Users of SSH clients know to trust specific machines because their keys will match publicly available SSH fingerprints. As part of the instructions you give your clients, you SHOULD be distributing the fingerprint of your MOVEit DMZ SSH server so your clients can confirm the identity of your server. (Without this protection, anyone could spoof this or any other SSH server!)
The following OpenSSH session shows this mechanism in action. Specifically, OpenSSH asks the end user if they want to trust the remote server after displaying the MD5 hash of the remote server's SSH server key.
d:\>sftp sshftpuser@moveit.myorg.com Connecting to moveit.myorg.com... The authenticity of host 'moveit.myorg.com (33.44.55.66)' can't be established. DSA key fingerprint is 0f:70:32:8f:03:fa:b4:fc:e3:36:bb:ed:37:16:e9:32. Are you sure you want to continue connecting (yes/no)? yes sshftpuser@moveit.myorg.com's password:
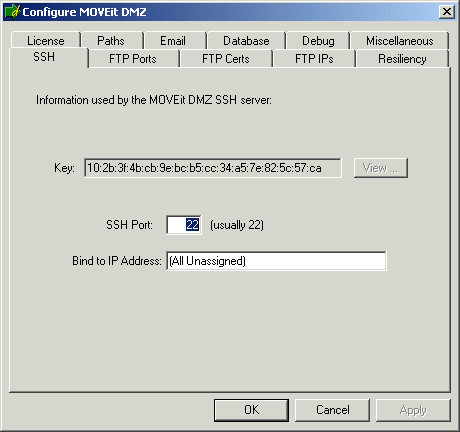
MOVEit DMZ's SSH key is automatically generated the first time the server is started and an associated fingerprint is created at the same time. To view your MOVEit DMZ SSH key fingerprint log into a Windows console on your MOVEit DMZ server. Open "Start -> All Programs -> MOVEit DMZ -> MOVEit DMZ Config" and navigate to the 'SSH' tab to view your MOVEit DMZ's SSH key MD5 hash.

The MOVEit DMZ SSH server key is stored encrypted in the registry under the "SSHServer\PrivKey" registry entry. Any registry backup, including the registry backup performed by the MOVEit DMZ Backup Utility, will back up this key.
To export MOVEit DMZ's public SSH server key in either OpenSSH or SSH2 format, see the related instructions in the "SSH - Configuration" documentation.