This topic describes options for setting and managing passwords (SETTINGS > Security Policies - Password).
The password requirements set here are displayed in the web interface where a user or administrator is asked to enter a password. For example, if the user is required to enter a password when sending a package, the password requirements are listed:
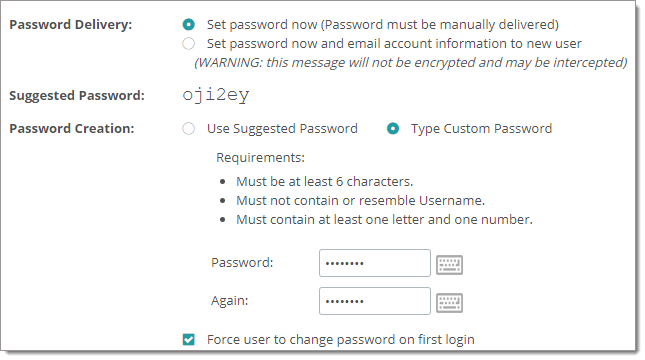
This section controls the minimum password complexity and length requirements for the MOVEit Transfer system.
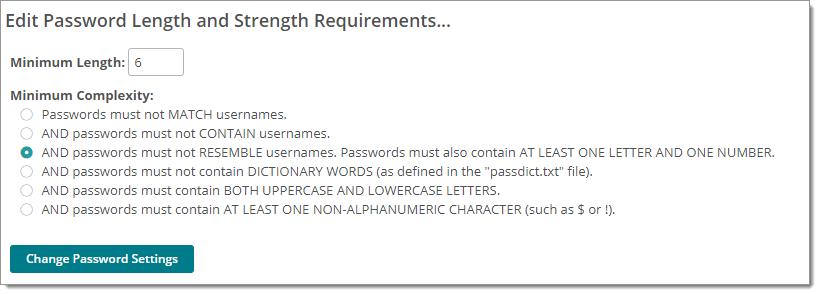
The passdict.txt file contains the full password dictionary. It is located in the d:\moveitdmz or similar folder. (It is not in "Program Files") This file is NOT encrypted and may be modified by any text editor.
MOVEit Transfer provides built-in controls for requiring regular or regular and frequent password changes and prevent the unsafe practice of password re-use. Using password aging and "history" (disallowing use of recently used password within the last n passwords used) are required pieces of all current cybersecurity standards.
Use these controls to set policies (rulesets) to regulate:
The workflow for using this feature requires you to create rulesets (policies) before you can apply them by user role.
![]() These password aging and history controls have no effect on external password sources and access control measures (such as the case where Single Sign-on is used).
These password aging and history controls have no effect on external password sources and access control measures (such as the case where Single Sign-on is used).
Define Password Aging Policies for Each Role of User in Your Organization
|
Control/Operation |
Notes |
|
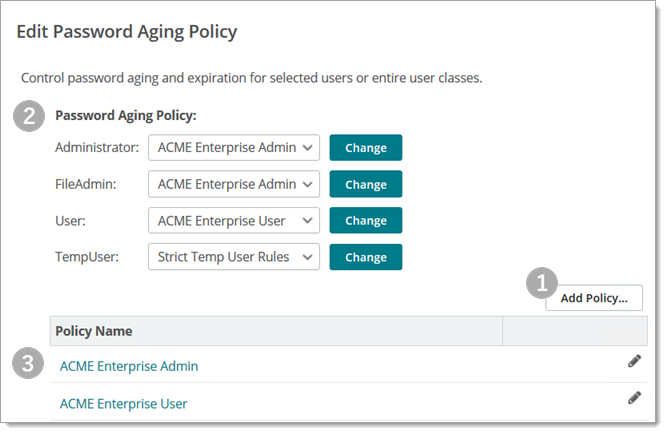
Add Policy. First, define a new set rules for password aging you can apply to a specific role of user. |
You must create a policy before you can apply policy rules that change the default (no policy applied) behavior. |
|
Password Aging Policy (select one from drop-down list). 1. Select a pre-defined policy for each user role in your organization. 2. Click Change to apply the policy you selected. |
Often times users with greater scope of access (such as administrators) are considered good candidates for shorter aging periods. (Greater access means greater risk and shorter periods of aging helps mitigate this risk.) |
|
Policy Name (table view). Browse, modify, or delete Password Aging Policies created with the Add Policy control. |
This table is initially blank until you create a policy. |
Define Password Aging Rules Using the Add/Edit Password Aging Policy View
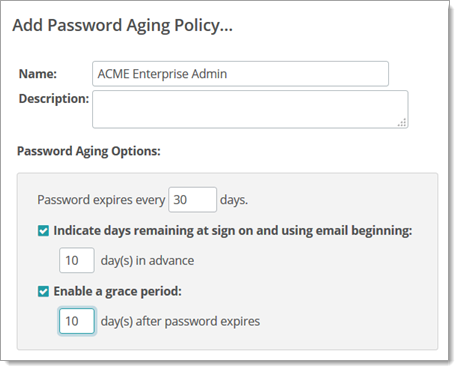
Password History. Allows Admins the ability to prevent users from reusing passwords. Default value is 0, and the maximum allowed value is 99. Password histories are built as people change their passwords. In other words password histories will not magically appear as soon as an Admin changes his history setting from 0 to 5.
