IN THIS PAGE
2022.0 (8.8.0) Dec 6, 2022
2022.0.1 (8.8.1) March 14, 2023 (updated)
2022.0.2 (8.8.2) Sept 27, 2023 (updated)
2022.0.3 (8.8.3) Oct 3, 2023 (updated)
2022.0.4 (8.8.4) Nov 7, 2023 (updated)
2022.0.5 (8.8.5) Feb 20, 2024 (updated)
2022.0.6 (8.8.6) March 7, 2024 (updated)
2022.0.7 (8.8.7) May 24, 2024 (updated)
2022.0.8 (8.8.8) August 27, 2024 (updated)
2022.0.8 (8.8.9) November 6, 2024 (updated)
What's New in WS_FTP Server 2022.0.5 (8.8.5)
The following new features and improvements were added to WS_FTP Server 2022.0.5 (8.8.5).
SHA2 host key algorithm support
WS_FTP Server now supports SHA-2 when when creating a TLS certificate. SHA-2 is the default selection.
What's New in WS_FTP Server 2022.0.2 (8.8.2)
The following new features and improvements were added to WS_FTP Server 2022.0.2 (8.8.2).
OpenSSL update
OpenSSL was upgraded to version v1.0.2zh to incorporate security fixes and prevent potential vulnerabilities. For more information, see https://www.openssl.org/news/vulnerabilities-1.0.2.html.
What's New in WS_FTP Server 2022.0 (8.8)
The following new features and improvements were added to WS_FTP Server 2022.0 (8.8).
Multi-factor authentication
Multi-factor authentication protects Web Transfer Client user's accounts from unverified users when a user's account password is lost, stolen, or compromised. To verify user identity, WS_FTP Server gives Web Transfer Client users private access to a uniquely-generated verification code made available to the user by mobile app. This additional verification step ensures user sign in is genuine.
This feature includes:
- Admin-level UI controls that enable administrators to implement multi-factor authentication.
- Online guide/wizard that guides end-users through the app verification and setup needed for multi-factor authentication.
- UI controls that enable administrator to require multi-factor authentication for selected user classes.
- UI controls that enable administrators to exempt specific users.
- Users can optionally 'opt in' to use multi-factor authentication when it is not an enforced requirement.
- User identity verification using a mobile authenticator app.
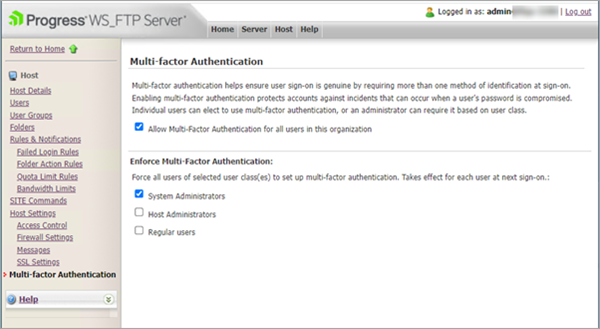
For more information, see WS_FTP Server Multi-Factor Authentication and Web Transfer Client Multi-Factor Authentication.
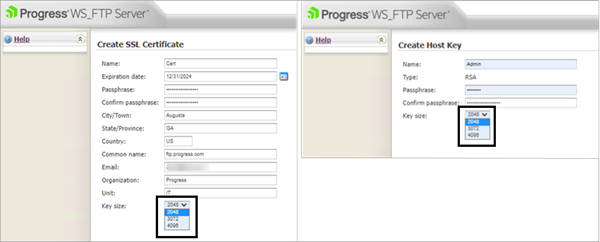
SSL certificate and SSH host key size updates
To improve secure certificate creation, the minimum key size for SSL certificate and SSH host key creation was increased from 1024 to 2048 bit. WS_FTP Server users can also choose 3072 or 4096 bit.
Upgrades to the latest version will not affect existing keys of sizes smaller than 2048 bit.
