This section is important if you are planning to run MS SQL Server remotely or you have an existing MS SQL Server running remotely with a lesser protocol (SSL 3.0, TLS 1.0-1.1, for example). Many Data Security Standards (DSS), PCI 3.1, for example, require TLS 1.2 use to ensure data privacy and integrity all the way to the presentation layer.
![]() Before you proceed! The procedure that follows also includes steps you or your MS SQL administrator perform outside of MOVEit Transfer. Ipswitch is not responsible for changes to documentation, online resources, and hosted software that originate from Microsoft or other third-party vendors. The documentation that follows was accurate at the time of this MOVEit Transfer release.
Before you proceed! The procedure that follows also includes steps you or your MS SQL administrator perform outside of MOVEit Transfer. Ipswitch is not responsible for changes to documentation, online resources, and hosted software that originate from Microsoft or other third-party vendors. The documentation that follows was accurate at the time of this MOVEit Transfer release.
PCI 3.1 requires end-to-end TLS 1.2 with no backward-compatible or 'fall-back' connections. For example, 'fall back' connections can be negotiated between a client and server if the server supports a range of SSL/TLS versions and the client is running at an earlier protocol version that is less secure than TLS 1.2.
When you run a database server (such as MS SQL Server) that is on a different host than the MOVEit Transfer Server, you should ensure that the appropriate level of security is applied to your transactions with MS SQL Server.
To ensure that MOVEit Transfer database transactions with MS SQL Server are run over TLS 1.2, you must:
Running SQL Server over a TLS 1.2 connection involves the following steps:
Note: Always consider your security-availability tradeoffs, timing, and impact of these changes. Applying strict endpoint security policies can enable the possibility of refused connections to non-compliant or out-of-spec clients.
MOVEit Transfer Configured with a Remote MS SQL Server
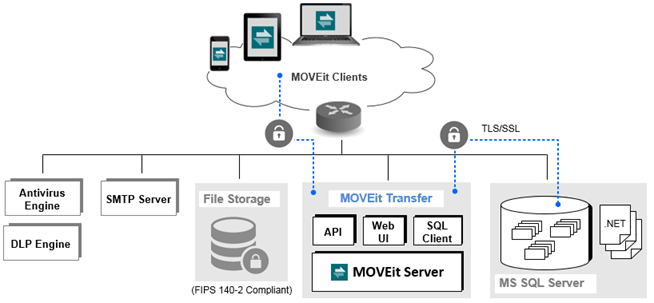
The following will enable the MOVEit Transfer Server to connect with TLS 1.2 to the remote MS SQL Server (using its SQL client). This is not a restrictive measure. (Applying this setting first ensures that clients will still be able to connect after Step 3 -- once you restrict communication at the MS SQL Server host).
MOVEit Transfer Server requires Windows Server, which by default uses the Schannel LIbrary (Schannel.dll) as part of its Security Support Provider Interface (SSPI). These instructions detail how to apply registry key values that Schannel expects for runtime configuration (TLS/SSL connections).
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL
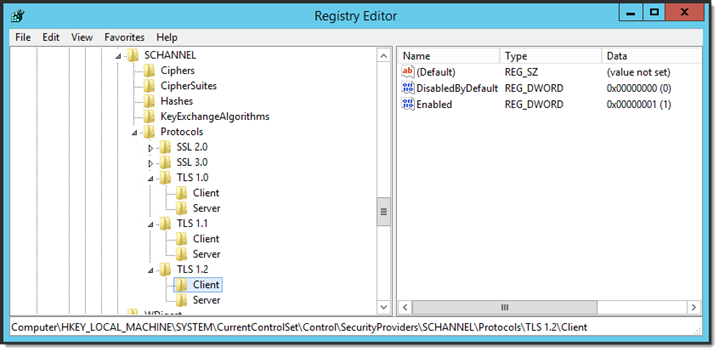
To limit MOVEit end-user client connections to use HTTPS and FTPS over TLS 1.2, you can use the MOVEit Transfer Configuration Utility. Ensure that TLS 1.2 is enabled, but you can unselect lesser protocols (The MOVEit Transfer Configuration Utility runs on the MOVEit Transfer Server Host).
MS SQL Server requires Windows Server, which by default uses the Schannel LIbrary (Schannel.dll) as part of its Security Support Provider Interface (SSPI). These instructions detail how to apply registry key values that Schannel expects for runtime configuration (TLS/SSL connections).
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL
SCHANNEL\Protocols\TLS 1.2\ClientSCHANNEL\Protocols\TLS 1.2\ServerOn the MS SQL host machine, ensure the value for the DWORD DisabledByDefault entry is set for the "TLS 1.2\Server" subkey to zero (0x0)--meaning false, to denote Schannel will use TLS 1.2 as a default. For the TLS 1.2\Server\DisabledByDefault subkey.
DisabledByDefault = 1 and Enabled = 0.Note: When a range of SSL protocols are enabled at the MS SQL Server host, an encrypted connection on one side can re-negotiate and downgrade or a per-connection basis to accommodate a lesser protocol running on the client host. To prevent this behavior, you must require encryption at the MS SQL server host and explicitly default the use of lesser security protocols to a false state.
![]() Full Microsoft KB article that details enabling TLS 1.2 can be found here.
Full Microsoft KB article that details enabling TLS 1.2 can be found here.
Next, open SQL Server Configuration Manager on the remote database host machine and change the connection policy to force SQL clients to connect to it using encryption.
Microsoft SQL Server Configuration Manager (version 2014 shown)
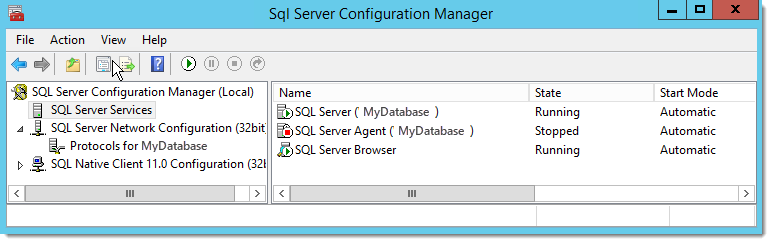
On the MS SQL Server Host machine:
--Where <my-sql-server-db> is the name of your Microsoft SQL Server DB Server.
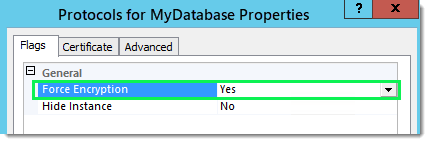
After you click Apply, a pop-up dialog reminds you that you must restart the database server for the changes to take effect.
For the last step, use a MOVEit Transfer client to generate request traffic with the MOVEit Transfer Server and send transactions to the remote MS SQL database.
ip.addr == <transfer-server-ip-address>
TDS exchanges (such as an SQL Query) between MOVEit Transfer Server host and the MS SQL Server should show TDS traffic with TLS protocol data unit information (SQL queries and batch queries should not be readable).
![]() After you ensure your TDS traffic is encrypted with TLS, you can check that the ciphers available to the MS SQL Server host are strictly TLS version 1.2. You can do this with port scanners such as Nmap. For example, this command:
After you ensure your TDS traffic is encrypted with TLS, you can check that the ciphers available to the MS SQL Server host are strictly TLS version 1.2. You can do this with port scanners such as Nmap. For example, this command: nmap --script ssl-enum-ciphers -p 1433 <my-sql-server-host> returns the version of TLS along with warnings (if applicable).