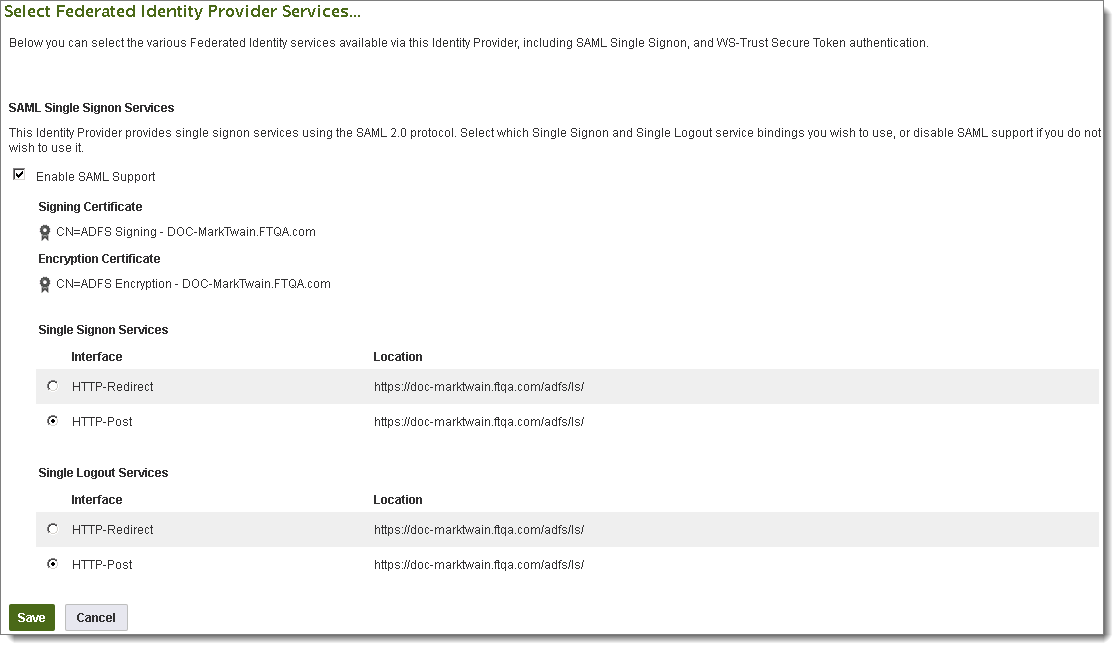
Enable SAML Support: Enable SAML single signon for this organization.
Signing Certificate: The certificate used to authorize responses from the identity provider. This comes from the metadata file; it cannot be modified here.
Encryption Certificate: The certificate used to encrypt responses from the identity provider. This comes from the metadata file; it cannot be modified here.
Single Signon Services: Sets the service that MOVEit Server uses to send authentication requests through the client browser.
Single Logout Services: Sets the type of service that MOVEit Server uses to send a logout request through the browser.
Note: The binding types for Single Signon and Single Logout services are essentially the same as those used in the Service Provider assertion consumer and single logout interfaces, though in this case, MOVEit Server is the sender and the identity provider is the receiver.
WS-Trust Security Token Service
Shows the WS-Trust external authentication sources, if any, that are configured to use this identity provider. WS-Trust service can request authentication tokens using provided username and password credentials. In this way, WS-Trust can provide external authentication from a client, for example, an FTP or SSH client.
Enabled: External authentication using WS-Trust is enabled for this organization.
Name: The name given to the WS-Trust authentication source when it was configured in MOVEit.
Edit: Click this button (to the right of the entry) to view or change the settings for this authentication source.
Add WS-Trust Authentication Source: Click this button to create a new WS-Trust source.
For information about creating or editing a WS-Trust source, see the External Authentication > WS-Trust (Authentication Only) page.
Edit Federated Identity Provider User settings
These settings configure how MOVEit will use the user information from the identity provider to create or modify the user account in MOVEit.
These settings will depend on which user attributes are available from your Identity Provider. You need to coordinate with the Identity Provider administrator. Note that the SAML Name ID attribute is always available from the Identity Provider.
Note: All newly created SAML Authentication accounts are provided a randomly generated password. The user or administrator can change this password, and the account can also be used to log into MOVEit through MOVEit authentication. If you are using Active Directory to do External Authentication, we recommend setting up LDAP against the same active directory ADFS uses. This will allow SAML and LDAP authentication to use the same credentials. We recommend setting up a mirroring external authentication source for FTP and SSH users because those interfaces cannot use SAML authentication.
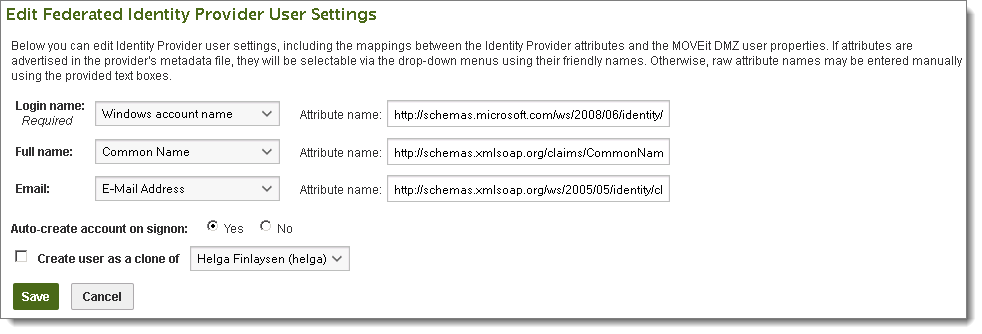
The Login name, Full name, and Email template settings determine what values will be used for the new user's login name, full name, and email address fields if they are added to the MOVEit user account.
