The MOVEit Transfer Config utility is used to configure the MOVEit FTP server. (Users, groups, folder settings and the like are generally maintained through the Web Interface or MOVEit API.) Run the configuration program by choosing the Start menu shortcut MOVEit Transfer Config. This program uses a tabbed dialog to group the settings by function.
MOVEit FTP will immediately apply configuration changes the next time a new connection is received.
Exception: If changes are made to the FTP explicit or implicit ports, the MOVEit FTP service must be restarted for these changes to take effect.
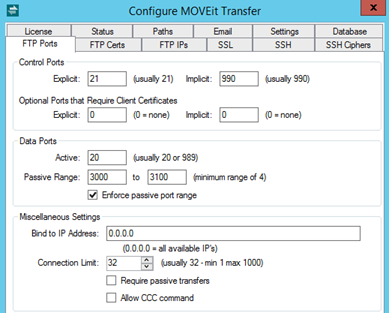
You can define the ports used for controlling the FTP session.
![]() Explicit SSL connection ports wait to move to SSL until the AUTH command is used explicitly. Implicit connections do not need the AUTH message indicator because they expect the connection handshake to begin immediately with SSL protocol messaging.
Explicit SSL connection ports wait to move to SSL until the AUTH command is used explicitly. Implicit connections do not need the AUTH message indicator because they expect the connection handshake to begin immediately with SSL protocol messaging.
If your MOVEit Transfer server expects connections from clients with valid client certs, you must define your control ("connection") ports here.
![]() If you specify values other than '0' (zero) for Client Certs ports, MOVEit Transfer FTP requires a connecting client to be known to the server before a session can take place. For example, some sites embed client certs by way of smart cards.
If you specify values other than '0' (zero) for Client Certs ports, MOVEit Transfer FTP requires a connecting client to be known to the server before a session can take place. For example, some sites embed client certs by way of smart cards.
You can control the range of ports used to send/receive FTP data.
Passive Range: This is a feature to help sites that position a firewall between the MOVEit FTP computer and end users. When running in passive mode, FTP dynamically creates ports on which it listens for data connections from the remote FTP clients. In order to accommodate this behavior, network administrators must allow incoming connections on these ports. The port numbers used for this purpose are normally greater than 1023, but otherwise cannot be predicted in advance. Because sessions are encrypted, there is no way for a firewall to learn the port numbers immediately. Therefore, firewalls must normally be configured to allow outside users to connect to any port greater than 1023.
To address this, MOVEit Transfer FTP provides an option to enforce the range of ports that it will choose when in passive mode. If you choose this option, you must select a range of ports on which FTP will listen for data connections; for instance, 2000-2200.
The advantage of this option is that is allows your network administrator to open up only a limited range of ports to which remote FTP clients can connect. This provides a modest increase in security on your site (when compared to opening up a very large number of ports).
By default, the configured range is 3000-3100. Most sites will want to keep this range down to 4-100 consecutive ports. (The range used by most Windows client applications is 49152 - 65535).
Warning: CCC carries the security risk of exposing file names, folder paths and other control information to anyone listening.
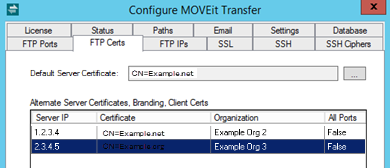
Default Server Certificate: The default certificate is the SSL server certificate used for transport encryption. This certificate must have already been created and installed on the system. Typically, you will use the same certificate that you have already installed on your MOVEit web server.
Certificates are normally purchased through a certification authority such as Thawte or Verisign. However, free software is available to allow you to create your own at no cost. For example, the Certificate Services component of Windows Server can be used to create certificates. Using certificates you created yourself is generally not recommended, because client programs consider them to be non-trusted, and raise warning dialogs.
Alternate Certificates, Branding, Client Certs: Alternate SSL server certificates may be assigned to each IP address of your MOVEit server. This is a way to have MOVEit FTP use a different certificate for connections through different networks.
Note: If you want to run a secure "multi-homed FTP server", you might need to configure these options. You cannot use alternate server certificates if you decide to bind to a single IP address.
For example, if MOVEit is connected to the internet through one network interface card (NIC) and to a local intranet through another NIC, you can give an alternate certificate for use by connections through the second NIC.
The Alternate Certificates, Branding, Client Certs list displays the columns Server IP and Certificate, as the alternate certificate is paired with a specific local IP address or IP mask.
In addition, the list has these columns:
Click Add to open the Add FTP Alternate Certificate dialog.
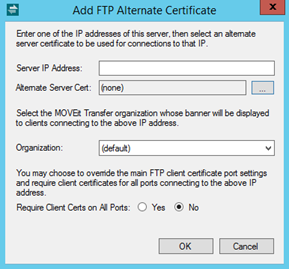
In addition to linking particular certificates with particular IP addresses, you may also link a particular Organization to a particular IP address to present a different signon banner to FTP users rather than the default Org's banner.
You may also decide to enforce more stringent client certificate requirements, that is, require client certs on all FTP command ports for the particular alternate IP address (overriding the client certificate port settings of the default IP address binding, which is configured on the FTP Ports tab). If Yes is selected for this option in the dialog box, back in the Alternate Certificates, Branding, Client Certs list, the All Ports column will show "True" for that certificate entry.
