Manage and rotate org-specific keys (ORGS tab <org-or-system> - Security Information - Encryption Keys). The feature replaces the key used to initially encrypt your data and applies fresh encryption (on a per-org basis).
![]() You can use MOVEit Transfer Key Rotation as part of your key management plan to protect at-rest data against compromise and operational weakness.
You can use MOVEit Transfer Key Rotation as part of your key management plan to protect at-rest data against compromise and operational weakness.
As an extra measure of security, the rotate keys feature enables you to refresh the org passphrase (and the key derived from it) (on-demand or as scheduled) and re-encrypt your at-rest filestore. When the file re-encryption work completes with the new key, MOVEit Transfer notifies you by email.
Using the Key Rotation Dashboard, you can:
The Key Rotation feature guides you through steps needed to apply new encryption keys. It returns a time-to-completion summary to help you determine the best period to begin the re-encryption process. When the re-encryption work completes, MOVEit Transfer notifies you by email.
Key Rotation Guide (time-to-complete shown)
Note: Only SysAdmin-level users can view and manage MOVEit Transfer Organizations using the ORGS tab. For other user roles, this item is not available.
For an extra measure of security, you can rotate keys regularly or as site conditions require. The rotate keys feature enables you to refresh the passphrase and key derived from it, which is used to encrypt your at-rest filestore.
![]() This feature allows you to apply an extra measure of security by controlling the time interval between key/passphrase updates.
This feature allows you to apply an extra measure of security by controlling the time interval between key/passphrase updates.
You must be signed-on as SysAdmin to apply these settings.
Scope of Encryption... |
Location in WebUI... |
What's Encrypted... |
Any Licensed Organization |
ORGS > <org-name> - Security Information - Encryption Keys |
User and file information associated with a particular MOVEit Transfer Org |
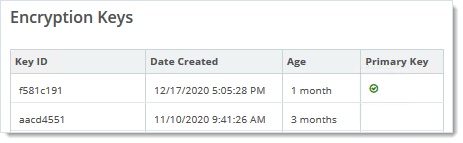
Encryption Key History is Available on the Org Key Management Page (Org encryption shown)
![]() Applying a new key means re-encrypting your shared files and filestore, which requires an increased CPU workload for the MOVEit Transfer server for the duration of the key rotation process. Ensure you use the estimation figures provided in the key rotation process and do not run during periods of peak demand.
Applying a new key means re-encrypting your shared files and filestore, which requires an increased CPU workload for the MOVEit Transfer server for the duration of the key rotation process. Ensure you use the estimation figures provided in the key rotation process and do not run during periods of peak demand.
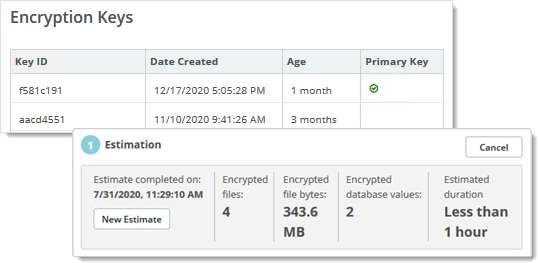
Encryption Key Rotation Begins with a Time Estimate
|
You can pause key rotation while it is in-process and resume later when it is more convenient. For example, the host system where MOVEit Transfer is running will use more than its typical share of CPU resources while a key conversion progresses. So, this feature allows you to pause processing during, let's say, a peak download period and then resume once the busy period is over to ensure your users do not perceive system latency. (You can also use the schedule feature for this purpose.)
Pause and Resume
|
If you can reliably predict periods when your MOVEit Transfer system will be busiest, you can use the Key Rotation Schedule feature to assign a non-peak period to re-encrypt files.
Rotate Periodically or Schedule for Non-Peak Hours
|
|
As a SysAdmin, you can refresh the encryption seed or "key" used to convert MOVEit Transfer system and org-specific data files to a freshly encrypted file store.
Note: For clustered installations commonly referred to as MOVEit Transfer Web Farms, sign-on to the node you typically use for administrative control of your MOVEit Transfer deployment. After launch, key conversion will be controlled only from this node. For more information, see the section titled Web Farm Notes.
The table that follows breaks down the steps needed to apply new encryption keys to your org-specific or system-org data.
Step |
Action... |
Description |
1. |
Click Begin Key Rotation Process |
Open a on-line guide that estimates the time it will take to complete re-encryption of your org data using the new key. |
2. |
Estimation |
Review the estimate. Next you can click:
|
3. |
Create Passphrase |
Click Continue to accept the estimate and apply a passphrase.
|
4. |
Click Start Now to re-encrypt your data using the new passphrase. —or— Edit/Enable Schedule |
Run now (you can pause at any time) —or— Select and schedule periods when increased CPU utilization associated with re-encryption and key conversion is optimal. |
5. |
Wait for notification. |
Completion notification will be sent to you by way of your SysAdmin configured email. |
|
What's Next... |
|
This process enables you to estimate and refresh your orgs at-rest data encryption.
![]() If you have a large filestore to re-encrypt, it is best to schedule or perform your key rotation and encryption refresh either during maintenance period or operational period when the least user traffic tends to be observed.
If you have a large filestore to re-encrypt, it is best to schedule or perform your key rotation and encryption refresh either during maintenance period or operational period when the least user traffic tends to be observed.
MOVEit Transfer returns a time estimate and summary of how much data and how many files will be affected. You can run this step multiple times.
![]() Your passcode is a master key and used to derive your encryption key. Make sure you write it down and safeguard it.
Your passcode is a master key and used to derive your encryption key. Make sure you write it down and safeguard it.
During production operations the encryption performance demands on the MOVEit Transfer server are naturally low relative to CPU performance. In other words, items you add to the filestore are encrypted in an on-demand fashion. However, when you re-encrypt a MOVEit Transfer filestore that has been built up with hundreds or thousands of files over time, this large-volume, batched encryption increases CPU workload, possibly for several or more hours. You can mitigate the perceived latency of the system through appropriate scheduling, scale-out, and by notifying your users who might perceive latency when interacting with MOVEit Transfer.
MOVEit Transfer Web Farm at-rest key rotation works similar to single node key management.
There are a few main differences: