Please also see FTP Certs Tab in FTP - Configuration and the Multiple SSL Certificates below if you plan on hosting multiple organizations with different SSL certificates on your MOVEit DMZ server.
The first page users will see depends on the link they followed to the signon page. For most users following links off an organization's main web site, the first page they will see will be their Home page. For users following links from notification emails, the first page will be a page with details about a specific file.
The Sign On page is presented in two different flavors:
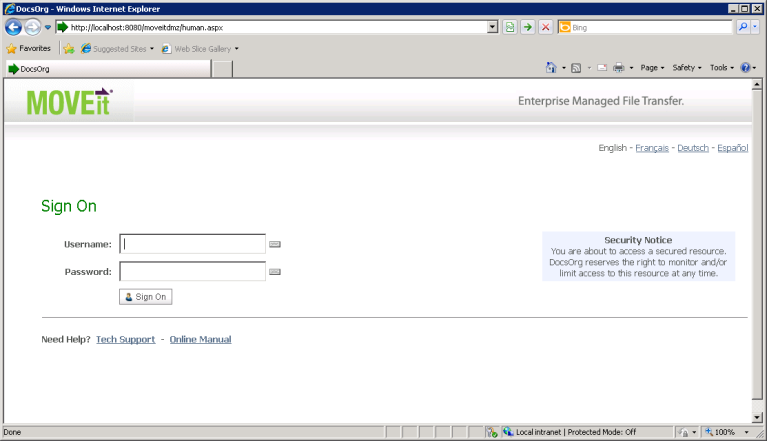
Using the default MOVEit Gray scheme.
An unbranded Sign On page will display the MOVEit DMZ logo and contact information for the site provider. (This information has been configured by a SysAdmin.)
An unbranded Login page will be displayed by default unless particular Organizations take steps to brand this page. The URL to invoke this page is typically of this form: http://moveit.nowhere.com
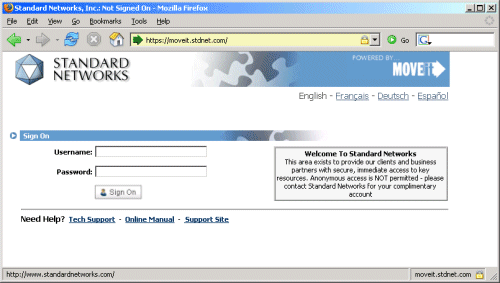
Using a customized scheme.
A branded Login page will display a particular Organization's logo, colors and contact information. (This information has been configured by an Administrator for that particular Organization through that Administrator's Settings page.)
A branded Login page will display in either of two cases:
Particularly with older versions of MOVEit DMZ, you may have noticed that simply copying a URL for a specific user, folder, file or other MOVEit DMZ profile may cause MOVEit DMZ to sometimes display (correctly) that your session has timed out when you next try to access this URL. The display of this message, however, is often misleading, especially if you intend to use this URL in a permanent link tag on a public web site. (For example, Ipswitch provides a direct link to the support page from which customers and evaluators may download its software.)
To always suppress this session expired message, simply append the following code to any URL you wish to may publicly available:
&quiet=true
Normal MOVEit DMZ pages include a header with banner logo, a user information bar, and a left-hand navigation section, all of which allow the user to navigate their way to different pages within the application. Some companies may wish to hide these sections, though, especially when DMZ is used in a single-signon system as part of a larger web application. To do so, the following code may be appended to the URL the user clicks to visit MOVEit DMZ:
&contentonly=1
This will cause the header, userbar, and left-hand navigation to be hidden for the rest of the session, or until the code above is repeated with a value of 0. Since the value is stored in the session, only the first MOVEit DMZ URL invoked by the portal application needs to have this code.
Since this feature is designed to allow MOVEit DMZ to be used within an existing web application via frames or iframes, when the contentonly flag is enabled, MOVEit DMZ will disable its normal cross-frame scripting protection code and allow the interface to be loaded by external framesets.
Normal MOVEit DMZ pages include a Sign Out link in the upper right corner, allowing the user to discontinue their session. When used in a single-signon system as part of a larger web application, this is generally not a desirable feature. Instead, it is usually desirable to provide the user with a link back to the main web application. To have MOVEit DMZ replace the Sign Out link with a custom Return link, the following code may be appended to the URL the user clicks on to visit MOVEit DMZ:
&returnto=<your URL>
Replace <your URL> with the full URL of the web page you wish the user to return to. The URL must begin with either http:// or https://. Since the value is stored in the session, only the first MOVEit DMZ URL invoked by the portal application needs to have this code. However, DMZ will always use the latest value provided to it for this option.
