MOVEit uses Microsoft's built-in TLS/SSL security support provider (Schannel.dll). In all supported versions of Windows, there are several available protocols and cipher suite options enabled by default. Not all of them will meet your security and compliance needs. For example, the much older SSLv2 protocol is enabled by default on the server but is not allowed for PCI-compliant web applications. Be careful to choose the right mix of strong encryption methods and acceptable client support.
Warning: Changing the cipher suites or TLS/SSL versions can affect any applications that use TLS/SSL. Be sure you are aware of the requirements of other applications before making a change. For example, if you select SSL 2.0 only, MOVEit will not be able to connect to the Microsoft SQL database. The intent of this dialog is to allow you to avoid using a weak cipher where not allowed by PCI, FIPS, or other standards.
In the Configure MOVEit Transfer program, you can use the SSL tab to select the cipher suites and SSL versions that can be used when establishing an SSL session. To run the configuration program, use the Start menu shortcut MOVEit Transfer Config.
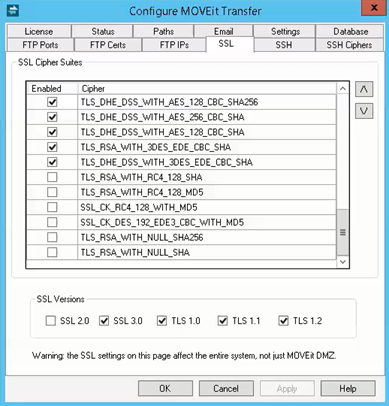
The SSL Cipher Suites section allows you to choose which cipher suites are permissible, and their order of preference. A cipher suite is a named combination of authentication, encryption, and message authentication code (MAC) algorithms used to negotiate the security settings. By default, all ciphers suites enabled in the base Windows OS are enabled.
Note: Both the client's and the server's preferences are taken into consideration when choosing the actual cipher for a given session. Though the server's first choice won't always be chosen, the cipher that ends up being chosen will always be in the set of allowed algorithms on both sides.
Select the Enabled check box to disable a selected entry or to enable an unselected entry.
Entries closer to the top of the list are given preference over entries lower down. Use the arrow buttons to move entries up or down in the list. Even if you must permit weaker cipher suites, you should always put the stronger ones at the top of the list.
SSL Versions are shown at the bottom of the SSL Tab. The default selections include SSL 2.0, SSL 3.0, and TLS 1.0. The versions selected determine the cipher suites that are available.
Select a check box to disable a selected version, or to enable an unselected version.
Note: After any SSL Version change, you need to reboot the system before the change takes effect.
Note: Be aware that the security policy setting System cryptography: Use FIPS compliant algorithms for encryption, hashing, and signing will restrict the available cipher suites and protocols. For example, TLS 1.0 will always be enforced.
Note: Be aware that the setting SSL cipher suite order via Group Policy will override any changes made to cipher suite order on this tab.
To test SSL changes, first obtain a copy of OpenSSL. You can get OpenSSL.exe from the OpenSSL Project. See the following examples.
Type the commands that are shown in purple. Look for the results in red.)
Using OpenSSL to verify SSL 3 is running on a remote server
This test was performed against our moveit.stdnet.com support server. It shows that a connection using SSL version 3, using a negotiated symmetric encryption algorithm called "RC4" and a "hash" algorithm called "MD5".
