MOVEit Transfer content scanning enables you to apply content screening at scale using a third-party virus scanner, a third-party DLP (Data Loss Prevention) pattern and expression engine, or both. Content scanning can be used as an extra layer of control to help inspect, analyze, track, and block inbound or outbound file transfer.
You can control data shared from/added to MOVEit Transfer based on user/user group and:
Content scanning is typically most necessary when MOVEit Transfer transfers occur across a firewall. Before MOVEit Transfer completes the data transaction, it forwards the data by way of Internet Content Adaptation Protocol (ICAP) to the appropriate scanner (AV or DLP). MOVEit allows or blocks the transfer based on the scan results.
Transfer Direction |
Scan Type |
Notes |
Outbound (share from MOVEit Transfer and Ad Hoc transfers) |
Data loss prevention |
DLP compliance. Logs or blocks sharing of DLP-rules identified content (for example, privileged or business sensitive data). |
Inbound (add to MOVEit Transfer) |
Anti-virus, data loss prevention |
Protective AV scan. DLP rules evaluation, tagging and determination of MOVEit Transfer user access based on rule sets. |
Third-party AV and/or DLP instances are managed and deployed separately from MOVEit Transfer. Note that different scanning servers might have different capabilities and performance capacity. A server can be configured to do AV, DLP or both. You can configure MOVEit to communicate with multiple different AV and DLP servers. You enable scanning at the system level, but you can have only one AV and one DLP server enabled at a time. You can then disable a specific AV or DLP process at the organization level.
Note: When both DLP and AV Content Scanning are each enabled and configured to block (or implicitly block due to timeout), you can use logs to diagnose which scan process returned the initial failure message that blocked the file from MOVEit Transfer.
The following major AV and DLP engines are compatible with MOVEit Transfer. Other scanning and compliance engines that support ICAP primitives could also work.
Anti-Virus Scanner |
Data Loss Prevention Scanner |
McAfee VirusScan Enterprise for Storage |
RSA Data Loss Prevention (DLP) |
McAfee Web Gateway |
McAfee Web Gateway* |
Sophos Anti-Virus Dynamic Interface (SAVDI) scanner |
Symantec DLP Suite (last tested with 15.x)* |
Symantec Protection Engine (last tested with 7.8.0.141) |
|
*DLP Blocked responses require additional configuration for McAfee and Symantec.Note: Check the MOVEit Transfer Release Notes for new additions to these lists and for any specific versioning requirements.
Anti-virus scan (SETTINGS > System > Content Scanning > Anti-Virus) allows scanning of incoming files using a remote anti-virus server. MOVEit Transfer submits incoming files to the anti-virus server using the ICAP protocol. Files that are clean are then passed into the MOVEit Transfer filesystem.
What happens when AV content scanning is enabled?
MOVEit Transfer scans uploaded files as follows:
Before You Begin
You need the following before you can enable virus scan:
Note: If you are using the AS2 Module to transfer files, be aware that content scanning does not apply to AS2 transfers. Use MOVEit Automation to scan AS2 transfers for viruses.
Configuring Anti-Virus Scanning for MOVEit Transfer Hosts
After you configure the anti-virus server, set up content scanning for your MOVEit Transfer organizations. Anti-virus settings apply to all MOVEit Transfer organizations on the system.
Note: For more information, see the topic titled Content Scanning.
Data Loss Prevention scans (SETTINGS > System > Content Scanning > DLP) send incoming data from file transfers and Ad Hoc transfers, including subject, note/body and attachments, to an external DLP server so that MOVEit Transfer can:
MOVEit Transfer uses the ICAP protocol to submit incoming data to the DLP server. The DLP server applies configured data protection policies as it scans the data. When the DLP server returns its response, MOVEit configurations determine whether to block, quarantine or allow the transmission. MOVEit logs all DLP policy violations returned by the DLP server.
Note: If you are using the AS2 Module to transfer files, be aware that content scanning does not apply to AS2 transfers.
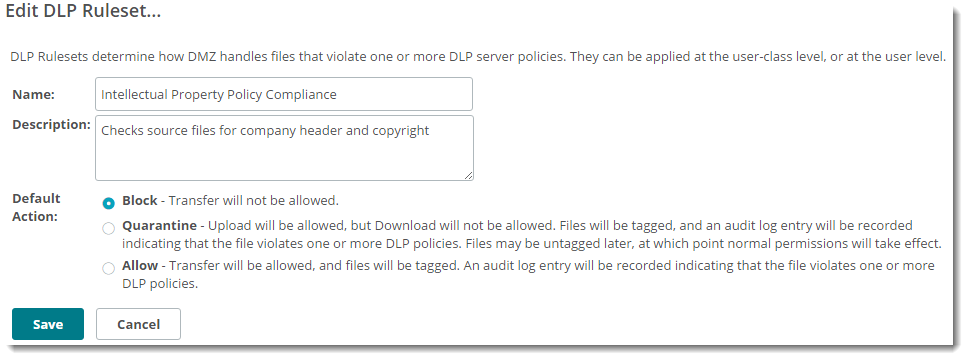
Configuring DLP Scanning for MOVEit Transfer Hosts
To implement Data Loss Prevention (DLP) scanning in MOVEit Transfer you must:
What happens when DLP content scanning is enabled?
