The MOVEit DMZ Configuration program is used to configure the MOVEit DMZ SSH server. (Users, groups, folder settings and the like are generally maintained through the Web Interface or MOVEit DMZ API.) Run the configuration program by choosing the Start menu shortcut MOVEit DMZ Config. This program uses a tabbed dialog to group the settings by function.
MOVEit DMZ SSH will immediately apply configuration changes the next time a new connection is received.
Exception: If a change is made to the SSH port, the MOVEit DMZ SSH service must be restarted for this change to take effect.
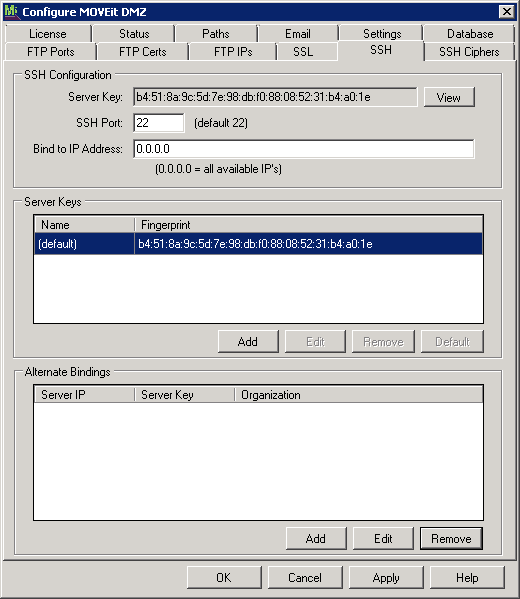
SSH Configuration
To export MOVEit DMZ's SSH public key, click the View button on the SSH tab of the MOVEit DMZ Config utility. The dialog will show you the key in two different formats. Select all the text in the window displaying the format you wish to export, press CTRL+C to copy the text, then save it into a text file of your choice.
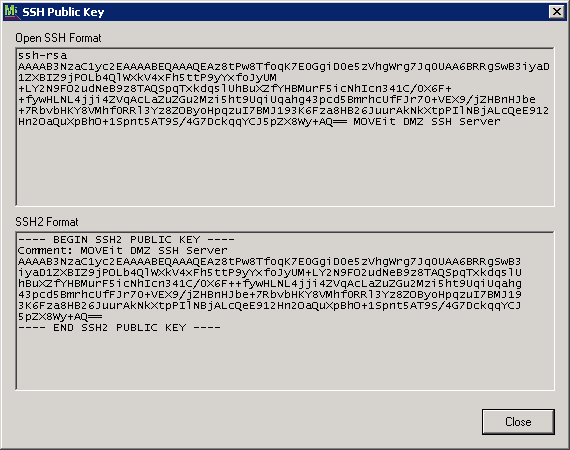
HINT: MOVEit DMZ's SSH server key never changes, so it's probably worth the extra time to export both formats of the same SSH server key while you're in the dialog. If you save these off (perhaps on an internal server) you may never need to come back to the SSH tab again.
Server Keys
The Server Keys window shows the MD5 hash of the internally generated RSA 2048-bit server key. You may not edit or remove this default key.
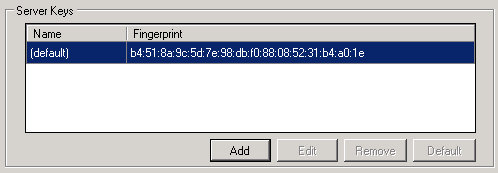
If your MOVEit DMZ has multiple organizations, you may want to add a different server key for each organization. Doing so will make it easier to change only one organization’s server key without affecting other organizations.
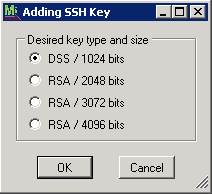
The DSS key type provides digital signatures but not key exchange or encryption. With DSS, signature generation is faster than signature verification.
The RSA key types provide digital signatures, key exchange, and encryption. With RSS, signature verification is faster than signature generation.
After you select a key type and size, the Add SSH Server Key window displays:
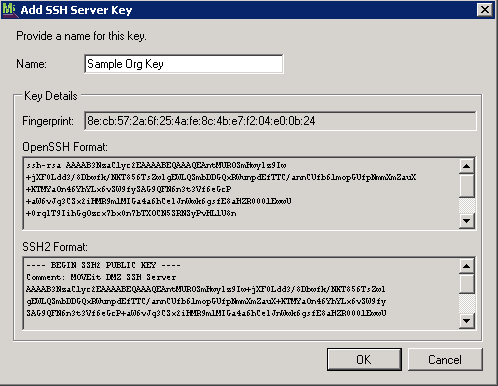
This window shows the key details, including Fingerprint, OpenSSH Format and SSH2 Format.
The new key adds to the Server Keys window.
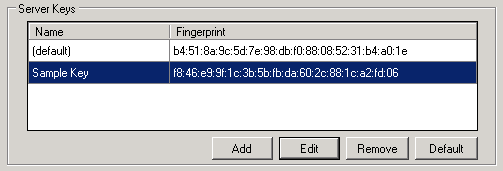
To edit a key's name, select the key and click Edit.
To remove a key, select the key and click Remove.
