This topic describes firewall configurations needed to allow your internal and external traffic to communicate with MOVEit Transfer. MOVEit Transfer was designed to be available and secure on DMZ segments exposed to the Internet.
MOVEit Transfer features protocol servers (such as HTTPS, FTPS, and SFTP) that clients using the same protocols connect to. It can also require availability of services such as SMTP (for email notifications) and LDAP (if external auth is used) along with its MFT database and filestore (which are typically running on a distinct host).
MOVEit Transfer communicates only over ports designated by its configuration. These ports are controlled by the MOVEit Transfer Config Utility. Most firewalls enable outgoing traffic from hosts behind the firewall while restricting traffic from the "outside world" (this includes the hop between your corporate and WAN firewalls or the what is commonly referred to as the DMZ, your ISP's metropolitan area network beyond that, and beyond that the entire Internet of reachable devices).
![]() If you are using MOVEit Transfer for the first time or you are unsure which ports MOVEit Transfer currently uses or expects traffic on, you can check the MOVEit Transfer Config Utility. You can also validate these settings using port scanner tools like nmap.
If you are using MOVEit Transfer for the first time or you are unsure which ports MOVEit Transfer currently uses or expects traffic on, you can check the MOVEit Transfer Config Utility. You can also validate these settings using port scanner tools like nmap.
HTTP over TLS ("HTTPS"), FTP over TLS (also referred to as "FTPS") and/or Secure File Transfer Protocol (SFTP) are used to communicate with MOVEit Transfer. MOVEit Transfer also needs to access your Simple Mail Transfer Protocol (SMTP) services (email server used for notifications).
FTPS uses different ports (effectively two channels) one for control and the other for data. FTPS uses logical ports for control messages (a port used for sending FTP session commands) and other logical ports for data (a different channel for sending entire or chunked portions of the folder or files). This distinction is important because for protocols like FTPS, it can mean applying incoming firewall rules to accommodate pass through for each the control commands and the chunked data stream. Direction is also important, because firewalls are meant to enable outward traffic and restrict incoming connections.
SFTP uses one port for both control messages and data.
Nonsecure HTTP services are optional and not recommended. If nonsecure services are enabled, MOVEit redirects users to the secure services. (IIS does not redirect.)
It is important to understand that firewall rules are directional. In other words, they control access to services relative to the sender/receiver's position to the corporate network. Outgoing traffic from a LAN is normally unrestricted (this is obvious when you casually connect your web browser to an e-commerce server, for example). However, traffic aimed at your corporate LAN from the Internet is restricted and wrapped in rules and policies to protect the assets on your network. Note then the distinction of traffic and connections initiated internally (from within the corporate LAN) or else from traffic initiated from somewhere on the Internet (from a business-partner's network, a mobile network and so on).
![]() The rules that follow assume you are using MOVEit Transfer without MOVEit Gateway. MOVEit Gateway serves as a trusted proxy to MOVEit Transfer. If you are using MOVEit Gateway, check the MOVEit Gateway Admin Guide for specific deployment details.
The rules that follow assume you are using MOVEit Transfer without MOVEit Gateway. MOVEit Gateway serves as a trusted proxy to MOVEit Transfer. If you are using MOVEit Gateway, check the MOVEit Gateway Admin Guide for specific deployment details.
The diagram that follows uses the following conventions:
Note: The following infographic shows LDAP and SMTP on a corporate LAN. If you are using cloud-available services, such as O365, LDAP and SMTP would then be positioned on the Internet side.
MOVEit Transfer Server Positioned on the DMZ Between a Corporate and WAN Gateway Firewall
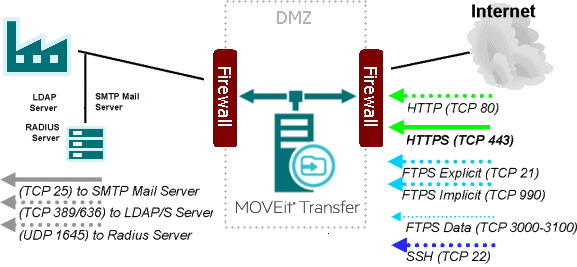
To prevent outside traffic from opening unauthorized connections to MOVEit Transfer, use the following rule:
REQUIRED: Deny (ALL CONNECTIONS) to MOVEit Transfer
To prevent MOVEit Transfer from opening unauthorized connections to outside computers, use the following rule:
REQUIRED: Deny MOVEit Transfer to (ALL CONNECTIONS)
Depending on the services you choose to run on MOVEit Transfer, you must open one or more ports. The criteria and specifics are covered below.