In the Alternate Certificates, Branding, Client Certs list, you can select a certificate and either click Edit (which opens the Edit FTP Alternate Certificate dialog) or Remove.
Server Certification Selection List
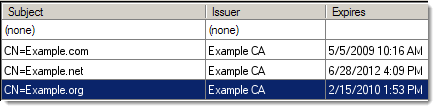
Clicking any of the "..." server certificate browse buttons opens a list of server certificates to select. Select a certificate with an Expires date later than today. To select a certificate, double-click it, or select it and click the OK button.
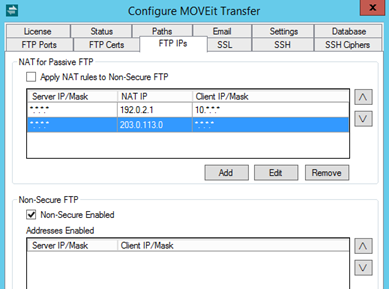
Whether to map IP addresses for Network Address Translation (NAT) is an advanced feature for sites that use a firewall to do "NAT'ing". It applies only to passive mode transfers. If you choose to use this feature, you should provide a list of NAT rules in most-specific-to-least-specific order with a "catch-all" at the bottom. Each NAT rule consists of an IP mask, and the external IP address to use for clients matching that mask. Each mask has the form "m.m.m.m", where each m is a decimal number like 208, or a * wildcard. Each external IP address is the usual dotted decimal number and should be the external IP address to which the firewall maps your FTP server.
The most common configuration resembles the following example. This provides an internal IP address (10.2.1.33) to clients connecting from internal clients (10.*.*.*), but provides an external IP address to all other (external) clients.
ServerIP=*.*.*.*, NatIP=10.2.1.33, ClientIPs=10.*.*.*
ServerIP=*.*.*.*, NatIP=66.170.5.130, ClientIPs=*.*.*.*
Another configuration involves "multihoming" where different hostnames have been mapped to different external IP addresses 66.170.5.130 and 66.170.5.131) which come in to two different internal IP addresses (10.2.1.33 and 10.2.1.34) on the same MOVEit Transfer machine. In this case we want to return the correct IP address for each external connection while still returning the correct address for internal clients.
ServerIP=10.2.1.34, NatIP=10.2.1.34, ClientIPs=10.*.*.*
ServerIP=*.*.*.*, NatIP=10.2.1.33, ClientIPs=10.*.*.*
ServerIP=10.2.1.34, NatIP=66.170.5.131, ClientIPs=*.*.*.*
ServerIP=*.*.*.*, NatIP=66.170.5.130, ClientIPs=*.*.*.*
If your NAT rules consist solely of the rule:
ServerIP=*.*.*.*, NatIP=208.33.33.33, ClientIPs=208.*.*.*
...then a client accessing any IP address your machine from 208.122.3.4 will be told to perform passive transfers to 208.33.33.33, even though the actual internal IP address of your FTP server may be something completely different, for example, 192.168.1.10. Clients accessing your FTP server from outside the 208.* domain will be given the actual address of your FTP server (192.168.1.10).
If you have more than one NAT rule, you can change the order of evaluation by using the up- and down-arrow buttons to the right side of the list.
Rules to handle localhost or 127.0.0.1 addresses are not necessary. Connections from these addresses will always be instructed to connect their data channels to the same address.
Specifies whether to allow access from Non-Secure FTP clients. This feature lets you open the FTP server up to clients that do not use secure FTP (encrypted) transfers. This significantly reduces the security of MOVEit because data can potentially be "sniffed" on the network. But in some circumstances, such as inside a company's intranet, that level of security is not important. Or, in other cases, there is no other way to transfer securely from a certain client. In order to open FTP up to non-secure transfers, you need to not only check the enabling box, you also need to add the specific IP addresses or IP masks that are allowed to perform these non-secure transfers. Non-secure mode is enabled using pairs of IP addresses. Each pair consists of a local IP address (or mask) on the MOVEit server, (corresponding perhaps to a specific network interface), and an external IP address or mask corresponding to a network FTP client. As with the NAT list, you can move entries up and down within the list.
Before any of the configured IP addresses will be allowed to connect insecurely, the Non-Secure FTP Enabled checkbox MUST be checked (and confirmed).
This option MUST be enabled before any user-level "allow non-secure FTP" interface setting can be used.
Warning: Non-Secure FTP carries the security risk of exposing usernames, passwords, file data, file names, folder paths and other control information to anyone listening.
The MOVEit FTP server's diagnostic log settings can be changed on the Status tab of the configuration utility. For more information about this tab, see the Configuration Utility topic.
The MOVEit FTP server communicates with MOVEit using the Machine URL configured on this tab. For more information about this tab, see the Configuration Utility topic.
The initial security banner and notice will be provided in the default language of the default organization, or in English, if no default organization exists. (See the Miscellaneous system settings page for more information about default organizations.) To change the language of the initial security banner and notice, log on to default organization on the system as an org admin. Change the org's default language using the International settings page.
In the MOVEit Transfer Config utility, you can use the SSL Tab to select the SSL versions and SSL encryption methods.