It helps to distinguish between an anti-virus that runs on the local Transfer server and an anti-virus solution used for dedicated content scanning. When you consider anti-virus solutions for MOVEit Transfer, local anti-virus refers to protecting the MOVEit Transfer machine, while content scanning examines uploaded files to protect resources in the managed file store (and ultimately to shield org users that might access these resources). This distinction matters because one part describes scanning OS and application files already deployed and operational on the MOVEit Transfer server machine. The other describes the unique capability to scan files (usually originating from another network) before they become part of the managed file store.
Protects local server machine running MOVEit Transfer software. It scans the local MOVEit Transfer server host system. It must not interfere with MOVEit Transfer operations.
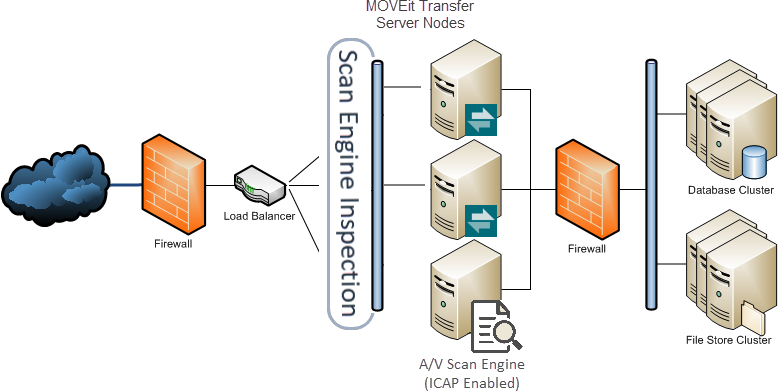
Scans files as clients (mobile, Web, and so on) upload to the MOVEit Transfer managed file store. This solution uses an A/V engine over an ICAP connection.
![]() Content scanning at upload is often paired with (or complemented by) Data Loss Prevention at download. For more information, see the section titled Content Scanning.
Content scanning at upload is often paired with (or complemented by) Data Loss Prevention at download. For more information, see the section titled Content Scanning.
Use these guidelines if you run a local anti-virus application to protect the MOVEit Transfer server machine.
![]() For more information on how to avoid the scenario where the local A/V or malware scanner interferes or blocks MOVEit Transfer server operations, see the MOVEit Transfer and MOVEit Automation A/V best practices community article in our knowledge base.
For more information on how to avoid the scenario where the local A/V or malware scanner interferes or blocks MOVEit Transfer server operations, see the MOVEit Transfer and MOVEit Automation A/V best practices community article in our knowledge base.
MOVEit Transfer server is often positioned on a network segment exposed to the Internet. The use of a maintained and up-to-date anti-virus product on the server (such as Windows Defender) has benefits. However, when setting up an anti-virus product on a server running MOVEit Transfer, ensure that you add no-scan exceptions for MOVEit Transfer server, subprocesses, and file store.
The MOVEit Transfer system uses a secure network channel to communicate with clients. It also employs 'at-rest' encryption to its managed file store. To some local or desktop A/V solutions, MOVEit Transfer server operations might be miscategorized as a possible threat (resulting in temporary block or quarantine of MOVEit Transfer processes, files, or other resources).
MOVEit Transfer Outside Corporate Network facing the Internet on a "DMZ" (segment between external and internal firewalls)
If you enable a local A/V scanner on the MOVEit Transfer server machine (for example, Windows Defender), provide anti-virus scan exceptions for the following core resources and components:
To avoid possible false positive virus matches and to prevent an anti-virus program from quarantining or even deleting files from the MOVEit Transfer file store, the anti-virus solution must be configured to ignore the MOVEit Transfer file store location. Encrypted files are stored in the Files subdirectory of the MOVEit Transfer non-web directory (typically D:\MOVEitTransfer). Therefore, for a typical installation, the anti-virus program should be configured to ignore D:\MOVEitDMZ\Files.
Note: For more information on resource and file location, see the topic titled System Internals - Technical Reference.
Configure the anti-virus program to ignore the MOVEit Transfer database files since they can contain binary data, which might be misinterpreted as a threat (several fields in the database are stored encrypted). If your database is MySQL, data files are typically stored in the Data subdirectory of the MySQL installation directory (typically D:\MySQL). Therefore, for a typical installation, the anti-virus program should be configured to ignore D:\MySQL\Data. If your database is Microsoft SQL Server, the files are typically stored in a directory like: C:\Program Files\Microsoft SQL Server\MSSQL.1\MSSQL\Data.
The main MOVEit Transfer processes you should exempt from scan (or blocked list) are:
In this scenario, an ICAP-enabled anti-virus engine ensures files that scan positive for virus signatures are not allowed into or out of the internal network. For example, files are scanned during the upload and are not added into the MOVEit Transfer filesystem until the content scanner returns an indication that the file shows no patterns that match the current virus definitions (or threat model).
Note: For more information, see the topic titled Content Scanning.
MOVEit Transfer encrypts files before writing them to disk. As a result, the unencrypted file data is never available on disk and never available to disk-checking anti-virus programs. For maximum security, most files are not stored in memory in their entirety but are instead read and written in smaller chunks. This makes most files unavailable to memory-checking anti-virus programs as well.
In addition to the fact that an anti-virus program should never be able to identify an actual virus in a file that is encrypted by MOVEit Transfer, the nature of file encryption makes false positives a possibility as well. It is possible that the process of encrypting a file can generate inside that file a sequence of bytes that anti-virus programs may read as a virus signature. Therefore, it is recommended that anti-virus programs be configured to ignore the MOVEit Transfer encrypted file store entirely.
Most MOVEit Transfer servers are placed on an isolated network segment. Such servers tend to be independent of the rest of your corporate network and are usually not added as members of a Domain or Active Directory tree. For the same reasons, centrally-managed anti-virus programs tend to have a harder time accessing and maintaining installed instances on MOVEit Transfer servers. Therefore, local anti-virus programs are usually installed in independent or stand-alone mode on MOVEit Transfer servers. For this reason, they require independent configuration, virus updating, and event checking.