MOVEit Transfer normally listens for NONSECURE web connections on TCP port 80 and SECURE web connections on TCP port 443. Remote users MUST be able to connect to the secure port (443) from remote addresses. Optionally, you can also leave port 80 open if you want MOVEit Transfer to auto-redirect users connecting on the nonsecure port to the secure port instead.
Note: MOVEit Mobile Client uses HTTPS (Port 443).
MOVEit Transfer uses a one-port SSH tunnel to support FTP over SSH clients. The use of a single SSH tunnel has an advantage over the multiple encrypted data streams used by FTP over SSL: fewer ports need to be opened on a firewall. (FTP over SSH is a single port secure transfer protocol.) The one port normally used by SSH is TCP port 22.
REQUIRED: Allow TCP (Remote) (Any Port) to MOVEitDMZ Port-22
If MOVEit Transfer FTP needs to support clients over the Internet, PSC strongly recommends you REQUIRE PASSIVE MODE FTP TRANSFERS and LOCK PASSIVE DATA PORTS TO A SMALL RANGE on MOVEit Transfer FTP.
Warning: Only specifying FTP on your firewall will rarely be enough to allow secure FTP through (unless both client and server use the CCC option). Firewalls that understand FTP look for the phrase "PORT" in data channels and open temporary holes in the firewall for communications over the designated ports between the two machines on either side of the data channel. However, secure data channels are encrypted, meaning the firewall cannot open any temporary ports.
Explicit FTPS control connections take place on TCP port 21.
Implicit FTPS control connections take place on TCP port 990.
If you use FTPS on your MOVEit Transfer system, it is HIGHLY RECOMMENDED that you configure it to use both explicit and implicit modes (for greatest client compatibility), passive mode (to allow the server to chose and notify the client of a port to use), and to use a restricted range of ports.
Passive FTP simplifies configuration from the client side. It allows the MOVEit Transfer Server and any clients to use typical control ports for FTP and enables the client initiate outgoing data connections with the server.
MOVEit Transfer normally listens for SECURE FTP control connections on TCP port 21 (and 990 when using implicit mode). In restricted passive mode, MOVEit Transfer listens for SECURE FTP data connections on a configurable range of contiguous TCP high ports (for example, 3000–3100,) that it specifies for the data channel of a particular client session. Because MOVEit Transfer uses the control channel to convey the logical data port it expects the client to use, nothing extra needs to be configured on client's side other than to specify passive mode transfers.
If you choose this option, the data port range used for MOVEit Transfer must be accessible. These incoming ports must be left open for proper communication.
MOVEit Transfer expects FTPS clients using client certificates to target different control ports.
If you use MOVEit Transfer FTPS (FTP/TLS) with client certificates, MOVEit Transfer expects these clients to connect to the Transfer Server using a distinct FTPS control port. You will need to open an incoming firewall rule for that port. However, in this client certificate scenario, MOVEit Transfer provides the same data port(s) as it would for regular FTPS sessions. (No additional firewall rules for data ports are needed.)
For example, consider the case where Explicit control and Implicit control ports are configured for a MOVEit Transfer FTP server. MOVEit uses ports 21 and 990 to handle control messages for regular FTPS connections. For sessions using client certificate authentication, however, by default MOVEit Transfer expects to see FTPS control messages on 10021 (Explicit channel) and 10990 (Implicit channel) to handle client-cert-authenticated connections.
![]() If you want to require some FTPS connections to authenticate with client certificates while others do not (common during migrations), you must set these additional control ports to allow FTPS client certificate authentication.
If you want to require some FTPS connections to authenticate with client certificates while others do not (common during migrations), you must set these additional control ports to allow FTPS client certificate authentication.
MOVEit Transfer supports the CCC FTP command. The CCC command allows FTP-aware firewalls to understand the PORT commands otherwise hidden by FTP over SSL. Specifically, the CCC command allows the PORT commands to be understood by firewalls by dropping the control channel out of encrypted mode and into cleartext mode.
Using the CCC command creates the following security risks:
The security risk of the alternate solution - a limited number of open ports - is that another service could be installed on that server and could start listening on those ports.
Active FTP is NOT recommended for Internet connections because remote firewalls will likely not permit active FTP data connections in, especially if they are encrypted.
Setting Passive FTP up in unrestricted mode is not recommended because proper operation of this mode requires a wide range of high ports (thousands) to be open on the firewall.