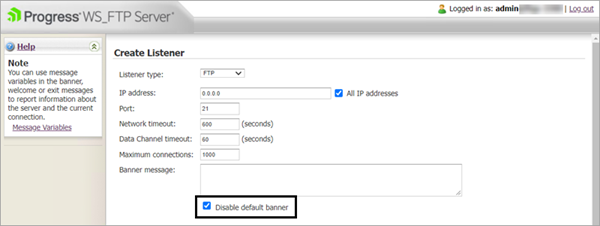
Disable default banner update
The default banner is disabled by default. This prevents identifying information about the server being displayed. WS_FTP Server user can opt to enable the banner. For more information, see Creating Listeners.
WS_FTP Web Server support deprecation
WS_FTP Web Server is no longer supported. For information about migrating WS_FTP Server Manager to IIS, see How to migrate the WS_FTP Server Manager to IIS.
SFTP transfer performance improvement
Updates to WS_FTP Server resulted in significant improvements to SFTP upload speeds.
Listener encryption settings (SSH) updates
WS_FTP SFTP Server now supports advanced public host key algorithms RSA-SHA-2 256 and RSA-SHA-2 512.
Less secure ciphers, MACs, and key exchange algorithms are disabled by default on new installations. When new listeners are created, the updated standards are enforced. The listener exchange settings are unchanged on upgrades to the latest version.
The following encryption settings are disabled by default:
- Cipher - 3des.cbc, blowfish.cbc, and cast128.cbc
- MAC - hmac-md5 and hmac-md5-96
- Key Exchange Algorithm - Diffie-hellman-group1-sha1
If required, you can re-enable the encryption settings from the Listener Encryption Settings page.
SSH user key authentication update
The Require multi-factor authentication check box for users was renamed Require password and SSH user key to ensure clarity. For more information, see Configuring password and SSH user key authentication.
Microsoft SQL Server support
WS_FTP Server 2022.0 supports Microsoft SQL Server 2019 Enterprise/Standard
Windows Server 2022 support
WS_FTP Server 2022.0 supports deployment to the Windows Server 2022 operating system.
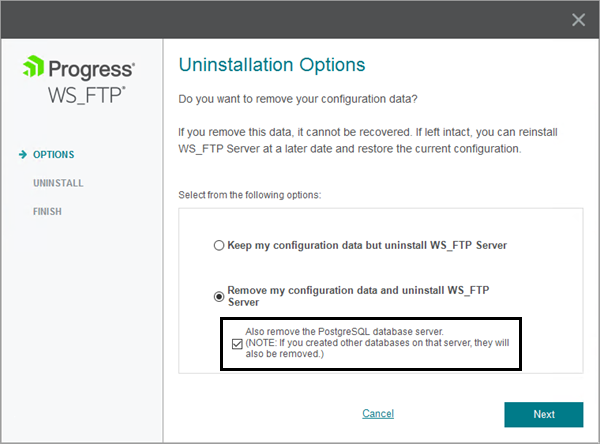
Updated uninstall option
If you choose to uninstall WS_FTP Server and remove your configuration data during the uninstall process, you can optionally choose to remove the PostgreSQL database server.
OpenSSL update
OpenSSL was upgraded from 1.0.2u to 1.0.2zf to incorporate security fixes and prevent potential vulnerabilities. For more information, see https://www.openssl.org/news/vulnerabilities-1.0.2.html.
Fixed Issues in 2022.0 (8.8)
The following issues were fixed in WS_FTP Server 2022.0 (8.8).
ID |
Category |
Fixed Issue |
|---|---|---|
12244 |
Database |
Fixed an issue which caused an error connecting to SSH/FTP after database migration from PostgreSQL to MSSQL. |
12769 |
Web Transfer Module |
Web Transfer Module now successfully opens as part of application pool creation. |
6315, 6332, 12240, 15175, 15178, 15179, 15184, 15185 |
Server, Security |
Addressed Cross-Site Request Forgery (CSRF) issues in WS_FTP Server Administrative interface. |
15168, 15181, 15182, 15183, 15186, 15187, 15188 |
Server, Security |
Addressed cross-site scripting (XSS) issues in WS_FTP Server Administrative interface. |
6160 |
Server, Security |
The Use Local Time option is respected. |
6293 |
Server, Database |
Fixed an issue which caused an error connecting to SSH/FTP after database migration from PostgreSQL to MSSQL. |
6351 |
Server, Web Admin |
Text generates correctly when logging in to WS_FTP Server. |
12345 |
Server, Installer |
The installer retains the given location of PostgreSQL. |
12548 |
Server, WTM |
A users full name is displayed when assigning user rights in Web Transfer Module. |
12751 |
Server, Security |
The default cipher sorting is strongest to weakest. |
12773 |
WTM, AHT |
The bootstrap.js dependency was updated to prevent a security vulnerability. |
15122 |
Server |
New and updated encryption algorithms ensures improved security. |
15151 |
WTM, AHT |
The Moment.js dependency was updated to prevent a security vulnerability. |
15152 |
WTM, AHT |
The Loadash dependency was updated to prevent a security vulnerability. |
15166 |
Server, SSH |
Version details are not disclosed in the banner information. |
15170 |
Server, Web Admin |
The assigned level of user permissions is respected. |
15260 |
Server, Security |
Addressed Cross-Site Request Forgery (CSRF) issues in WS_FTP Server Administrative interface. |
19457 |
Installer |
WS_FTP Server successfully installs following uninstalling the application with the Keep Configuration Data option selected. |
15361 |
Server, Database |
The PostgreSQL database was updated to 14.5. This update addressed CVE-2022-2625 and prevented other security vulnerabilities. |
Fixed Issues in 2022.0.1 (8.8.1)
The following issues were fixed in WS_FTP Server 2022.0.1 (8.8.1)
ID |
Category |
Fixed Issue |
|---|---|---|
19449 |
SSH Server |
Sub-sessions opened through a single parent connection now close properly on the session manager respecting the network timeout. |
19501 |
Multi-factor authentication |
Users added using |
19530 |
Multi-factor authentication |
Users synchronized from the Active Directory, LDAP, Windows, or ODBC Database have the correct settings. |
19539 |
Installer |
The UI was updated to display the correct title during the uninstall process. |
19613 |
Installer |
The WS_FTP Server Installation Guide is linked from the installation welcome screen. |
19643 |
Installer |
Uninstall options were updated to add Delete the database, which removes the PostgreSQL database in upgrade scenarios. |
19575 |
Security |
Updated Zlib library to version 1.2.13 to prevent CVE-2022-37434. |
Fixed Issues in 2022.0.2 (8.8.2)
The following issues were fixed in WS_FTP Server 2022.0.2 (8.8.2)
ID |
Category |
Fixed Issue |
|---|---|---|
6040 |
Server, Database |
WS_FTP Server does not deadlock external-facing databases when updating last login. |
15121, 15169 |
WTM, Security |
Updates were applied to WS_FTP Server to prevent a potential cross-site scripting (XSS) vulnerability (CVE-2022-27665). |
19677 |
Web Admin, Security |
To protect against Cross-Site-Request-Forgery (CSRF) attacks, CSRF tokens were added to multiple pages. |
19678 |
Web Admin, Security |
A potential cross-site scripting (XSS) vulnerability was fixed. |
19679 |
Web Admin, Security |
The directory view is inaccessible in both authenticated and unauthenticated states. |
19686 |
AHT, Security |
Addressed a padded oracle vulnerability to prevent a potential cross-site scripting (XSS) attack. |
20729 |
Web Admin, Server, Security |
Updates were applied to dependencies to prevent potential SQL injection attacks. |
20742 |
Web Admin, Security |
Updates were applied to WS_FTP Server Manager to prevent potential Cross-Site-Request-Forgery (CSRF) attacks, |
20785 |
Server, SSH |
Updates to SSH listeners on one port are not replicated on SSH listeners on a separate port. |
20787 |
Server, DBConfig |
Default SSH host keys and SSL certificates are maintained and new keys and certs are successfully created when DBConfig is run. |
21458 |
Database, Server |
The SQL server database version history table is updated correctly during upgrades. |
21541 |
AHT Security |
Deserialization of untrusted data does not occur, ensuring that pre-authentication command execution is not permissible (CVE-2023-40044). |
21576 |
SFTP |
Directory traversal is prevented in SFTP file rename commands (CVE-2023-42657). |
21591, 12867 |
Web Transfer Module |
Directory traversal is prevented in Web Transfer Module file delete feature. |
21593, 21604, 21605 |
SSH Server |
Directory traversal is prevented in SFTP file remove, directory remove, and directory make commands. |
Fixed Issues in 2022.0.3 (8.8.3)
The following issues were fixed in WS_FTP Server 2022.0.3 (8.8.3).
