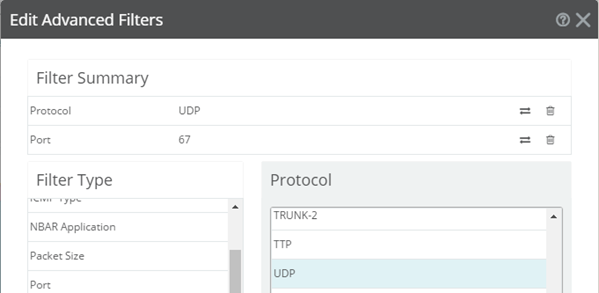
Advanced filters enable you to isolate traffic by protocol, domain, application, and so on. For example, the following visual demonstrates how to isolate BOOTP request traffic (in other words, client devices requesting an IP address from a BOOTP Server on their network segment).
Tip: Click the arrows button (![]() ) to exclude/include the specified filter pattern.
) to exclude/include the specified filter pattern.
Tip: For filtering on an IP address, you can use CIDR notation to identify a subnet of hosts from which the reports display data. For example, when you select a Sender filter type, you can specify a subnet using 192.168.11.0/24 to display information from all of the hosts in the subnet.
Filter Type Name |
Description |
Application |
In NTA, the simplest way to distinguish an application is by checking for TCP/UDP ports usage against well-known ports defined by the IETF or as defined by you in the NTA Applications Library. You can select one or more to filter on to reveal traffic that used the specified application port. The label you use here must match the application name as configured in the NTA Applications Library. Tip: For more precise application recognition/detection, you can also use NBAR (if enabled at the source device). |
Conversation |
Conversations are the combination of a sender IP address, receiver IP address, and the suspected application in use between them. |
Conversation between Locations |
Conversations between locations are the aggregation of all the traffic sent by a location and received by another location. A location can be a country, a region in a country, or a city in a region and country. |
Endpoint |
An endpoint represents one or more IP addresses sending or receiving traffic. It can be as a specific IP address, a subnet in CIDR notation, or one of the special keys that represent predefined groups. The predefined groups are:
|
Endpoint Location |
All IP addresses located in a City, Region, and Country that are sending and receiving. |
ICMP Type |
ICMP Type. Examples of ICMP type are 'Echo Request' or 'Echo Reply' and more as defined by the IETF. |
NBAR Application |
NBAR Applications are the application that the source device detected using NBAR packet inspection. NBAR information is typically included in flow summaries (when you use Flexible NetFlow, for example). Otherwise, you can also use SNMP to poll the source device for NBAR information. |
Packet Size |
Filter by average packet size. |
Port |
Port number selected as the service port in a flow (80 for HTTP, 21 for FTP, and more). |
Receiver |
One or more IP addresses receiving traffic. It can be a specific IP address, a subnet in CIDR notation, or one of the special keys that denote predefined groups. These special groups are:
|
Receiver ASN |
All the IP addresses in the same network with the same ASN number receiving traffic. ASN stands for Autonomous system number and is a unique number used by the Border Gateway Protocol (BGP). |
Receiver Domain |
All the IP addresses in the same domain receiving traffic. To get the domain, WhatsUp Gold extracts the two highest parts from the fully qualified name except for certain countries —where three parts are used to identify a domain. For example, in the United Kingdom or Japan, the second part identifies the type and not the company, so the BBC domain is BBC.co.uk. |
Receiver Group |
All the IP addresses in the same NTA Group receiving traffic. Customers can select multiple groups in the combo box. |
Receiver Location |
All the IP addresses in the same geographical location (country, region, or city) receiving traffic. Customers can select multiple locations in the combo box. |
Receiver TLD |
All the IP addresses with the same Top Level Domain (TLD) receiving traffic. The TLD is extracted from the fully qualified name and in most cases identify the country of the registered domain —with the exception of the US that identifies the type COM, EDU, ORG, and more. |
Sender |
One or more IP addresses sending traffic. Sender can be a specific IP address, a subnet in CIDR notation, or one of the special keys that denote predefined groups. These special groups are:
|
Sender ASN |
All the IP addresses in the same network with the same ASN number sending traffic. ASN stands for Autonomous system number and is a unique number used by the Border Gateway Protocol (BGP). |
Sender Domain |
All the IP addresses in the same domain sending traffic. To get the domain, WhatsUp Gold gets the two highest parts from the fully qualified name except for certain countries where three parts are used to identify a domain. For example, in the United Kingdom, or Japan, the second part identifies the type, and not the company, so the BBC domain is BBC.co.uk. |
Sender Group |
All the IP addresses in the same NTA Group sending traffic. |
Sender Location |
Show traffic sent by devices whose IP addresses are registered to a country, state, subdivision, or city |
Sender TLD |
Show traffic sent by domains that have the specified top-level domain (such as .com, .net, .us, or .uk). |
TCP Flags |
TCP traffic will typically exhibit one or more of the specific TCP Flags (SYN, ACK, FIN, RST, ECE, PSH, URG, CWR). Flows contain the accumulation of the TCP flags used during the life of the flows. (For example, flows with only the SYN flag on are indicators of connection attempts that were never acknowledged with a SYN-ACK message). |
Type of Service |
Filter by Type of Service (ToS) identifier. |
Tip: You can enter a port number instead of an application name to show all traffic transmitting over a certain port.