Managing SSL certificates, SSH keys, and PGP keys is done using the Cert/Key manager in MOVEit Central Admin. This dialog is available by choosing the Settings menu, selecting Certs/Keys, and selecting the key/cert type you wish to manage. From here, keys and certs can be listed, details about individual entries shown, new keys created or imported, and existing keys removed. There are also more options available for specific key/cert types.

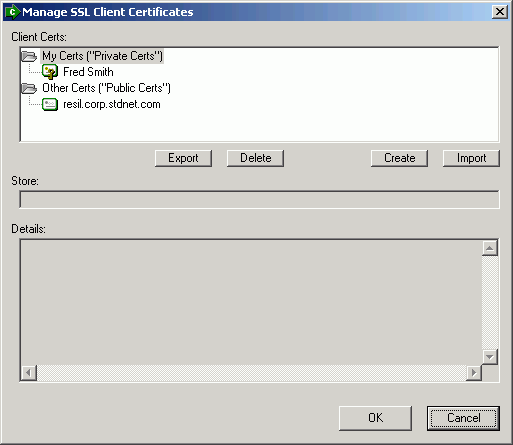
SSL client certificates are listed here under the particular store the certificate is installed under. Personal client certificates (those including private keys) are generally shown in My Certs store (corresponding to the "Personal" or "My" store in Windows). Client certificates for other people (those not including private keys) are generally shown in the Other Certs store (corresponding to the "Other People" or "AddressBook" store in Windows).
Choosing a certificate in the list will display information about that certificate in the Details field. Certificate fields such as issuer, expiration date, and thumbprint are displayed here. A selected certificate can also be deleted by clicking the Delete button.
Existing certificates can be added to the system by choosing the Import button. The user will be prompted to select a certificate file from their local system to be imported. Files ending with a ".pfx" or ".p12" extension are assumed to contain private keys, and the user will be prompted for the password securing those keys. If no such password is set, simply leave the password field blank and click OK. Files ending with other extensions are assumed to contain only public certificates, so the user will not be prompted for a password.
New certificates can be generated and added to the system by choosing the Create button. The user will be prompted for various fields; the only required field is Name, also known as Common Name or CN. The certificates generated in this way are "self-signed" and unlike certificates issued by well-known certificating authorities, will not automatically be trusted by other sites.
NOTE: Use of self-signed certificates is not recommended for securing web servers like IIS, as they will cause trust errors to occur with end users who visit a site configured with one. Self-signed certificates are suitable for testing, for securing communications between MOVEit Central and MOVEit Central Admin, and in some cases for production use in applications like AS2.
NOTE: If you have access to MOVEit DMZ as an administrator, you can also generate self-signed SSL certificates through the MOVEit DMZ web interface.
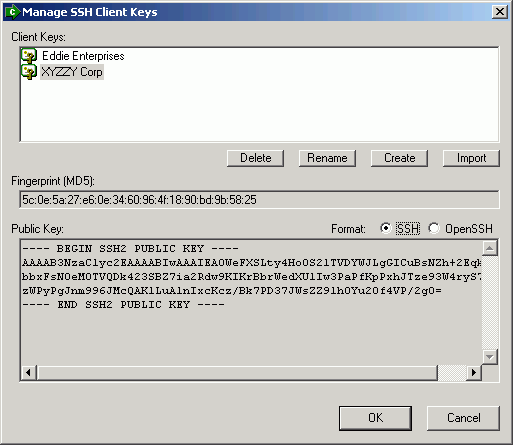
SSH client keys available in MOVEit Central are listed here. choosing a key in the list will display the key fingerprint in the Fingerprint (MD5) field, and the text content of the key in the Public Key field. Use the Format radio options to select the displayed key content format in the Public Key field. SSH and OpenSSH formats are supported.
A selected key can be renamed by clicking the Rename button. The new name will be prompted for. A selected key can also be deleted by clicking the Delete button.
New keys can be added by choosing the Create or Import buttons. First, the user will be prompted to enter a name for the new key. Next, if the user clicked the Create button, MOVEit Central will generate a new key and add it to its internal keyring. If the Import button was clicked, the user will be prompted for a key file, and then a passphrase. The data from the provided key file will then be imported into MOVEit Central's keyring.
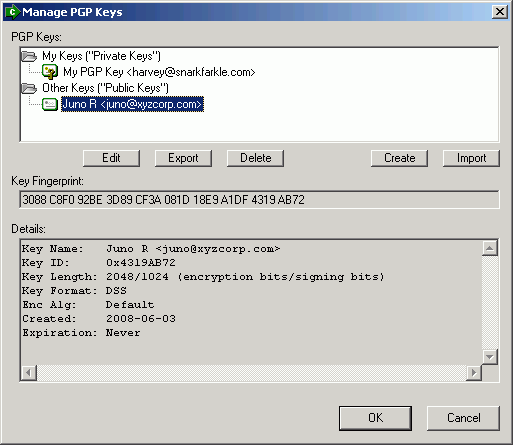
PGP keys are listed here in two sections, related to the key types. Personal PGP keys (those containing public and private keys) are listed in the My Keys section, while other PGP keys (those containing only public keys) are listed in the Other Keys section. choosing a key in the list will display the key fingerprint in the Fingerprint field, as well as information about that key in the Details field. Key fields such as name, size, format, and expiration date are displayed here.
For more information about actions available for PGP keys, see the Managing PGP Keys page in this section.