As a SysAdmin user, you can apply secure HTTP directives ("HTTP response headers") at the MOVEit Transfer web service (SETTINGS > System - HTTP Headers: Security Headers). Major web browsers that comply with industry standards will use these to block/mitigate WebUI session vulnerabilities. These optional parameters that you can control from MOVEit Transfer leverage industry standard directives with hardened options.
![]() The MOVEit Transfer WebService inserts these directives into the HTTP message header. To see if they are currently sent, open the developer tools view of the browser where a new MOVEit Transfer WebUI session is open. For example, in Chrome you can access HTTP response headers by opening tools view with the F12 key, then look under Network >
The MOVEit Transfer WebService inserts these directives into the HTTP message header. To see if they are currently sent, open the developer tools view of the browser where a new MOVEit Transfer WebUI session is open. For example, in Chrome you can access HTTP response headers by opening tools view with the F12 key, then look under Network > ![]() > Headers.
> Headers.
Received HTTP Response Header Viewed from a WebUI Session Using Chrome Developer Tools (Content-Security-Policy settings highlighted)
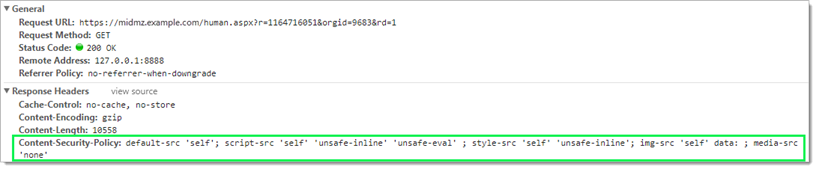
These options ensure session communication between the MOVEit Transfer WebUI (or equivalent) and the pages it requests from the MOVEit Transfer server host use a secure transport protocol and are not vulnerable to content or pages backfilled from a different origin server. Using these header messages with major browser vendors ensures integrity and confidentiality of the pages viewed during a typical WebUI session.
Setting this HTTP header flag... |
does this... |
Other details... |
Include Content-Security-Policy Header |
Apply a policy that allows browsers of this site to load resources from designated server origins and endpoints. If no policy is defined, Same-Origin (link to RFC) policy will be enforced. |
Restricts content origin and types for the current session to OWASP suggested settings. |
Include HTTP Strict Transport Security Header |
Direct WebUI or equivalent session client to only contact the MOVEit Transfer web service only by way of HTTPS.
|
Strict use of HTTPS prevents HTTP downgrade attacks and helps to ensure that other security policy settings are neither revealed nor compromised. |
Include X-XSS-Protection Header |
Direct all WebUI clients to filter out or block injection of JavaScript or popups, also referred to as cross-site-scripting (XSS) that could potentially pull in content from a different, less-secure, or compromised site. |
For purposes of hardening, when enabled, this directive instructs clients to block pages that exhibit some signature of XSS. |