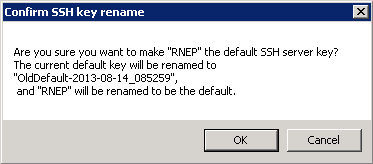
To make a key the default SSH server key, select the key and click Default. The current default key will be renamed to "OldDefault-year-month-day_xxxxxx" and the name of the key you have selected will be renamed "default."
Alternate Bindings
If your MOVEit DMZ has multiple organizations and it allows duplicate usernames across organizations, you can direct users to the IP address of their specific organization during signon by adding an alternate binding. You can also assign a unique server key to an organization so that any changes you make to that server key will affect only that organization.
Alternate Bindings lets you associate a Server IP, Server Key, and Organization.
The Add SSH Alternative Binding dialog displays.
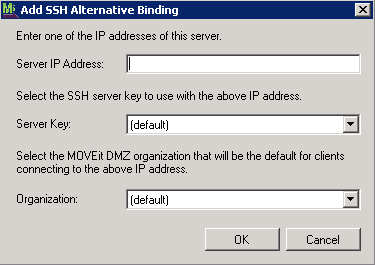
The new binding adds to the Alternate Bindings window.
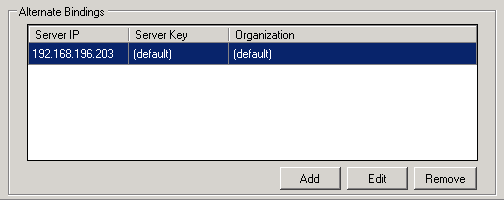
To edit the Server IP, Server Key, and Organization of a binding, select the binding and click Edit.
To remove a binding, select the binding and click Remove.
The MOVEit DMZ SSH server's diagnostic log settings can be changed on the Status tab of the configuration utility. See the Configuration Utility document for more information about this tab.
The MOVEit DMZ SSH server communicates with MOVEit DMZ using the Machine URL configured on this tab. See the Configuration Utility document for more information about this tab.
The encryption and hashing algorithms that the MOVEit DMZ SSH server uses can be configured on the SSH Ciphers Tab. (The encryption and hashing algorithms used by the MOVEit DMZ SSL servers - both HTTPS and FTPS - are also configurable.)
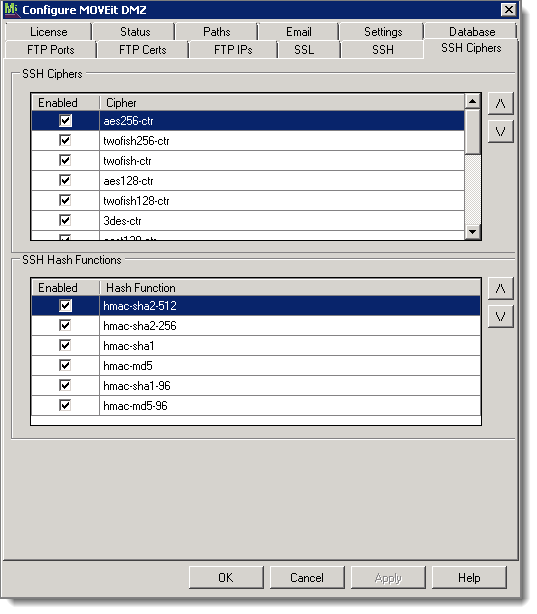
This tab lets you select the ciphers and hash functions used to secure the SSH connection.
For FIPS and PCI compliance, you may need to prevent the use of weak ciphers. For example, a PCI audit may flag the use of ciphers, such as MD5 and MD5-96. FIPS-approved cryptographic methods for SSH include (as of September 2015) 3des-cbc, aes128-cbc, aes192-cbc, and aes-256 ciphers with hmac-sha2-512, hmac-sha2-256, hmac-sha1, hmac-md5, hmac-sha1-96, and hmac-md5-96 as the approved hash functions.
Note: Both the client's and the server's preferences are taken into consideration when choosing the actual cipher and hash function for a given session. There must be a common cipher and hash function on both sides or there will be an error.
The SSH Ciphers section allows you to choose which ciphers are permissible, and their order of preference. By default, all ciphers are enabled.
Select the Enabled check box to disable a selected entry or to enable an unselected entry.
Entries closer to the top of the list are given preference over entries lower down. Use the arrow buttons to move entries up or down in the list. Even if you must permit weak ciphers or hashes, you should always put the stronger ones at the top of the list.
The SSH Hash Functions section allows you to choose which hash functions are permissible, and their order of preference. By default, all hash functions are enabled.
Select the Enabled check box to disable a selected entry or to enable an unselected entry.
Entries closer to the top of the list are given preference over entries lower down. Use the arrow buttons to move entries up or down in the list.
Certain clients may want to know which algorithms the MOVEit DMZ server supports, so this section provides a complete list.
Many SSH clients can also obtain this information from MOVEit DMZ just by connecting because the SSH protocol requires the server to list which modes it supports. In other words, there is no security reason to keep this information private.
MOVEit DMZ SSH server supports the following encryption algorithms.
MOVEit DMZ SSH server supports the following (keyed) hash algorithms.
MOVEit DMZ SSH server supports the following on-the-fly compression algorithms.