ID |
Category |
Fixed Issue |
|---|---|---|
21642 |
SSH, SFTP |
SFTP operations complete successfully for regular users with home folder as root. |
Fixed Issues in 2022.0.4 (8.8.4)
The following issues were fixed in WS_FTP Server 2022.0.4 (8.8.4).
ID |
Category |
Fixed Issue |
|---|---|---|
21752 |
Server |
Updates were applied to WS_FTP Server to prevent potential path injection attacks. |
Fixed Issues in 2022.0.5 (8.8.5)
The following issues were fixed in WS_FTP Server 2022.0.5 (8.8.5).
ID |
Category |
Fixed Issue |
|---|---|---|
6104 |
WTM, AHT, SFTP, FTP |
Triggered rule behavior is now consistent across all transfer methods. |
21497 |
DB Config, Server |
Connection strings are successfully updated when migrating from PostgreSQL. WS_FTP Server uses the migrated MSSQL DB. |
21824 |
WTM, AHT, SFTP, FTP |
The loading time for directory listings was improved when there are lots of notification rules configured. |
22124 |
SSH |
SSH keys are successfully imported when the default locale is Japanese. |
20741 |
Security |
CVE-2024-1474: Addressed multiple cross-site scripting (XSS) issues on the WS_FTP Server administrative interface. |
22082 |
Security |
The PostgreSQL version was updated to 14.10 to prevent potential security vulnerabilities. |
Fixed Issues in 2022.0.6 (8.8.6)
The following issues were fixed in WS_FTP Server 2022.0.6 (8.8.6).
ID |
Category |
Fixed Issue |
|---|---|---|
22183 |
WTM, SFTP, FTP(S) |
Folder action rules replace notification variables with the correct values. |
22184 |
WTM, SFTP, FTP(S) |
Service stops when invalid characters are present in a home folder name. |
Fixed Issues in 2022.0.7 (8.8.7)
The following issues were fixed in WS_FTP Server 2022.0.7 (8.8.7).
ID |
Category |
Fixed Issue |
|---|---|---|
5944 |
Server, iftpaddh |
Hosts created by |
17431 |
SSH key |
If a specific SSH key is selected, the selected key choice persists after an upgrade or repair. |
21448 |
AHT, Web Admin, WTM, Security |
The |
21559 |
Server, Web Admin |
The server web UI works correctly when logging into both server web interface and WTM. |
21985 |
Server |
If a new log location is set, the new location persists after an upgrade. |
21986 |
Server |
If a MAC is removed, it remains removed from the list after an upgrade. |
21987 |
AHT, Web Admin, WTM, Security |
Dependencies and attributes were updated to prevent potential Cross-Site Request Forgery (CSRF) attacks. |
22011 |
AHT, WTM, Security |
The cookie path attribute was updated. |
22217 |
Web Admin |
Incorrect "Potential CSRF Attack" error removed when an invalid token is encountered. |
22230 |
Web Admin |
The Host Details Top folder field correctly displays the folder path with two backslashes "\\". |
22247 |
Server |
The SFTP server does not hang after multiple user log ons from LDAP. |
22260, 22343 |
Web Admin |
The Web Admin correctly displays dates independently of the system locale settings. |
22279 |
SFTP |
The server does not crash when refreshing the list of rules. |
6235 |
Security |
To protect against potential Cross-Site-Scripting (XSS) attacks, the HttpOnly attribute was added. |
Fixed Issues in 2022.0.8 (8.8.8)
The following issues were fixed in WS_FTP Server 2022.0.8 (8.8.8).