D:\OSOmissions>openssl s_client -connect moveit.stdnet.com:443 -ssl3
Loading 'screen' into random state - done
CONNECTED(000002AC)
depth=0 /C=US/ST=Wisconsin/L=Madison/O=Standard Networks/OU=MOVEit Site/CN=moveit
t.stdnet.com
verify error:num=20:unable to get local issuer certificate
verify return:1
depth=0 /C=US/ST=Wisconsin/L=Madison/O=Standard Networks/OU=MOVEit Site/CN=moveit
t.stdnet.com
verify error:num=27:certificate not trusted
verify return:1
depth=0 /C=US/ST=Wisconsin/L=Madison/O=Standard Networks/OU=MOVEit Site/CN=moveit
t.stdnet.com
verify error:num=21:unable to verify the first certificate
verify return:1
---
Certificate chain
0 s:/C=US/ST=Wisconsin/L=Madison/O=Standard Networks/OU=MOVEit Site/CN=moveit.s
tdnet.com
i:/C=ZA/ST=Western Cape/L=Cape Town/O=Thawte Consulting cc/OU=Certification S
ervices Division/CN=Thawte Server CA/emailAddress=server-certs@thawte.com
---
Server certificate
-----BEGIN CERTIFICATE-----
MIIC5DCCAk2gAwIBAgIDCeniMA0GCSqGSIb3DQEBBAUAMIHEMQswCQYDVQQGEwJa
QTEVMBMGA1UECBMMV2VzdGVybiBDYXBlMRIwEAYDVQQHEwlDYXBlIFRvd24xHTAb
BgNVBAoTFFRoYXd0ZSBDb25zdWx0aW5nIGNjMSgwJgYDVQQLEx9DZXJ0aWZpY2F0
aW9uIFNlcnZpY2VzIERpdmlzaW9uMRkwFwYDVQQDExBUaGF3dGUgU2VydmVyIENB
MSYwJAYJKoZIhvcNAQkBFhdzZXJ2ZXItY2VydHNAdGhhd3RlLmNvbTAeFw0wMzAx
MTQxOTI0MDlaFw0wNTAyMDcyMjA0MThaMIGBMQswCQYDVQQGEwJVUzESMBAGA1UE
CBMJV2lzY29uc2luMRAwDgYDVQQHEwdNYWRpc29uMRowGAYDVQQKExFTdGFuZGFy
ZCBOZXR3b3JrczEUMBIGA1UECxMLTU9WRWl0IFNpdGUxGjAYBgNVBAMTEW1vdmVp
dC5zdGRuZXQuY29tMIGfMA0GCSqGSIb3DQEBAQUAA4GNADCBiQKBgQCncZmY8wgl
6avPENjI3b7CDrIBVVYlBXs8eA+dZGXBQ6NfS2pP3bAG2Mi4atFp49EY4WKwz/CV
tyrPeTdyZOxkuIZkiC5wH+iAFJg3J6DwpzkkVPMI4lXxiOnd6cke4ZZupwUPR/4R
w/CW2WWClQlELxv2FgOzEkqFPazzpMEWcQIDAQABoyUwIzATBgNVHSUEDDAKBggr
BgEFBQcDATAMBgNVHRMBAf8EAjAAMA0GCSqGSIb3DQEBBAUAA4GBAK7JtOFt5fW3
fEBc14waYvuzKVTSh+zBuskRSVt3C4uUtxLqMBbswUmx3n29TpHInmNoL+iXZJz2
IZEaGkMwLMXJxB0MwD19mlrK9EhZDAOI9ZUNWnZ+1gWep4SpFODFP7UOSzuU0s1z
34xKpkqtN3nzR5iRkSEZU7nxPyl29CM0
-----END CERTIFICATE-----
subject=/C=US/ST=Wisconsin/L=Madison/O=Standard Networks/OU=MOVEit Site/CN=movei
t.stdnet.com
issuer=/C=ZA/ST=Western Cape/L=Cape Town/O=Thawte Consulting cc/OU=Certification
Services Division/CN=Thawte Server CA/emailAddress=server-certs@thawte.com
---
No client certificate CA names sent
---
SSL handshake has read 904 bytes and written 304 bytes
---
New, TLSv1/SSLv3, Cipher is RC4-MD5
Server public key is 1024 bit
SSL-Session:
Protocol : SSLv3
Cipher : RC4-MD5
Session-ID: F50400000B9D20B4B6D0605AE6BE88573A3A4D7503D861281CF0691B0FDAFC62
Session-ID-ctx:
Master-Key: B556889277515F16889D048A003B1C827BF0F7DF01E2EAEEE7BD45F518912B24
F1FE19762809BA770E215C8FFA99C330
Key-Arg : None
Start Time: 1075827324
Timeout : 7200 (sec)
Verify return code: 21 (unable to verify the first certificate)
---
(ctrl+c)
DONE
Using OpenSSL to verify SSL 3 is NOT running on a remote server
This test was performed against an internal IIS server after SSL3 was manually disabled.
D:\OSOmissions>openssl s_client -connect localhost:443 -ssl3
Loading 'screen' into random state - done
CONNECTED(000002AC)
1484:error:1409E0E5:SSL routines:SSL3_WRITE_BYTES:ssl handshake failure:./ssl/s3
_pkt.c:529:
By default, Microsoft SSL only logs serious SSL connection errors to the event log. However, you can change the level of SSL connection information logged here by making a Windows registry change. First, make sure the following REG_DWORD registry entry exists. If it does not, add it.
HKEY_LOCAL_MACHINE\System\CurrentControlSet\Control\
SecurityProviders\SCHANNEL\EventLogging
One of the following values should be used in this field.
You must restart your computer for this value to take effect. For more information, see the Microsoft Support site under the "How to enable schannel event logging" topic (#260729)