Through support of SAML 2.0 functionality, you can customize MOVEit to use a third-party "identity provider" to authenticate MOVEit users. An identity provider is an application that provides identity assertions by way of SAML and in response to authentication requests from a service provider. MOVEit acts as the service provider. In this deployment pattern, MOVEit can be referred to as the "SAML consumer."
Single Sign-on Option (MOVEit Mobile shown)
|
Single Sign-on Option (Web UI shown)
|
User Selects Identity Provider (Web UI shown)
|
Security Assertion Markup Language (SAML) 2.0 provides a mechanism for exchanging authentication data among secure web domains. SAML 2.0 is an XML-based protocol and an OASIS standard. For more information about SAML, refer to SAML Overview from OASIS.
![]() The SAML single sign-on service allows users to connect to MOVEit using a third-party identity provider. This enables users signed on to their network or corporate account to access MOVEit without needing to enter additional MOVEit specific credentials.
The SAML single sign-on service allows users to connect to MOVEit using a third-party identity provider. This enables users signed on to their network or corporate account to access MOVEit without needing to enter additional MOVEit specific credentials.
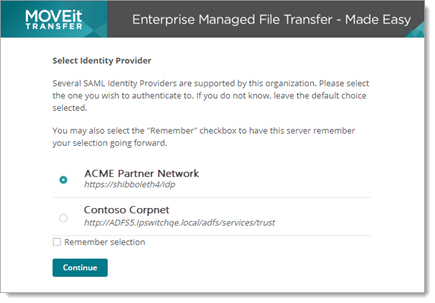
MOVEit supports authentication from the following as the Identity Provider:
![]() We tested Windows Server 2019 AD FS (sometimes referred to as "ADFS 5.0") and Windows Server 2016 AD FS (sometimes referred to as "ADFS 4.0") with MOVEit Transfer.
We tested Windows Server 2019 AD FS (sometimes referred to as "ADFS 5.0") and Windows Server 2016 AD FS (sometimes referred to as "ADFS 4.0") with MOVEit Transfer.
Authentication with these Identity Providers has been tested and is supported. Other identity providers not listed here that support the SAML 2.0 protocol should also work with MOVEit.
Single Sign-on Option (Desktop Client shown)
|
Single Sign-on Option (Mobile Client shown)
|
Single Sign-on Option (Web UI shown)
|
When Single Sign-on is available, a user session works like this:
If the user is not already signed-in, a login page displays the option to use single sign-on.
Identity provider redirects browser to MOVEit Server with an authentication assertion.
MOVEit validates the assertion and signs the user on.
To set up Single Sign-on for users signing on to MOVEit Transfer web interface, you need to do the following:
Note: If you are using Active Directory as your user store (configured in User Authentication as External Only), then you can use that same user store with the Identity Provider. You will need to install and configure ADFS so that Active Directory can act as the Identity Provider.
When Single Sign-on is configured for the Outlook plug-in and MOVEit Sync clients, a user session works like this:
To set up Single Sign-on for users signing on to MOVEit Transfer from the Outlook plug-in and MOVEit Sync clients, you need to use ADFS as the Identity Provider. Both clients can use the MOVEit Transfer Single Sign-on services to sign on using a Windows domain account. Currently, only ADFS supports using Windows Authentication.
Assuming the Service Provider and Identity Provider settings are configured (see "Single Sign-on for MOVEit web interface"), Outlook plug-in and MOVEit Sync users can complete the configuration as described in the following procedure.
If MOVEit is configured for Single Sign-on through an Identity Provider using the same Domain Controller that your users use to perform Windows Authentication, it is possible to configure the Outlook plug-in and MOVEit Sync clients to automatically sign those users on without requiring credentials. To achieve this, follow these steps:
Note: This procedure must be run on the end-user computer.
Note: If the client was installed using silent install with the Windows Authentication and Organization ID properties already set, then the user will not need to sign-on. The user will be signed on when they log into their Windows account.
Note: MOVEit Transfer Clients (Sync, MOVEit Ad Hoc, and so on) can also be configured to use WS-Trust authentication, allowing users to sign on using Windows Authentication when ADFS is not available, for example, if the user signs on from a home network. For information about setting up WS-Trust Authentication, see the "Single Sign-on for FTP and SSH Clients" section.
WS-Trust authentication allows MOVEit to directly authenticate users using the same identity provider used for single sign-on with SAML. We recommend configuring a WS-Trust authentication source in addition to SAML Single Signon services for customers who want to provide FTP and SSH access to MOVEit using the same credentials the user uses to authenticate to their Identity Provider.
Currently, only the ADFS Identity Provider supports WS-Trust.
If you have a requirement to use WS-Trust, you can do so by setting up the following components:
Note: If you have already configured the Service Provider settings and added ADFS as the Identity Provider, you do not need to complete this setup again.
After you have configured the single sign-on components, you need to provide the following information to your end-users.
Note: If you use the ADFS Identity Provider and want to avoid silent re-authentication by the browser, you can configure HTML form-based sign-on. For more information, see the procedure below.
Depending on how the Identity Provider is configured, many browsers will silently re-authenticate the user when they initiate the next session, which may be the desired behavior. However, if you want users to re-enter their password after doing a full SAML sign off, you can configure HTML Form-based sign-on. This procedure describes how to configure form-based sign-on for ADFS.
microsoft.identityServer.web localAuthenticationTypes element.