In a situation where someone wants to set up a single signon to integrate MOVEit DMZ into an existing portal environment, you can build up a link (or submit a form) which silently prefills a username and password. To make this occur, add the following snippet to any regular MOVEit DMZ URL.
&username=myusername&password=mypassword&transaction=signon
Please be aware that by using a username and password in a link, you incur the following risks:
The issue with username and password being saved in local client history is usually mitigated if a form-based (POST) submission is used instead.
Installations which wish to expose subfolder URLs without OrgIDs. (e.g., a site may want Woodstock Bank's users to access MOVEit as https://www.myorg.com/woodstockbank and let Bull Valley Credit Union's users access MOVEit as https://www.myorg.com/bullvalley). This arrangement is especially common at data centers where ownership wishes to minimize annual certificate costs by hosting many related sites on a single server.
To effect this configuration, perform the following steps for each subfolder you wish to configure.
<% ' This redirect script sends users who type in "friendly" URLs
' to MOVEit's front door with the appropriate parameters.
'* * * * * * * * * * * * * * * * * * * * * * * * *
'* Set your Organization's ID here!!!
Dim OrgID as String = "1234"
'* * * * * * * * * * * * * * * * * * * * * * * * *
'* Set the official URL of your MOVEit DMZ here!!!
'* (Make sure this URL has a VALID certificate.)
Dim URL as String = "https://moveit.stdnet.com"
'* * * * * * * * * * * * * * * * * * * * * * *
'* Do NOT modify the code below this line!!!
Response.Redirect(URL & "?OrgID=" & OrgID)
%>
By providing a special URL to end users, end users can be forced them to initiate a (non-Wizard) download immediately after signing on (if not already authenticated). This procedure is typically performed by a MOVEit DMZ API application which creates its own notifications or web pages, but the same technique can be used by any application which can create a link for a user to click.
Use the following syntax to initiate a direct download. Items to be filled in are in square brackets. Be sure your requests actually only use one line.
https://[MOVEitDMZ_Hostname]/human.aspx?
Username=[EndUser_Username]&arg01=[MOVEitDMZ_FileID]&
arg05=0/[DownloadAs_Filename]&arg12=downloaddirect&
transaction=signon&quiet=true
The following example prepares to sign on as Penguin to download a file with ID#910286 as dwn.gif.
https://dotnet.stdnet.com/human.aspx?
Username=penguin&arg01=9102186&
arg05=0/dwn.gif&arg12=downloaddirect&
transaction=signon&quiet=true
This crafted URL may be used with other crafted URLs such as Simple Single Signon Support or MOVEit DMZ API's session redirect to ensure the user is signed on before attempting a transfer. (Otherwise, the user will be prompted for a username and password.)
Note: Sometimes different browsers will handle direct file downloads from MOVEit DMZ in different ways; sometimes files will be automatically opened by the browser using the default application for that filetype, while other times the user will be prompted to save the file before actually opening it. If the behavior the end users are experiencing is not the desired behavior, try adding the argument noattch=0 to the direct download URL. This will cause MOVEit DMZ to add a Content-Disposition: attachment header to the direct download response, which will cause some browsers to treat the downloaded file differently than normal.
If you wish to support having different SSL certificates for different MOVEit DMZ organizations, you must have a unique IP address / port combination, and SSL certificate, for each organization. (IIS 7.0 on Windows 2008 does not require separate sites.) (See Feature Focus - Multihoming for more information.) If you are willing to share a named certificate across organizations, none of these extra steps are required.
For example, if SampleHoster wants to host secure.acme.com and ftps.whammo.com on the same MOVEit DMZ machine, each with a unique SSL certificate, then SampleHoster is multihoming. However, if SampleHoster wants to host vault.samplehoster.com and allow access to vault.samplehost.com/acme and vault.samplehost.com/whammo (one, shared SSL certificate), SampleHoster needs only:
Both of these configurations have been deployed by data centers and MOVEit DMZ supports both equally well in production. The main reason cited for going with individual SSL certificates for each organization is that it completes the branding experience. The main reasons cited for going with single shared SSL certificate is that it reduces management hassle and SSL certificate costs.