MOVEit Transfer normally listens for SECURE FTP control connections on TCP port 21 (and 990 when using implicit mode). As a passive FTP server, MOVEit Transfer will then listen for a SECURE FTP data connection on the TCP high port (>1023) it negotiated with the client. These ports must be left open for proper communication.
The MOVEit Transfer server requires the use of an SMTP-compliant mail server to send email notifications. If your MOVEit Transfer server notifications must pass through a firewall to reach a mail server, you must allow MOVEit Transfer to access it over the TCP port SMTP listens on for incoming requests. Typically this means port 25. If you want the ability to queue messages if your mail server is unreliable, need special authentication parameters to relay mail, or generally plan on sending many notifications at one time, consider setting up a local mail relay.
Note: The MOVEit Transfer server does not need to access an internal email server if you can point it to your upstream (ISP) mail relay instead.
REQUIRED: Allow TCP MOVEitDMZ (High Ports) to (YOUR MAIL SERVER) Port-25
If you intend to use RADIUS remote authentication, MOVEit Transfer must be able to communicate using UDP to the remote RADIUS server. The UDP port normally used to support RADIUS is 1645, but this port is configurable.
OPTIONAL: Allow UDP MOVEitDMZ (High Ports) to (YOUR RADIUS SERVER) Port-1645
If you intend to use LDAP remote authentication, MOVEit Transfer must be able to communicate using TCP to the remote LDAP server. The TCP port normally used to support LDAP is 389 and the port normally used to support LDAP over SSL is 636, but these ports are configurable. (The use of LDAP over SSL is strongly recommended; most modern LDAP servers support this. For example, see Active Directory - SSL in Feature Focus - External Authentication for instructions to enable SSL access on Active Directory LDAP servers.)
If MOVEit Transfer connects remote Microsoft SQL Server database, such as in a web farm pattern, the MOVEit Transfer node must be able to communicate over the SQL Server ports. Port 1433 is the default SQL Server port if you have configured a different port for your SQL Server instance, use that port instead of 1433. You must open port 1434 only if you plan on running SQL Server Studio or another SQL Server utility on the MOVEit Transfer application nodes themselves.
If MOVEit Transfer Web Farms is in use, each node and the UNC filestore (NAS, for example) must allow Microsoft networking protocols between them. This is normally accomplished by opening TCP port 445 between the various machines. However, DO NOT leave this port open to or from the Internet.
Some sites, such as those regulated by the FDA, might need to ensure that the clock on MOVEit Transfer is kept in sync with a known, external source. The hostnames of external time sources such as time.nist.gov can be found on various lists of public time servers.
Time services (RFC 958) normally use UDP port 123. When setting up firewall rules to support external time service, you must allow UDP packets to travel from any high port on the MOVEit Transfer to remote UDP port 123, ideally on one or a small collection of remote servers. Return traffic using the same UDP port must also be able to return to your MOVEit Transfer server.
Notes:
If you elect to send MOVEit Transfer Audit Events to a SysLog server, you will likely need to allow UDP SysLog packets to travel from your MOVEit Transfer to the SysLog server on UDP port 514.
If you elect to send MOVEit Transfer Audit Events to an SNMP management console, you will likely need to allow UDP SNMP packets to travel from your MOVEit Transfer to the SNMP management console on UDP port 161.
This procedure has largely been replaced by the ability of the MOVEit Transfer API to run ad-hoc custom reports against most MOVEit Transfer configuration elements and audit entries remotely over a secure connection.
If you elect to set up an ODBC stunnel connection (as described in Advanced Topics - Database - Remote Access), you will likely need to allow connections from MOVEit Automation to MOVEit Transfer on TCP port 33062. This port is configurable and may be changed in both the stunnel_mysqlserver.conf and stunnel_mysqlclient.conf configuration files involved.
MOVEit Freely and MOVEit Buddy are secure FTP clients. See the Remote Secure FTP Over SSL Clients section above for required port information.
MOVEit Automation typically communicates with MOVEit Transfer via HTTPS. See the Remote Web Browser (HTTP/S) section above for required port information.
The MOVEit Wizard, MOVEit Xfer, MOVEit Transfer API and MOVEit EZ clients all communicate with MOVEit Transfer using HTTPS. See the Remote Web Browser (HTTP/S) section above for required port information.
AS2 clients normally use HTTPS. In rare cases they can use HTTP instead. See the Remote Web Browser (HTTP/S) section above for required port information.
AS3 clients are secure FTP clients. See the Remote Secure FTP Over SSL Clients section above for required port information.