Password Aging. Turns password aging on and off. If enabled, passwords will EXPIRE after the configured number of days. After a password has expired, the user will be locked out until an administrator can re-enable their account. A notification of the password expiration will also be sent to interested administrators and GroupAdmins. Default value is OFF.
Lock out user if password older than: Passwords older than this number of days EXPIRE and will cause their users to be locked out until an administrator can re-enable their account. Default value is 120 days, the minimum allowed value is 1, and the maximum allowed value is 9999.
Warn and force password change in advance. When enabled, MOVEit Transfer will EMAIL password expiration notices to the user in advance of their password becoming expired. An email notification will also be sent to interested administrators and GroupAdmins indicating that the user has been informed of the pending expiration of their password. Also, when a user's password is within the configured number of days, the user will automatically be forced to change their password the next time they sign on.
How many days in advance. Controls how many days in advance of the password becoming expired a warning will be sent. Also controls how many days in advance of the password becoming expired MOVEit Transfer will begin forcing the user to change their password the next time they sign on. Default value is 10 days, the minimum allowed value is 0, and the value must be less than or equal to the value for the Lock out if older than setting.
When changes to the password aging options are made, the system will check to see if any current users will have their passwords marked as Expired due to the new settings. If any such users are found, a second page will appear asking the administrator if they wish to reset those users' password change stamps to the current time. Doing so will not change the passwords of the users. Instead, it will merely change the internal timestamp associated with each user's password, preventing the passwords from being considered old. If this prompt is declined, affected users will have their passwords marked as Expired during the next nightly scheduled task run.
Org Administrators can control how passwords are delivered and if users can reset them without admin intervention.
This section determines which delivery method is available or preferred when administrators create other users.
![]() Important: Unless SMTPS (secure SMTP) is configured, passwords sent by email are sent in plain-text. For more information on setting up SMTPS, see the SMTP section of the System Configuration topic.
Important: Unless SMTPS (secure SMTP) is configured, passwords sent by email are sent in plain-text. For more information on setting up SMTPS, see the SMTP section of the System Configuration topic.
Allow Users to Change Own Password (while signed-on)
When checked, users will be able to change their own passwords. Otherwise, when you clear the checkbox, users will be prevented from changing their own passwords.
Default=checked (Enabled).
Allow End-Users to Reset Password
When checked (Enabled), users will be allowed to request a password change from the MOVEit Transfer sign-on screen. This allows users to reset their own passwords without having to task your site's technical support staff.
If Enabled individual users may still be denied password change requests by enabling the Prohibit user from requesting automatic password changes setting on the user's profile. See the Password section of the User Profile documentation for more details.
If a user clicks the Request password change link on the sign-on page, he will then be prompted to enter a username. An email address will be sent to that user account's registered email address—if there is one—with either a link to continue the password change request, or a notice that the request was denied. (The user will have a limited amount of time to click the link that brings them to a dialog that initiates the change password operation.) Password change request provides extra options for verifying identity:
When Failed Sign-on Attempts or Answers to Challenge Questions are Observed...
User reset is subject to policies of incorrect sign-on attempts even when using challenge questions. For example:
Note: The length of time a password change request link is active is determined by the Password request codes should expire after setting. Each password change request is issued a unique ID code that identifies it to the server. That ID code is provided in the link sent to the user's email address. If that ID code is not used within the time specified by this setting, it will expire and will no longer be able to be used to reset the user's password.