Attribute name: The mapping of Identity Provider attributes to MOVEit Transfer user properties is done by selecting an attribute advertised by the Identity Provider in its metadata file. If an Identity Provider does not advertise the available attributes in the metadata file, you can use the Attribute name box to manually enter an attribute name in the user settings. The value to use in the attribute name is dependent on the Identity Provider. ADFS provides a schema based on URIs (for example, for Full name, use: http://schemas.xmlsoap.org/claims/CommonName). Shibboleth provides a schema based on the urn OID (for example, for Full name, use: urn:oid:2.5.4.3). Refer to the Identity Provider documentation for the appropriate schema and values to use.
Auto-create account on signon: By default, when a new user successfully signs on, an account will be created in MOVEit. If you want to disable it, click No
Create user as a clone of: Lets you (the administrator) select an existing user as a template for users created by this authentication source. When this setting is enabled, the selected user will be cloned to create the new user account.
Edit Federated Identity Provider Group settings
These settings configure how MOVEit will use group information from the identity provider to add a group setting for the new MOVEit user.
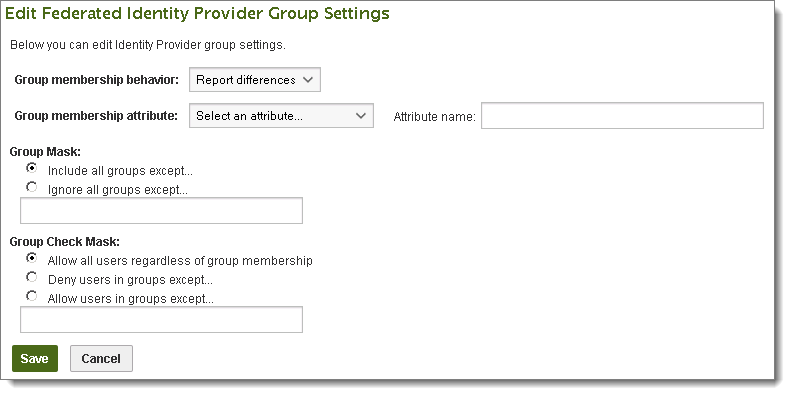
Group membership behavior: This setting determines how group memberships will be dealt with. When set to Ignore Differences, identity provider group memberships will be ignored, except in the case of the Group Check Mask setting. When set to Report Differences, differences between MOVEit group memberships and identity provider group memberships will be reported in the log. When set to Correct Differences, differences between MOVEit group memberships and identity provider group memberships will be corrected, if possible. MOVEit groups will NOT be added automatically, only group memberships. Groups existing on the identity provider but not on the MOVEit server will be noted as errors.
Group membership attribute: Select from the list of object properties to set the name of the group, if a group exists on the identity provider.
Attribute name: As with the user settings, if an Identity Provider does not advertise the available group attributes in the metadata file, you can use the Attribute name box to manually enter an attribute name for the group settings. Refer to the Identity Provider documentation for the appropriate schema and values to use.
Group Mask: These settings determine which groups will be included when syncing identity provider and MOVEit group memberships. The rule can be set to include groups except those matching one or more of the masks, or ignore groups except those matching one or more of the masks. The mask list can be one or more group name masks, separated by commas. Group name masks may contain the multiple-character wildcard *, and/or the single-character wildcard ?.
Group Check Mask: These settings operate similarly to the Group Mask settings, but determine the group memberships used by the system to determine if a user should be allowed to sign on or be automatically created (or mentioned in the error reports if the source is configured to not do auto-creation of users). By default, this setting is set to allow all users regardless of group memberships. The rule can also be set to deny users except those in groups matching one or more of the masks, or to allow users except those in groups matching one or more of the masks. As with the Group Mask setting, the mask list can be one or more group name masks, separated by commas. Group name masks may contain the multiple-character wildcard *, and/or the single-character wildcard ?.
Click Save to make your changes to the identity provider.
Update Federated Identity Provider Settings From Metadata
Similar to when you first add an identity provider using the metadata file, you can update the identity provider settings using this feature.
Or
Enter a URL for the provider's metadata, then click Update Identity Provider.
The entry for the identity provider is updated using the information in the metadata file.
Update Federated Identity Provider Security Token Service Endpoints from Metadata
When you create a WS-Trust authentication source, you add the security token service information using the metadata file from your identity provider. If the information on the token service changes (on the identity provider), you can update the settings using this feature, so that MOVEit will have the new token service information.
Or
Enter a URL for the provider's metadata, then click Update Identity Provider.
The entry for the identity provider is updated using the information in the metadata file.