ID |
Category |
Fixed Issue |
|---|---|---|
6133 |
Database, Users |
Duplicate users are not created when a user logs in with same username but with a different case. |
22217 |
Server |
An incorrect error message was removed. |
22504 |
Installer |
Updated Ad Hoc impersonation settings are saved and maintained during upgrades. |
22544 |
Server |
The List all folders in /users folder options function as expected. |
22772 |
Server |
The folder action rules run the executable part of the rule when managing files with the Web Transfer Module. |
22919 |
Logging Server |
WS_FTP Server log files can exceed 2GB. |
22768 |
Security, Web Transfer Module |
Path traversal attempts return an error. Fixes CVE-2024-7744. |
22711, 22712 |
Security, Web Transfer Module |
Multi-factor authentication was updated to address CVE-2024-7745. |
23040 |
Security, PostgreSQL |
PostgreSQL was updated to version 15.8 to address CVE-2024-7348. |
6259 |
Ad Hoc Transfer Module |
Usernames are correctly stored in the Ad Hoc Transfer Module. |
Fixed Issues in 2022.0.9 (8.8.9)
The following issues were fixed in WS_FTP Server 2022.0.9 (8.8.9).
ID |
Category |
Fixed Issue |
|---|---|---|
25279 |
Server |
The correct order of tables are created during migration from PostgreSQL to MS SQL database using |
25317 |
Web Transfer Module |
If a user's web transfer module password expires, they can log on but must change their password to continue. |
25263 |
Web Transfer Module |
To reset two-factor authentication (2FA) or perform any operations, you must log on with a valid 2FA code. |
Known Issues in 2022.0 (8.8)
This section details known issues and workarounds in all WS_FTP Server 2022.0.0 (8.8.0) releases.
ID |
Category |
Known Issue Description |
|---|---|---|
19501, 19530 |
Multi-factor authentication |
Multi-factor authentication (MFA) is disabled by default for users added using iftpaddu.exe, ftpdbsyc.exe, or the synchronize option through admin. To enable MFA for these users, resave the MFA configuration in WS_FTP Server Manager. |
19501 |
Multi-factor authentication |
Users added using the user command line utility |
19525 |
Command line utility |
Using the database backup command line utilities to generate backup files returns an error To resolve this issue, remove the |
Known Issues in 2022.0.1 (8.8.1)
This section details known issues and workarounds in all WS_FTP Server 2022.0.1 (8.8.1) releases.
ID |
Category |
Known Issue Description |
|---|---|---|
19525 |
Command line utility |
Using the database backup command line utilities to generate backup files returns an error To resolve this issue, remove the |
System Requirements
These requirements apply to the supporting environment and operating system where you install WS_FTP Server.
Software Requirements
Supported Operating Systems for WS_FTP Server
The Operating Systems are supported for the following WS_FTP Server configurations:
- Standalone
- Failover cluster using Microsoft Clustering Services
- Failover cluster using Microsoft Network Load Balancing
Operating System
- Windows Server 2022 Standard/Datacenter (standalone only)
- Windows Server 2019 Standard/Datacenter (standalone only)
- Windows Server 2016 Standard/Datacenter (standalone only)
Windows Server Components Activated Automatically
The WS_FTP Server installer automatically activates certain components in your Windows Server installation. This is necessary because after installation Windows Server does not turn on non-core operating system components. However, before installing WS_FTP Server, you should ensure these changes conform to your organization’s security policies.
When you install WS_FTP Server, the install activates the following Windows Server roles:
- ISAPI Extensions
- Windows Authentication
- ASP
Supported Web Browsers
The following browsers are supported for WS_FTP Server Manager and the Web Transfer and Ad-Hoc Transfer client interfaces:
- Chrome
- Mozilla Firefox
- Microsoft Edge
Database Platform
WS_FTP Server requires one of the following database platforms.
The default database platform is PostgreSQL, however during installation, you can select Microsoft SQL Server as your database for configuration data.