MOVEit Transfer scans downloaded files as follows:
Important: Only one DLP scanner can be enabled on your system at any time.
If Content Scanning is enabled, MOVEit Transfer checks every few minutes to make sure the enabled AV and/or DLP scanner is available. This is part of the SysCheck routine (see Advanced Topics - System Internals - Scheduled Tasks), which can generate a built-in notification. It first checks the AV scanner and then the DLP scanner. If the either scanner is unavailable, SysCheck sends an email message to the Send Errors To email address and warns that the MOVEit Transfer server will not be able to transfer files until this situation is addressed. When the scanner becomes available again, SysCheck sends an email that states that scanning is now working.
Note: The system administrator should always test the connection when configuring a content scanner. They can also run MOVEit Transfer Check on demand.
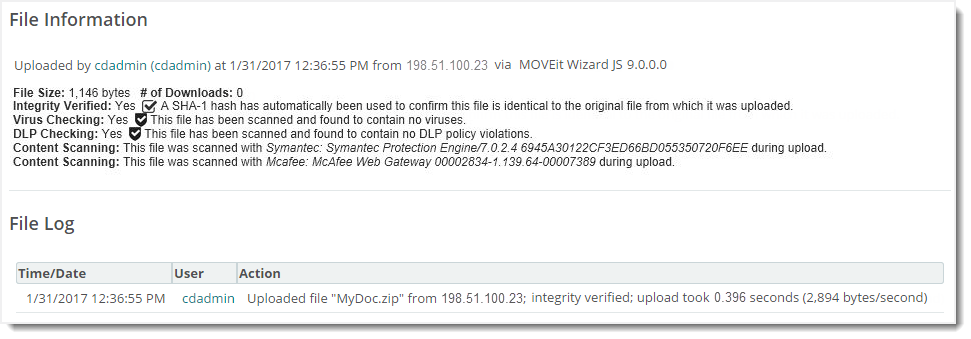
If a file was scanned, file detail pages show the anti-virus (AV) or the data loss prevention (DLP) server information.
In the following example, the first line of Content Scanning information is for the AV server and the second line is for the DLP server.
If a file fails the scan, an error message appears on the Home page of the user who uploaded the file.
Log file entries include status, user, and file attributes as well as policy violations (if applicable).
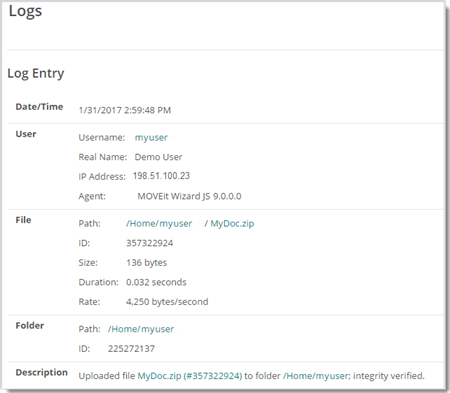
Error code numbers (6100 - 6103) are used to report AV errors. This will help when filtering logs. If an upload fails due to content scanning, the corresponding log table records will contain the AV server name and, if possible, the name of the virus.
Error code numbers 0 and 6150 are used to report DLP policy violations, as follows:
Notification macros for content scanning, if enabled, can report the scan results for both anti-virus (AV) and data loss prevention (DLP) scans.
AV and/or DLP information may be included in the following notifications:
The standard templates for these notifications do not include the content scanning results. You can add the macros that report the scan results by creating custom notification templates. Custom notifications are set in an organization via Settings | Appearance | Notification | Custom.
These reports show various types of content scanning activity. Two reports give specific information about scan results: Violations Blocked and DLP Violations (Allowed and Blocked). The remaining reports are maintenance reports that show aggregate counts.
If you are logged in as an organization administrator, the report shows scan results for your organization. If you are logged in as a system administrator, the report can show multiple organizations.
Note: Typically, reports may contain up to 30 days of online audit records and 30 days of online performance statistics, depending on how you run the scheduled cleanup tasks that archive the older data.