- PostgreSQL 15.8 (WS_FTP Server 2022.0.8 (8.8.8), or later)
- PostgreSQL 14.10
- Microsoft SQL Server 2019 Enterprise/Standard
- Microsoft SQL Server 2017 Enterprise/Standard
- Microsoft SQL Server 2016 Enterprise/Standard
Framework and Accessibility
WS_FTP Server requires the Microsoft .NET Framework and other Microsoft packages for scripting and software accessibility. Microsoft .NET Framework 4.8 is included in the installation program.
Hardware
Minimum requirements
- 4-core server-class CPU (For example: Intel Xeon 4-core 2+GHz)
- 4 GB RAM
- 250 GB or larger free disk space, depending on estimated data to be stored
- 100/1000 MB Ethernet interface (for TCP/IP traffic)
Ad Hoc Transfer Plug-in Requirements
The following software must be installed on the machine on which you install the Ad Hoc Transfer Plug-in for Outlook.
- Microsoft Outlook 2016, 2013, or 2010
- Supported on Windows Operating Systems only.
Note: If you are running the installer live (not doing a silent install), the installer automatically installs the Microsoft Visual Studio redistributable programs. You do not need to download anything from Microsoft. If running a silent install, you must download and install these redistributable programs before running the install. See the Requirements in the Silent Install section.
Note: For silent installation instructions for the Ad Hoc Transfer Plug-in for Outlook, see Silent install of the Ad Hoc Transfer Plug-in for Outlook .
Upgrading
Upgrading to the latest version of WS_FTP Server ensures that you have access to the latest features, fixes, security updates, and usability improvements.
WS_FTP Server 2022 (8.8) supports direct upgrades from WS_FTP Server 2020 (8.7). For more information, see Upgrade Paths.
Upgrading information and considerations
Latest features and improvements
For the most up-to-date information about the latest supported features and improvements, see What's New.
Hardware Requirements
Review the current WS_FTP Server System Requirements.
Activation code
The activation code is automatically applied when you run the WS_FTP Server installer to upgrade.
- Your upgrade activation code is embedded in the installer file.
- The activation code is also stored in the Product Downloads section of the Progress Community.
- The activation code differs from your serial number. The code begins with your serial number and contains an additional eight characters.
WS_FTP Web Server support deprecation
WS_FTP Web Server is no longer supported. For information about migrating WS_FTP Server Manager to IIS, see How to migrate the WS_FTP Server Manager to IIS.
Support for older WS_FTP Server Versions
For information about support for previous versions of WS_FTP Server, see the Product Lifecycle page on the Progress Community website. Customers running EOL or soon to be EOL versions should upgrade to WS_FTP Server 2022 (8.8).
Upgrade Paths
To upgrade from an earlier version of WS_FTP Server to WS_FTP Server 2022 (8.8), you must download the installer file.
- Login to the Progress Community.
- Select Product Downloads.
- Locate and download your product. Your activation code is embedded in the download file, and is automatically applied during installation.
Note: WS_FTP Web Server is no longer supported. To upgrade from an earlier version of WS_FTP Server Manager on WS_FTP Web Server, you must first migrate WS_FTP Server Manager to IIS. For information about migrating WS_FTP Server Manager to IIS, see How to migrate the WS_FTP Server Manager to IIS.
Upgrade paths
WS_FTP Server 2022 (8.8) supports direct upgrade installations from the following version:
- WS_FTP Server 2020 (8.7)
Note: The upgrade paths are valid only on supported Operating Systems. For more information, see WS_FTP Server System Requirements.
For detailed installation and configuration instructions, or activating a new or upgraded license, see the WS_FTP Server Installation and Configuration Guide.
Note: If you upgrade from a version earlier than 2020, the default installation folders do not change. For example, the WS_FTP Server installation folder will be C:\Program Files (x86)\Ipswitch\WS_FTP Server.
Licensees and Evaluators
Read the end user license agreement (EULA) before installing or using this product: Progress End User License Agreement.
Copyright Notice
Visit the following page online to see Progress Software Corporation’s current Product Documentation Copyright Notice/Trademark Legend: Product Documentation Copyright Notice & Trademarks | Progress
DEC
06
2022